Data Leaks: How to prevent deplorable consequences for companies and persons
In 2021, the National Commission for Computing and Liberties (CNIL) received 5,000 data leak declarations, affecting a total of 3 million people. In 2022, this statistic has continued to increase to reach the number of 5 million persons concerned.
In 2021, the National Commission for Computing and Liberties (CNIL) received 5,000 data leak declarations, affecting a total of 3 million people. In 2022, this statistic has continued to increase to reach the number of 5 million persons concerned. During the first months of 2023, an alarming observation was made: not less than 41.6 million accounts were compromised. This threat, which is now proving capable of impacting companies of all sizes as part of their IT and digital security policies, as well as persons in both their private and professional spheres, is worrying.
The General Data Protection Regulation (GDPR) was introduced to safeguard data privacy. He even defined data leaks as “security incidents” or “personal data breaches”.
THE CAUSES OF DATA LEAKS
Data leaks are one of the greatest cybersecurity threats of the 21st century. This threat is characterized by the negligent or unauthorized and unintentional disclosure of confidential, financial informations as well as sensitive trade secrets.
Many factors can cause these data leaks, such as :
Human errors
They can lead to harmful data leaks, especially when it comes to using weak or shared passwords, or when IT security awareness is lacking. In addition, some inappropriate practices, such as downloading files or malware, opening suspicious emails or attachments on unsecured devices, may put data at risk.
Furthermore, such errors can occur when sensitive informations are transmitted to an unauthorized person, when a storage medium containing confidential data is lost or when established security procedures are neglected.
Security vulnerabilities
Security breaches constitute a major risk to computer systems, as they provide opportunities for hackers to compromise sensitive data. These vulnerabilities can arise when systems are not regularly updated with the latest security patches, leaving doors open to attack. In addition, incorrect configurations of security settings can create vulnerabilities exploited by hackers. For example, misconfigured access permissions or unnecessary open ports can facilitate system intrusion.
Online exhibition
In the age of hyperconnection, an increasing number of devices interact with each other on a daily basis. However, it is important to be aware of the inherent risks of online data exposure.
For example, some companies that allow their employees to use their own smartphones or to connect to public Wi-Fi networks. Indeed, these devices often have security vulnerabilities, which makes it easier for hackers to inject malware and obtain confidential company information.

Data Breachs
It is crucial to distinguish data leak and data breach. Data breach, or data violation, represents an intentional attack where hackers launch cyberattacks with the aim of stealing confidential data, whether personal for people or sensitive for companies, in order to disrupt their operations. According to the CNIL “It is any security incident, whether malicious or not and occurring intentionally or not, having the consequence of compromising the integrity, confidentiality or availability of personal data”.
A large number of companies and persons are faced with this type of cyberattack, which can take different forms :
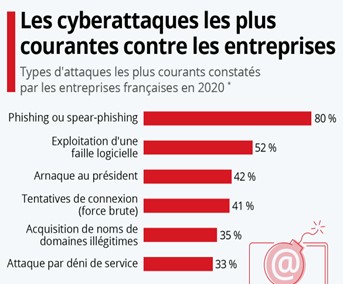
Phishing attacks
This practice, well known and widespread, represents a real danger in terms of data leaks. Indeed, a hacker pretends to be a trustworthy person or a legitimate entity in order to deceive his victim and obtain sensitive informations. In such cases, hackers use deceptive messages to trick users into divulging their login credentials, passwords, financial details or other confidential datas. They can adopt different methods, whether through fraudulent e-mails or counterfeit websites.
Use of malware
Malware, commonly referred to as malicious software, comes in the form of computer programs designed to infiltrate systems without permission and perform harmful actions in order to steal sensitive datas. What makes malware more dangerous is its ability to enter in systems without the entity concerned immediately noticing the harmful effects. This is all the more worrying as attackers exploit inherent vulnerabilities in systems.

