Quishing: a formidable phishing technique
Quishing, also known as QR code phishing, is a cyberattack tactic that leverages QR codes to steer users towards malicious websites.
QR codes have experienced remarkable growth in recent years. They were widely adopted during the pandemic for health pass monitoring, and have gradually become integrated into all aspects of our daily lives.
They can be found everywhere, from pharmacies, museums and restaurants to flyers and even television. QR codes are also being used to simplify financial transactions.
When the code is scanned, it can redirect the user to a fraudulent website to install malware on the victim’s device or steal personal information such as login details, credit card numbers, etc.
How Quishing works
Quishing involves 3 key steps.
1. Creating the fraudulent QR code
Hackers generate a malicious QR code that redirects to a website designed to deceive the user.
This website may imitate perfectly a legitimate site, such as that of a bank, government agency, airline or delivery service. The aim is to create a feeling of trust and encourage the user to enter personal information without hesitation.
2. QR code distribution
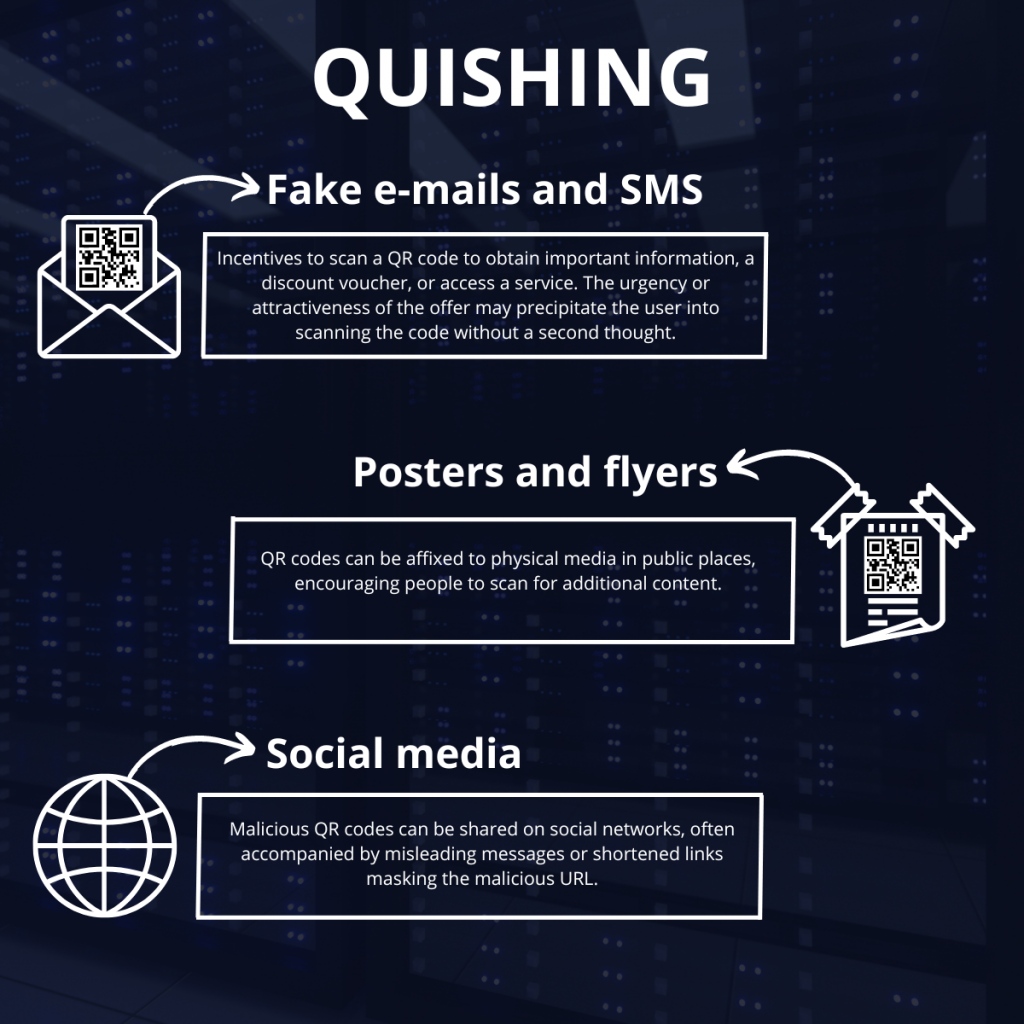
The fraudulent QR code can be distributed through a variety of channels, making the threat difficult to detect and counter:
False e-mails and SMS
Incentives to scan a QR code to obtain important information, a discount voucher, or access a service. The urgency or attractiveness of the offer may precipitate the user into scanning the code without a second thought.
Concrete examples
- An email appearing to come from an airline company offers a discount voucher for an upcoming trip. The embedded QR code redirects to a fraudulent website that asks the user to enter personal information to “claim” the voucher.
- An SMS claiming to be from a government agency invites the user to scan a QR code to “access an important service related to the current health situation”. The code redirects to a website that steals the user’s personal data.
Posters and flyers
QR codes can be affixed to physical media in public places, encouraging people to scan for additional content.
Concrete examples
- A QR code on a poster in a café promises access to an online menu. The code has been hacked and redirects to a website that steals customers’ bank details.
- A QR code on a flyer advertising a new product offers to download an informative brochure. The code redirects to a website that installs malware on the user’s device.
Social media
Malicious QR codes can be shared on Facebook, Twitter, Instagram, TikTok, and are often accompanied by misleading messages or shortened links masking the malicious URL.
