Public Sector & Cybersecurity
The public sector is continually faced with cyberattacks. They can have serious consequences for administrations and citizens.
In France, as in the rest of the world, the public sector is facing growing challenges in terms of cybersecurity. Cyberattacks are increasingly frequent, sophisticated and can have serious consequences for administrations and citizens.
Why is the Public Sector so targeted?
The public sector has become a prime target for cybercriminals due to the multitude of factors that make it a fertile hunting ground. This in-depth analysis explores the motivations of cyberattackers, the specific security vulnerabilities the public sector faces, and the serious consequences that successful attacks can have.
A gold mine of sensitive data
Public administrations are guardians of treasures of sensitive data, irresistibly attracting cybercriminals in search of profits or geopolitical gains. Among the most coveted data are:
- Personal information : names, addresses, social security numbers, dates of birth, etc., which can be used for identity theft, credit card theft or insurance fraud.
- Medical data : medical records, health histories, prescriptions, etc., which can be sold on the black market or used to blackmail victims.
- Financial data : banking information, credit card numbers, tax returns, etc., which allow cybercriminals to carry out illegal money transfers or empty bank accounts.
- Government data : classified information, state secrets, trade agreements, etc., which can be exploited for espionage or to harm national interests.
Greed is not the only driver of cyberattacks against the public sector. State actors and government-sponsored hacker groups can attack government agencies to steal sensitive information, disrupt critical services, or sow discord among the population.
Vulnerable IT systems and persistent security flaws
Public administrations are often faced with budgetary challenges which force them to use aging and obsolete IT systems, which are more easily exploited by cybercriminals.
In addition, managing a complex and heterogeneous IT fleet, made up of multiple disparate systems, applications and networks, makes the implementation of coherent and effective security measures particularly difficult.
Common security vulnerabilities facing the public sector include:
- Outdated software : Governments can be slow to update their software and operating systems, leaving known vulnerabilities exposed to attacks.
- Weak passwords and lax access management practices : Lack of rigor in managing passwords and access to sensitive data can make it easier for cybercriminals to infiltrate.
- A lack of network segmentation : Lack of adequate network segmentation can allow cybercriminals to quickly spread from one system to another once they gain initial access.
- Insufficient backup and restoration procedures : In the event of an attack, administrations may find themselves unable to quickly restore their critical data if backup and restoration procedures are not adequate.
A lack of awareness and training of agents
Public officials are often the first line of defense against cyberattacks, but they can also be the weak link in the security chain. A lack of awareness of cyber risks and training in good security practices can make them more vulnerable to phishing, social engineering or phishing attacks.
For example, an agent may be led to click on a malicious link received by email, thinking that it is a legitimate communication, and thus trigger an attack on the administration’s computer network.
Various motivations and attacks with serious consequences
The motivations of cybercriminals targeting the public sector are diverse and can include:
- Data theft and resale on the dark web : Stolen data can be sold to the highest bidder on the black market, fueling a lucrative criminal economy.
- Ransomware attacks : Cybercriminals encrypt government data and demand payment of a ransom to unlock it, seriously disrupting public services and causing significant financial damage.
- Espionage and theft of state secrets : State actors and government-sponsored groups may attack government agencies to steal sensitive information for espionage purposes or to harm national interests. Such attacks can compromise national security, undermine public trust in institutions and disrupt international relations.
- Disruption of public services and degradation of the image of administrations : Cyberattacks can seriously disrupt essential public services, such as the distribution of water, electricity or health care, causing significant inconvenience to citizens and potentially put lives in danger. In addition, successful attacks can tarnish the image of administrations and weaken public confidence in their institutions.
What are the threats to the Public Sector?
Some of the most common cyberattacks facing the public sector include:
Phishing attacks
Phishing attacks aim to trick public sector employees into disclosing confidential information, such as login credentials or financial data.
Hackers can use deceptive emails, websites or SMS messages to pose as legitimate entities, such as banks, government agencies or social security organizations.
Denial of service (DDoS) attacks
Denial of service (DDoS) attacks aim to overwhelm a website or online service with fake traffic, making it inaccessible to legitimate users.
These attacks can seriously disrupt essential public services, such as government websites, tax payment systems or online health services.
Malware
Malware, such as ransomware and viruses, can be installed on public sector IT systems via infected email attachments, malicious links or code injection attacks.
Once installed, this malware can steal sensitive data, encrypt files, and render systems unusable unless the victim pays a ransom.
Intrusion attacks
Intrusion attacks aim to infiltrate public sector computer networks to steal sensitive data or take control of systems.
Hackers can exploit security vulnerabilities in software or operating systems to gain unauthorized access.
Man-in-the-Middle Attacks
Man-in-the-Middle attacks aim to intercept communications between two parties, such as a public sector employee and an online bank.
Cybercriminals can use hacked public Wi-Fi networks or fake websites to intercept sensitive data, such as passwords and banking information.
In addition to these common types of attacks, the public sector can also be the target of more sophisticated attacks, such as state-sponsored cyberattacks and targeted supply chain attacks.
What are the consequences of cyberattacks on the Public Sector?
