Cyberattacks in the health and medico-social sectors in France in 2023
Each year, the Digital Health Agency, or ANS, in collaboration with the Ministry of Health and Prevention as well as the CERT Santé, publishes a report on security incidents of information systems for the health and medico-social.
Every month, we hear in the news of a cyberattack orchestrated against a health structure, whether it is a private establishment, such as a radiology center, or a public one such as university hospitals.
On April 16, 2024, the Simone Veil hospital in Cannes was the victim of a ransomware cyberattack. This attack resulted in the encryption of data in the hospital’s computer system, rendering many essential services, such as medical records, the drug prescription system and the radiology system, unavailable. The Lockbit hacker group is responsible for this intrusion and data theft.
Incidents similar to that at the Simone Veil hospital in Cannes happen frequently. Each year, the Digital Health Agency, or ANS, in collaboration with the Ministry of Health and Prevention as well as the CERT Santé, publishes a report on security incidents of information systems for the health and medico-social.
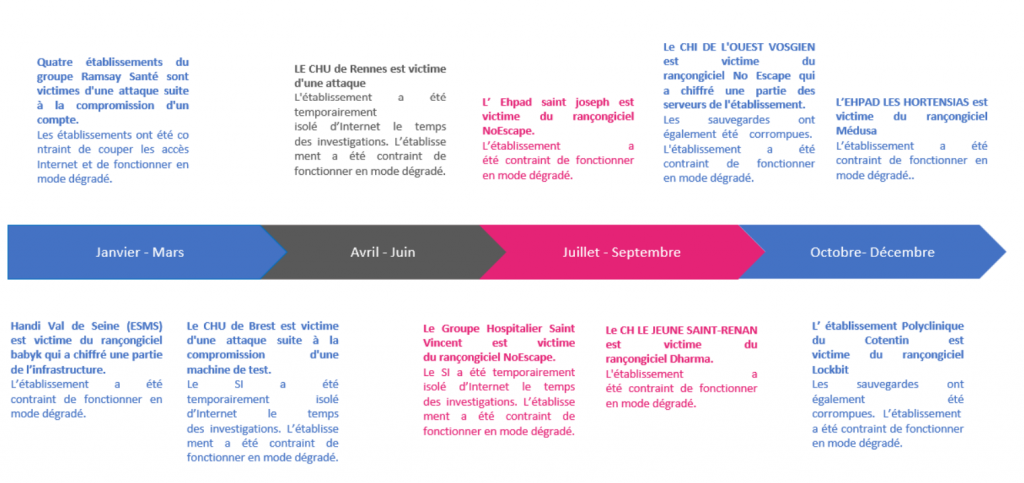
Healthcare facilities – a key target of cyberattacks
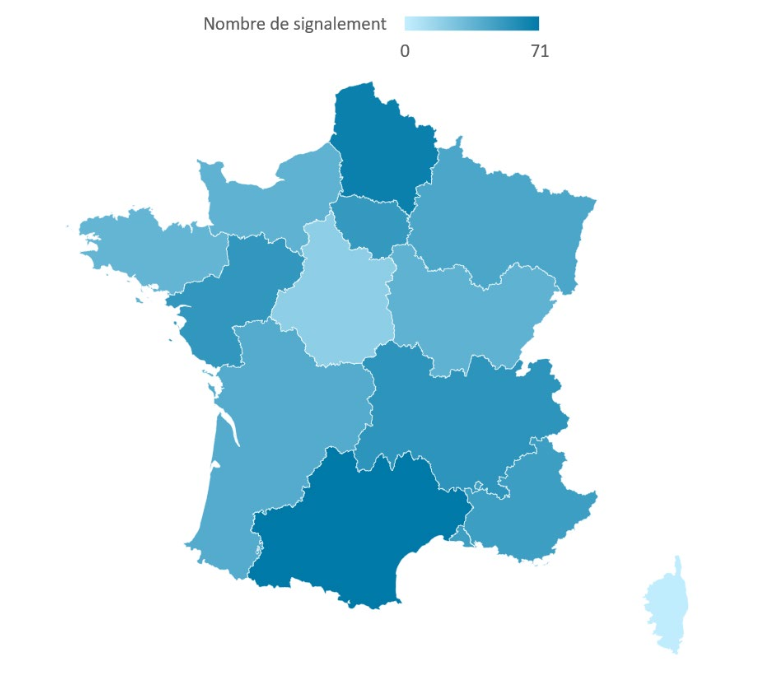
581 incidents were reported in 2023. This number is down slightly from 2022, which was 592. In 2021, the number of reported incidents was 733.