Case of data leak
Many companies were affected by the data leak, such as URSSAF in 2023 and WhatsApp in 2022. URSSAF was the victim of a data leak during the weekend of May 1, 2023, impacting more than 10,000 persons. Indeed, a “computer error”, according to the statements of the URSSAF, was at the origin of the unauthorized disclosure of confidential data concerning 7,400 users. The next day, the organization said that 1,650 persons had an access to information that did not concern them, sparking reactions on social networks.
Some users have reported receiving documents containing very sensitive personal datas, including informations on bank accounts, income, addresses and full identities of the persons concerned. In accordance with the legislation, the URSSAF immediately notified this “computer incident” to the CNIL and strongly encouraged those whose information might have been consulted to carefully monitor their bank accounts in order to detect any possible suspicious activity.
In addition, in the year 2022, specifically, on November 16, almost 500 million WhatsApp users were affected by a data breach.
Indeed, personal informations has been put up for sale on the Dark Web. A hacker claimed to sell the updated personal informations of 487 millions WhatsApp users from 84 countries, including France, by offering “very recent mobile phone numbers”. Tech news site CyberNews has verified that the 1,914 phone numbers that were provided actually belong to WhatsApp users.
This type of attack is a striking example of the vulnerability of companies and persons to cyberattacks. This case highlights the extent of data leaks, which constitute a violation of privacy, whether for WhatsApp users or for URSSAF users. Thus, this situation underlines the crucial importance for any company to redouble its efforts to protect the data of its users and to work closely with the authorities and competent professionals to monitor hackers.
CONSEQUENCES OF DATA LEAKS
According to the CNIL and other data protection organisms, data leaks can lead to multiple harmful consequences. First of all, it is worth to highlight the risk of privacy’s invasion of people, since sensitive personal informations may be exposed, such as contact details, identifiers, financial datas, medical informations, etc. This situation can lead to identity theft and even harassment. In addition, the risk of financial harm to businesses must be considered.
Indeed, data leaks can damage their reputations, causing them to lose customers and business contracts.
In addition, companies may be subject to financial and legal sanctions for failing to comply with data protection obligations. Regulators, such as the CNIL, can conduct investigations and audits to assess compliance if necessary.
Moreover, the company DEDALUS BIOLOGY was severely sanctioned by the CNIL on April 15, 2022, with a fine of 1.5 million euros, following the leak of medical datas of 500,000 persons. This leak exposed sensitive personal informations such as first and last names, social security numbers, medical datas and other confidential medical informations. In this case, the CNIL carried out checks and seized the Paris court to block access to data published online. After identifying several breaches relating to data security, the CNIL’s restricted committee decided to impose a fine of 1.5 million euros.
This sanction highlights the crucial importance of the protection of personal datas and underlines the serious financial and legal consequences that companies can face in the event of a data breach.

DATA LEAK PREVENTION MEASURES
In order to prevent data leaks, companies and people must adopt proactive measures to strengthen the security of their systems, identify and correct existing vulnerabilities.
It is therefore important to remain constantly vigilant and never disclose sensitive informations without thorough verification of the identity of the entity or the person.
The CNIL has published a guide to help professionals comply with the Data Protection Act and the GDPR, aimed at ensuring a level of security adapted to the risk.
The guide recommends :
1. Educate users.
2. Authenticate users.
3. Manage clearances.
4. Trace access and manage incidents.
5. Secure workstations.
6. Secure mobile computing.
7. Protect the internal computer network.
8. Secure servers.
9. Secure websites.
10. Back up and plan for business continuity.
11. Archive securely.
12. Supervise the maintenance and destruction of datas.
13. Manage subcontracting.
14. Secure exchanges with other organizations.
15. Protect the premises.
16. Supervise IT developments.
17. Encrypt, guarantee integrity or sign the data.
However, it is also the people’s responsibility to implement preventive measures, such as adopting strong passwords, periodically checking their bank accounts and financial transactions in order to detect suspicious activity and report it without delay to the relevant financial institution.