Concrete examples
- An influencer shares a QR code on Instagram claiming it gives access to an exclusive contest. The code redirects to a website that asks the user to enter personal information to participate.
- A tweet encourages users to scan a QR code to “discover a fun video”. The code redirects to a website that broadcasts a fake video and attempts to download malware onto the user’s device.
In addition to these examples, fraudulent QR codes can also be found on:
- Parking tickets
- Charging stations for electric vehicles
- Cash dispensers
- Food packaging
- Invitations to events
3. Attack on the user
- Once the user scans the QR code, he or she is redirected to the fraudulent website.
- This website may use various techniques to trick the user into entering personal information:
- Login forms: The website imitates the login page of a legitimate service and asks the user to enter his/her credentials.
- Fake administrative forms: The website pretends to be an official site and asks the user to provide personal information to “verify identity” or to “benefit from a service”.
- Downloading malware: The website prompts the user to download a file which, once installed, infects their device and allows hackers to steal their data.
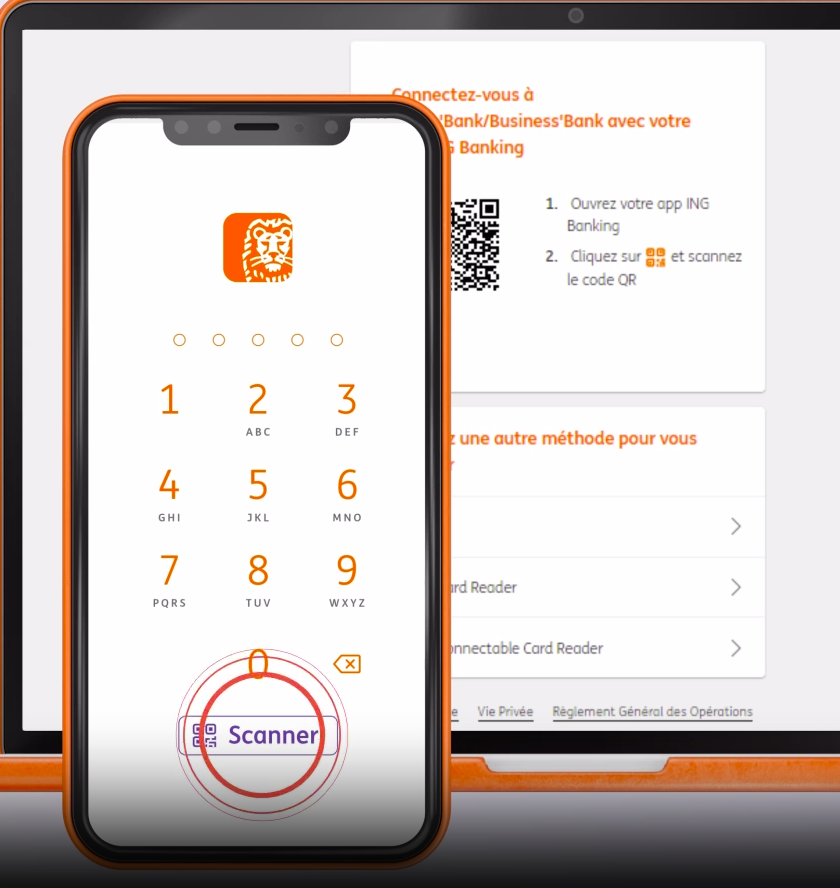
Example ING Bank
The case of ING Bank is considered one of the best-known cases of quishing. Hackers managed to hijack authentication QR codes intended for ING bank customers.
These codes are usually used by customers to access their account as a secure method. The crooks succeeded in obtaining these QR codes and were thus able to access customers’ bank accounts, resulting in significant financial losses, up to thousands of euros.
Vincent Biret, CEO of Unitag, one of the leading QR code platforms, confirmed that this type of hacking is rare and highly complex, but nevertheless possible.
Protecting yourself from Quishing
There are several ways to protect yourself against phishing. Quishing can be difficult to detect.
According to Lieutenant Eddy Rouf, head of the prevention and protection office of the Unité nationale Cyber (UNCyber), there are over 800 criminal proceedings underway involving QR codes, most of which are classified as scams. To this end, the cyber gendarmes are running an anti-quishing prevention campaign to alert the public to this new scam risk.
Tips to protect yourself against Quishing
To counter this threat, we strongly recommend applying the rules of Vigilance, Verification, Protection and Awareness.
1. Vigilance
- Never scan a QR code from an unknown source, even if the offer seems attractive.
- Be wary of QR codes in public places or on unofficial media.
2. Check
- Make sure that the URL of the website to which you are being redirected begins with “https://” and that a closed padlock is present in the address bar.
- Hover over the URL before clicking on it. The link displayed may not correspond to the real URL.
3. Protection tools
- Use antivirus and firewall software to protect against malware and phishing attacks.
- Install a security application to scan QR codes and detect fraudulent codes.
4. Awareness
- Inform those around you about the dangers of quishing, and let them know how to protect themselves.
Obviously, these are just a few of the many measures available, and the best advice is to be vigilant. Indeed, as the saying goes: “prudence is the mother of safety”.
Awareness campaigns for companies
Quishing and phishing awareness campaigns are available for companies and professionals.
A corporate phishing and quishing awareness campaign aims to educate employees to recognize fraudulent QR codes and emails, preventing information leakage and protecting the company from cyber-attacks.