The regions with the highest number of reports are:
- Occitanie with 71 reports,
- Hauts-de-France (67),
- Auvergne-Rhône-Alpes (55).
These three regions alone represent more than 33% of the total reports.
Confidential patient data, stored en masse in healthcare establishments, makes them prime prey for cybercriminals. The poor cybersecurity of these structures further accentuates their vulnerability.
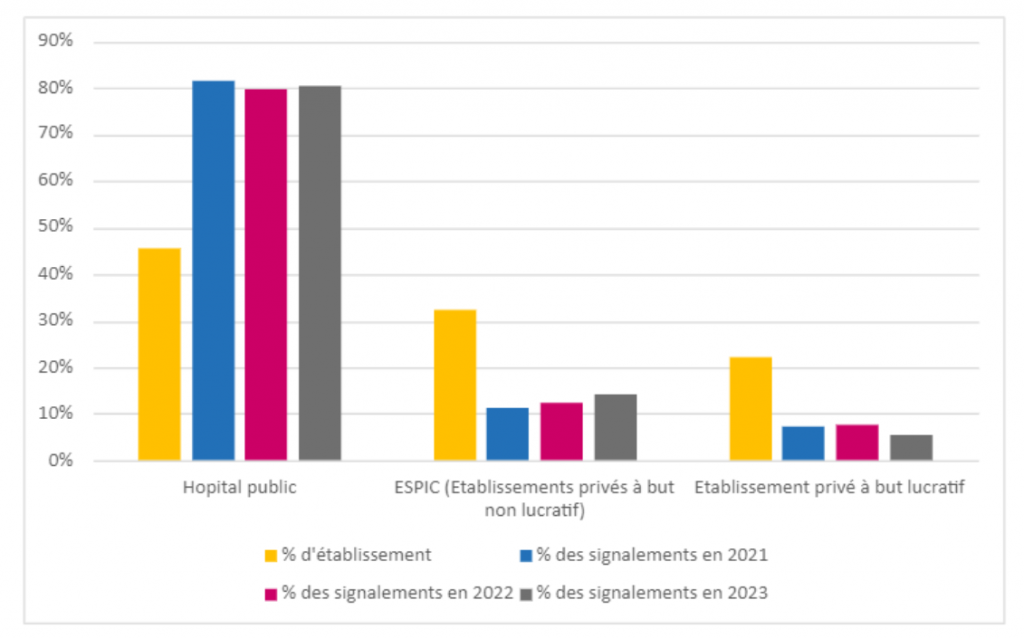
A large proportion of incidents in these health establishments affect the public sector. In 2023, 80% of these establishments having reported an incident are public hospitals.
Types of incidents
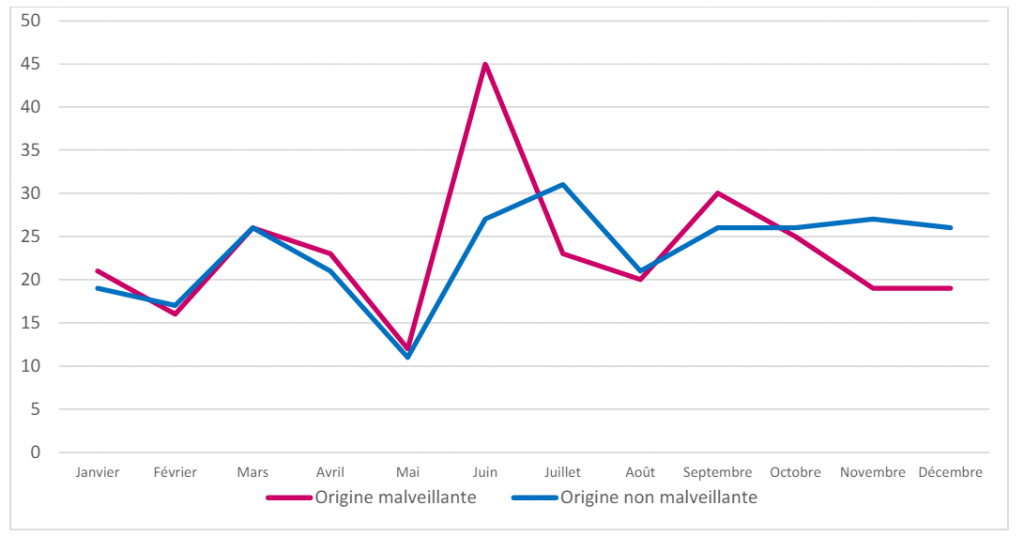
Among the incidents reported in 2023, half are of malicious origin, and the other half are non-malicious.