Cyberattacks can have major consequences on the public sector, affecting its operations, its relations with citizens and its reputation.
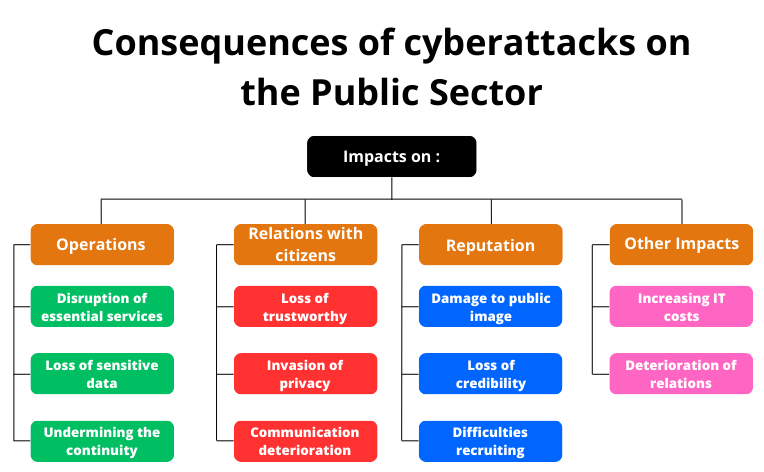
Impact on operations
Disruption of essential services
Denial of service (DDoS) attacks or ransomware can paralyze critical IT systems, affecting services such as transportation, hospitals or water distribution.
This can have serious consequences for the security and well-being of citizens, as illustrated by the 2021 ransomware attack on Costa Rica that crippled government systems, including health services.
Loss of sensitive data
The theft of sensitive data, such as personally identifiable information or medical records, can put citizens at risk of fraud and identity theft.
In 2016, the DNC data leak compromised sensitive information about Hillary Clinton’s campaign, significantly impacting the US presidential election.
Undermining the continuity of public service
Cyberattacks can disrupt or interrupt essential public services, such as issuing passports or collecting taxes. This can cause significant delays and additional costs for citizens and businesses, as illustrated by the attack on Colonial Pipeline in 2021 which caused fuel shortages and increased prices in the United States.
Impact on relations with citizens
Loss of trustworthy
Cyberattacks that result in the loss of personal data can undermine public trust in public institutions. Citizens may become reluctant to share their information with the government or use its online services.
Invasion of privacy
The theft of personal data can have a significant impact on the privacy of citizens. Victims may be at risk of identity theft, financial fraud, or other invasions of their privacy.
Communication deterioration
Cyberattacks can harm communication between government and citizens. Citizens may be less likely to report problems or request services if they are concerned that their information is not secure.
Impact on reputation
Damage to public image
Cyberattacks can tarnish the public image of the public sector and make it appear incompetent or incapable of protecting its systems and data.
Loss of credibility
Cyberattacks can undermine government credibility and its ability to carry out its mandates. This can harm public trust in democratic institutions.
Difficulties recruiting and retaining talent
Cyberattacks can make the public sector less attractive to potential employees, which can harm its ability to recruit and retain qualified talent.
Other Impacts
In addition to these direct impacts, cyberattacks can also have indirect consequences, such as:
Increasing IT costs
The public sector may have to spend significant sums to improve its cybersecurity after an attack, which can impact other programs and services.
Deterioration of international relations
Cyberattacks that target government infrastructure can damage relations between countries and increase geopolitical tensions.
Initiatives and measures to strengthen cybersecurity in the Public Sector
Faced with the growing increase in cyber threats, the public sector must take concrete measures to protect its information systems and citizens’ sensitive data. Here are some essential measures to put in place:
Strengthening cybersecurity governance and awareness
- Establish a clear and comprehensive cybersecurity policy, defining roles, responsibilities and procedures in the event of an incident.
- Appoint a cybersecurity manager with the necessary authorities and resources to implement the security strategy.
- Regularly raise awareness and train staff in cybersecurity best practices, including recognition of fraudulent emails and websites, password management and procedures to follow in the event of an incident.
Put in place adequate technical protections
- Segment computer networks to limit the impact of a cyberattack.
- Install firewalls and intrusion detection systems like a vulnerability scanner to block unauthorized access and identify attacks in progress.
- Regularly update operating systems, software and applications with the latest security patches.
- Perform regular backups of data and ensure it is stored offsite and securely.
- Encrypt sensitive data, in transit and at rest.
Take a proactive approach to risk management
- Conduct regular audits and vulnerability testing to identify security vulnerabilities and fix them before they are exploited.
- Establish an incident response plan to define actions to take in the event of a cyberattack.
- Participate in cyber training exercises to test teams’ preparedness for a real incident.
Cooperate with cybersecurity players
- Share cyber threat information and best practices with other public and private sector entities.
- Work with law enforcement to report cyberattacks and prosecute cybercriminals.
- Rely on the resources and services offered by government agencies specializing in cybersecurity, such as ANSSI in France.
Investing in cybersecurity research and development
- Support the research and development of new cybersecurity technologies to better anticipate and counter emerging threats.
- Train cybersecurity experts to fill the skills gap in this area.
