Social Engineering
Social engineering, far from being a simple abstract notion, is proving to be a formidable and constantly evolving threat in the cybersecurity landscape. To better understand its scale and implications, let’s explore in detail its workings, its techniques and the means to protect yourself from it.
Social engineering, far from being a simple abstract notion, is proving to be a formidable and constantly evolving threat in the cybersecurity landscape. To better understand its scale and implications, let’s explore in detail its workings, its techniques and the means to protect yourself from it.
Psychology and manipulation
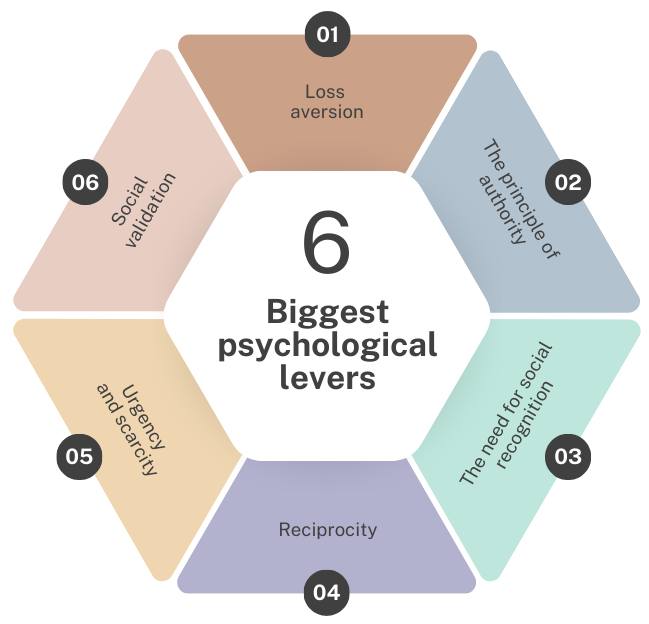
At the heart of social engineering lies a keen understanding of human psychology. Manipulators skillfully exploit cognitive biases and behavioral flaws to influence their victims and get them to act against their own interests. Among the most commonly used levers, we find:
Loss aversion
The fear of losing something valuable (money, personal data, identity) motivates individuals to act irrationally, making them more likely to give in to the manipulator’s demands.
email phishing , where an alarming message informs the victim of suspicious activity on their bank account, tricking them into clicking a malicious link to “verify their account” and disclose their login credentials.
The principle of authority
The natural tendency to respect authority figures and obey orders is taken advantage of by social engineers to extort information or actions from victims.
Posing as an IT technician, customer service representative, or supervisor, the manipulator can trick the victim into providing confidential information or performing unauthorized actions, such as installing malware.
The need for social recognition
The desire to belong to a group or to be liked by peers can push individuals to conform to the manipulator’s expectations, even if this means disclosing confidential information or carrying out harmful actions.
On social media, a malicious individual can create a popular fake profile and trick followers into sharing personal information or clicking on dangerous links.
Reciprocity
The social norm of reciprocating pushes individuals to respond favorably to the requests of those who have done them favors, thereby creating an opportunity for the social engineer to exploit this disposition.
A manipulator may pretend to be providing a service to the victim, such as “protecting their computer” from a fictitious virus, and then ask them to grant them access privileges or disclose sensitive information.
Urgency and scarcity
By creating a sense of urgency or emphasizing the rare nature of an offer, manipulators push their victims to act quickly and without thinking, thus increasing the chances of success of their attack.
An advertising message may announce a limited-time promotion or an exceptional price, encouraging the victim to seize the opportunity without verifying the veracity of the offer and to provide their personal or banking information.
Social validation
Seeing other people comply with the manipulator’s requests (for example, by providing their personal information) may motivate individuals to follow the herd and do the same, out of fear of appearing different or missing an opportunity.
On a fraudulent website, fake positive reviews and testimonials from satisfied customers can lead the victim to trust the site and make a purchase or disclose their personal information.
Attack techniques
Attackers exploit flaws in human psychology and cognitive biases to trick their victims into acting against their own interests.
Here are some of the most common social engineering attack techniques:
Phishing
Imagine receiving an alarming email from your bank notifying you of suspicious activity on your account. Panicked, you click on the link provided to log into your account and update your information. In reality, this link takes you to a fake website designed to capture your banking credentials.