Malicious incidents
Of the 581 incidents reported by health structures in 2023, 50% of these were of malicious origin. The ANS counted and classified the types of malicious acts.
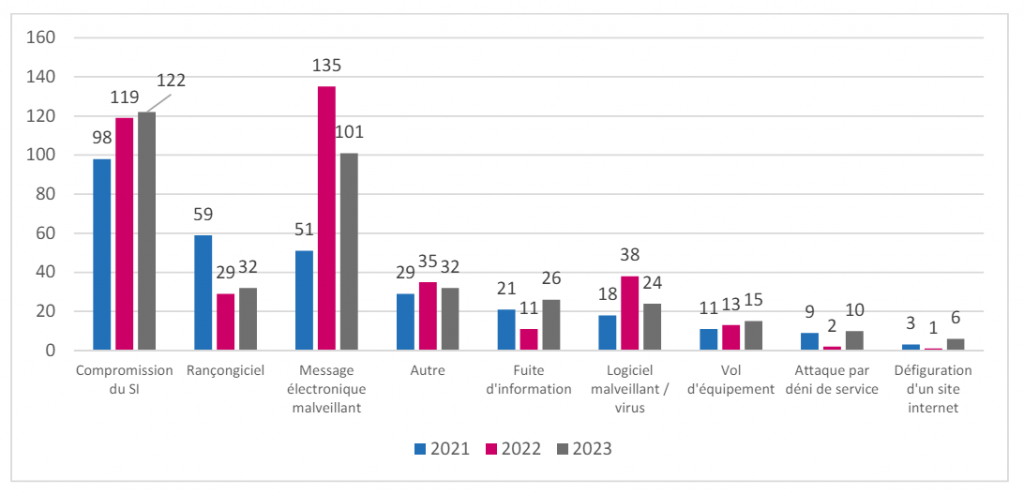
Compromise of the IS
The compromise of the Information System is strongly noticed with 122 incidents in 2023, this is the first type of malicious acts that health structures suffered in 2023.
Here, it concerns the compromise of maintenance accounts for infrastructure and application solutions.
For these two techniques, the hackers were able to recover the identifiers using several methods:
- Phishing, or phishing in English, consists of obtaining confidential information via email. As this type of technique is increasingly used, it is necessary to train and raise awareness among healthcare personnel through personalized phishing campaigns .
- Exploiting flaws and vulnerabilities on equipment. Using a vulnerability scanner allows you to act before security vulnerabilities are exploited.
- The Brute Force technique, consisting of testing a large number of passwords to access the victim’s account.
Malicious email message
As we can see, with 101 incidents, the year 2023 was also strongly marked by the use of malicious electronic messages, this consists of the theft of identifiers (logins and passwords) of electronic mail accounts and remote access accounts.
Ransomware
The 32 ransomware attacks in 2023 were evenly distributed across the 4 quarters of the year. Some of them caused critical dysfunctions within the victim establishments due to the massive loss of data and were sometimes preceded by an exfiltration of confidential or sensitive information.
The government has recommended never paying the requested ransom, for several reasons:
- Paying the ransom does not guarantee decryption of the stolen data.
- Paying the ransom does not guarantee the resale of the data on the Dark Web.
- This will not protect the health structure from being targeted by hackers again.
- This encourages cybercriminals to continue their activities.
- Obtaining a decryption key does not always allow you to reconstruct all of the encrypted files.
- The payment helps subsidize criminal organizations.
“Other”
The “Other” category brings together various types of threats, including phishing attempts by email and telephone, the distribution of USB keys containing propaganda and conspiracy theories, as well as computer intrusion attempts that do not successful.