NOTIFICATION IN CASE OF DATA LEAK
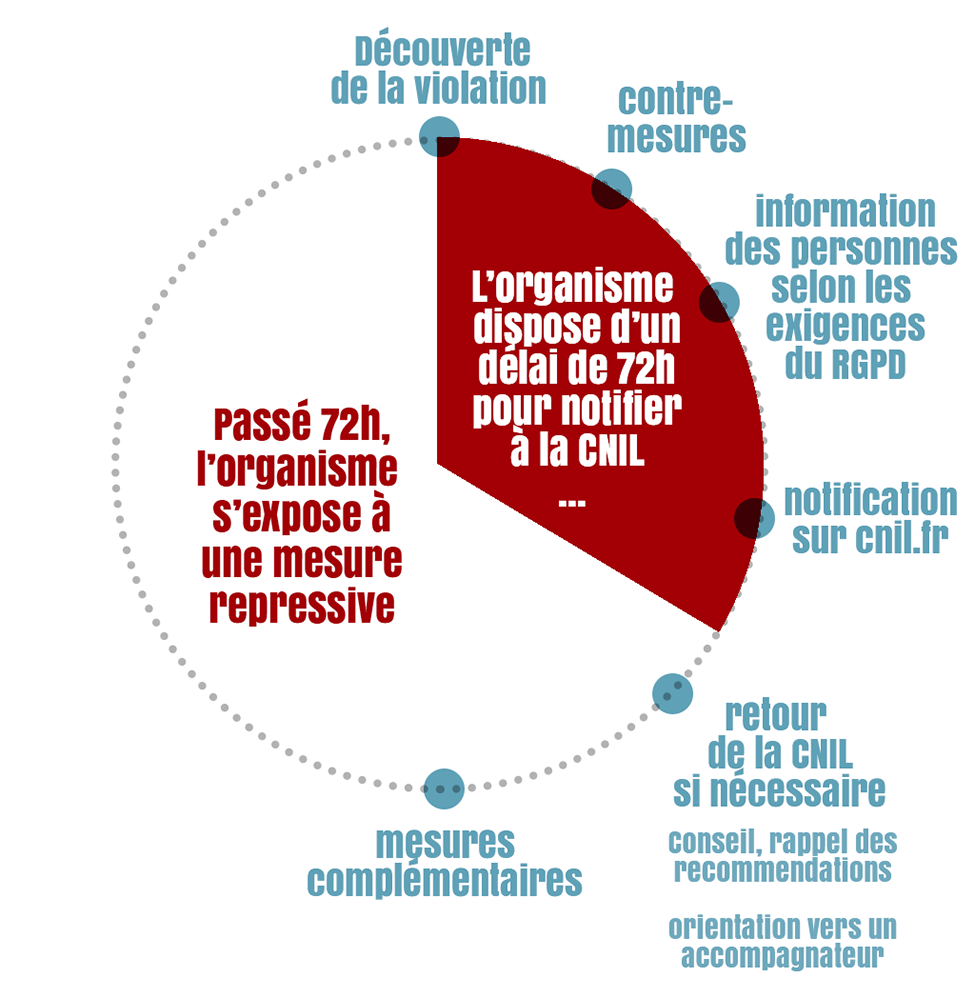
In accordance with the provisions of the General Data Protection Regulation (GDPR), in the event of a data breach, data controllers must :
1.Document the incident internally.
2. Notify the incident immediately to the National Commission for Computing and Liberties (CNIL). In the event that all the necessary information cannot be provided in time, a two-step notification may be considered. The CNIL will investigate the notification and may close the procedure if it considers that the violation has not infringed personal datas or does not present a risk to the rights and freedoms of the persons concerned.
3. In the event of a high risk for the rights and freedoms of the persons concerned, also notify the breach to them and put in place appropriate technical data protection measures.
Indeed, these actions are essential in order to comply with the legal and regulatory requirements in force. It is therefore recommended to file a complaint with the competent authorities and to provide all the evidence in the event of cyberattacks.
Finally, to minimize the risks of data leaks and protect the sensitive datas of companies and persons, it is crucial to put in place preventive measures such as automated solutions.