Spear phishing
Unlike general phishing, spear phishing targets specific individuals or organizations. The attacker may have conducted extensive research on their victim, knowing their name, position and interests. It can thus create a personalized and highly credible email , increasing the chances that the victim will take the bait.
Baiting
Imagine finding a USB drive containing a pirated movie or software in a parking lot. The temptation to get it for free can be strong. But once inserted into your computer, the USB drive infects your system with malware that steals your data or takes control of your machine.
Malware
A seemingly innocuous email from a friend or colleague tempts you to open a funny attachment. As soon as you open it, malware silently installs itself on your computer, ready to steal your valuable information or spy on your activities.
Pretexting
An individual posing as an IT support technician contacts your company, claiming to have detected suspicious activity on your network. To “fix” the problem, it asks for your password or tricks you into installing malware.
Quid pro quo
A threatening phone call tells you that you have committed an offense and must pay a fine immediately. To “help” you, the scammer offers you a quick and convenient payment method, such as a prepaid card or an online money transfer.
Tailgating
An individual waits near the secure entrance of a building, carefully observing people approaching. When the door opens, he closely follows an authorized person to enter without being identified.
Vishing
A convincing phone call from a so-called tax agent informs you that you have a significant tax backlog. To “regularize” your situation, it asks you for your banking information or encourages you to make an immediate payment by credit card.
Protecting against social engineering
Faced with these sneaky attacks, vigilance and proactivity are your major assets. Here is a complete guide to protect yourself effectively:
Strengthen your vigilance
Healthy distrust
Be skeptical of any unsolicited communications, whether emails , text messages, phone calls or messages, especially if the sender is unknown to you or if the message seems urgent. Remember: Irresistible offers or messages creating a sense of urgency are red flags.
Careful verification
Hover over the links to view the actual URL before clicking. Never click on shortened or suspicious links. Be wary of unexpected attachments, even if they come from a seemingly known contact.
Carefully analyze the email address and the content of the message: spelling or grammatical errors, an unusual tone or urgent requests may indicate an attempt at fraud.
Trusted Sources
Never disclose personal or financial information to people you do not know or fully trust. Always verify the identity of the speaker and the communication channel before disclosing sensitive information. If in doubt, contact the organization or individual concerned directly using an official and secure communication channel.
Protect your devices
Security software
Install powerful antivirus and anti-malware on your devices, keep them updated, and enable their real-time protection features. Choose trusted security solutions and make sure they have the latest updates and protections.
Regular updates
Regularly update your operating system, applications and browser to close identified security vulnerabilities. Enable automatic updates when possible to ensure optimal protection.
Secure browsing
Avoid unsecured public Wi-Fi networks for sensitive transactions, such as online shopping or banking. Use a VPN (Virtual Private Network) to encrypt your online traffic and protect your confidential data, especially when connecting on public networks.
Adopt safe habits
Strong Passwords
Use unique, complex passwords for each online account, and change them regularly. Avoid using easily guessable personal information like your name, date of birth, or address.
Multi-factor authentication
multi-factor authentication for your important accounts, adding an extra layer of security. In addition to your password, you will be required to enter a verification code sent via SMS or mobile app, making it more difficult for hackers to access your accounts.
Responsible behavior
Never share your personal information or passwords with third parties, even if you know them. Be careful about unusual requests, even if they come from colleagues or friends.
Beware of phone scams
Be wary of unsolicited phone calls, especially if the caller is pressuring you to take action or threatening you. Never give personal or financial information over the phone to people or organizations you don’t know. Always verify the authenticity of the caller by hanging up and searching for the phone number independently.
Raising awareness and sharing knowledge
Information and training
Stay informed of the latest social engineering techniques and raise awareness among those around you, family, friends and colleagues, to minimize the risk of attacks. Share press articles, awareness videos or online training so everyone can protect themselves against these threats.
Sharing experiences
Openly discuss the social engineering attempts you have encountered with those around you. This will allow everyone to better identify warning signs and take appropriate protective measures.
Raise awareness with a phishing campaign
A phishing campaign, also called phishing, is a fraudulent operation orchestrated on a large scale to deceive individuals or organizations. Its main objective is to extract sensitive information, such as login credentials, banking details or personal information, for illegitimate purposes.