Information leak
The information leaks concern login credentials and personal health data. It is highly recommended to use Data Leak Detection software to constantly and continuously monitor whether information has been leaked or disclosed.
Incidents of malicious origin represent a significant portion of reported incidents, however not all are of the same magnitude and do not result in the same consequences. Thus, ransomware is often the most notable and the most publicized, because confidential and personal data are stolen and are threatened with disclosure or resale.
Incidents of non-malicious origin
If 50% of incidents are malicious acts, then 50% are non-malicious. Here are the incidents reported to the ANS.
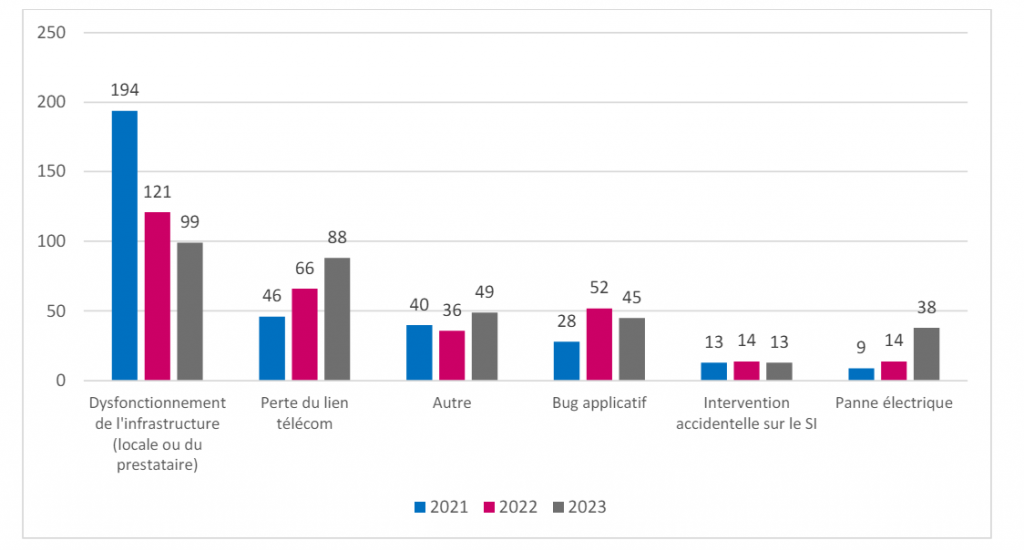
In these incidents of non-malicious origin, we find, in the majority, malfunctions of the infrastructure, this represents 35%. This category brings together incidents due to uncontrolled modifications to the internal information system, as well as problems originating from hosts or external service providers. These malfunctions may result in service or application interruptions, the duration of which varies.
With 33%, next comes the loss of the telecom link. This type of incident has a strong impact on emergency or SAMU services. Operators resolve these issues as a priority.
Application bugs are linked to external or internal applications having problems in their operation. These bugs can cause usability issues, crashes or data loss. In most cases, the publishers of the affected applications respond quickly by releasing a corrective update.
In the “other” category, we find the majority of flaws and vulnerabilities not exploited and subsequently corrected.
The consequences of cyberattacks on health structures
Whether intentional or accidental, cyberattacks against healthcare establishments can have serious consequences, affecting both the structure itself, its services and patients.
The impact on activities
When a healthcare structure is the victim of a cyberattack, its operations are seriously disrupted, affecting all of its activities.
In the event of a telecoms failure, communications with emergency services (SAMU) become impossible, compromising the care of people and patients.
The ANS report highlights the serious consequences of the incidents on health structures: 32% of them had to reduce their activities and operate in degraded mode. This means that these structures have been forced to limit their services, which can have significant impacts on patient care.
Faced with incidents, healthcare establishments must adapt their methods and processes in degraded mode. This may involve the use of paper for patient management, the implementation of alternative solutions to overcome prescription software failures or the impossibility of using credit card payments.
When an incident is not a ransomware attack, healthcare organizations operate in degraded mode for an average of one day.
In the event of a ransomware attack, healthcare establishments operate in degraded mode for more than a month. During the first week, it is necessary to organize patient care in neighboring establishments. This case concerns 8% of establishments, which were forced to interrupt their activity for certain patients.
The financial impact
Operating in degraded mode generates significant additional costs for healthcare establishments. The operational changes imposed by this mode of operation increase both costs and treatment time per patient. Indeed, the loss of time, the slowing down of tasks and the increased mobilization of staff lead to significant additional financial expenses.
In the event of a ransomware attack, although the French ministry advises against paying the ransom, healthcare establishments are statistically more likely to resort to it to recover their encrypted data.
The average ransom in the medical sector in 2022 amounts to €189,000, which is significantly less than the global average of €779,000.
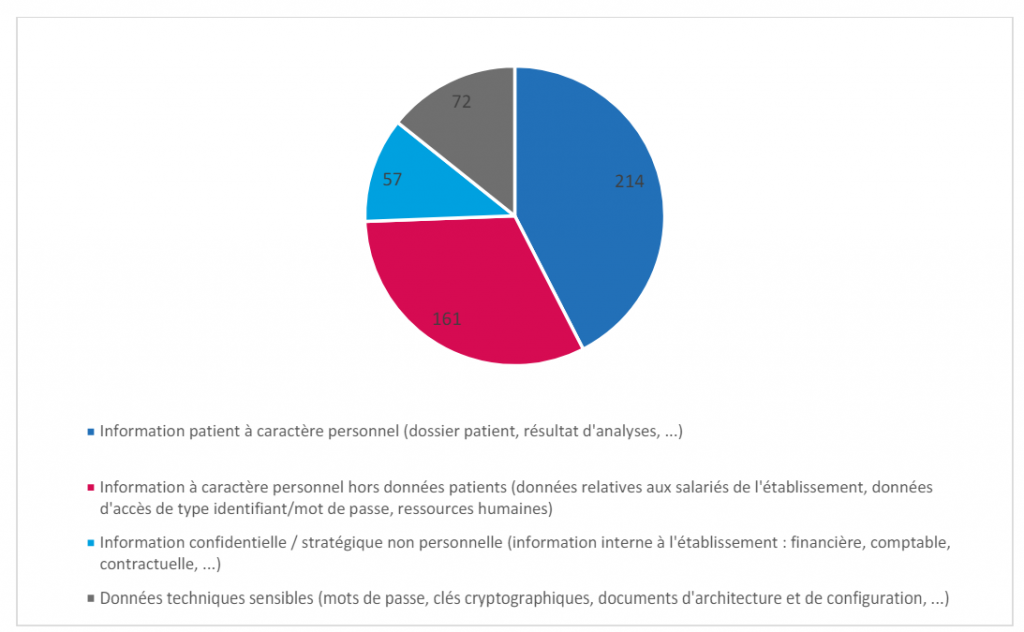
The impact on data
The report from the National Information Systems Security Agency (ANS) reveals that 59% of health establishments having suffered a cybersecurity incident were affected at the level of their data, whether data to personal nature, technical or relating to the proper functioning of the establishment.
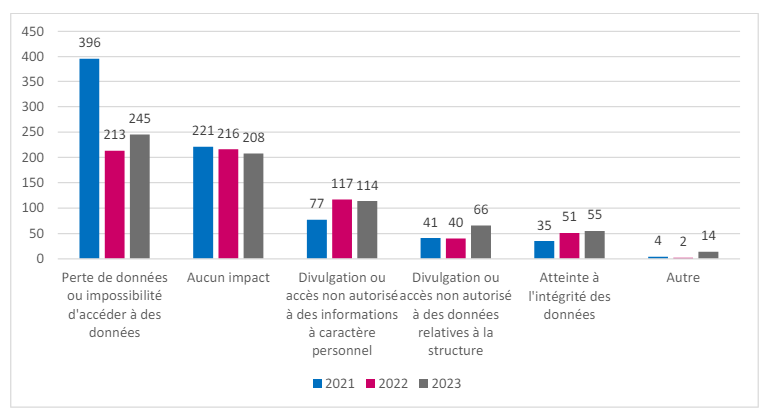
According to the ANS report, 42% of compromised information concerns patients’ personal and confidential data, such as their medical records or analysis results.
Source: https://esante.gouv.fr/sites/default/files/media_entity/documents/ans_certsante_rapport_public