Spear Phishing
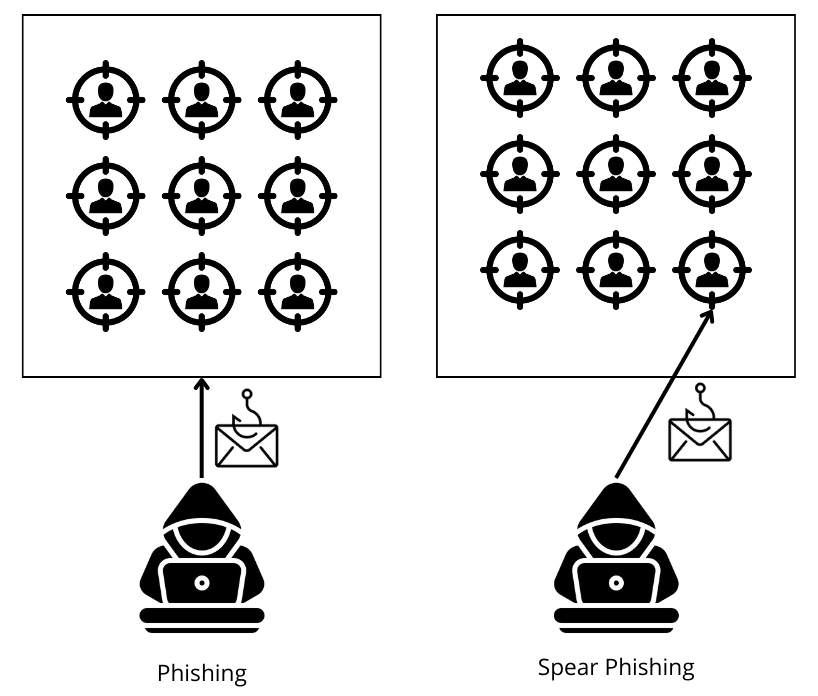
Spear Phishing is a sophisticated email attack technique that targets specific individuals or organizations.
Spear Phishing is a sophisticated email attack technique that targets specific individuals or organizations.
Unlike traditional phishing attacks that send mass emails to random recipients, Spear Phishing targets specific individuals or organizations, exploiting their vulnerabilities and manipulating them to obtain confidential information or install malware.
How does Spear Phishing work?
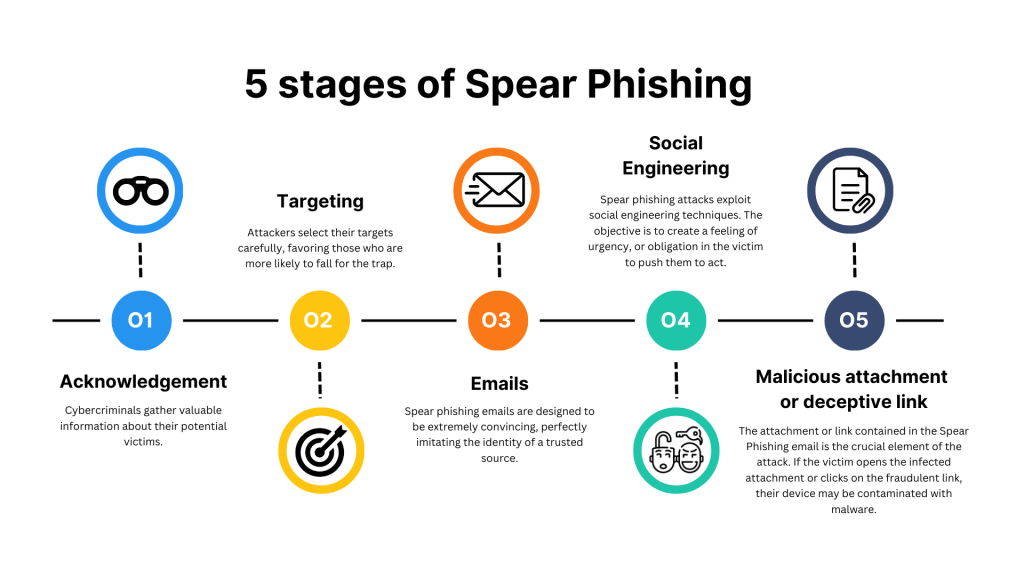
Spear Phishing works in 5 steps:
- Acknowledgement.
- Targeting.
- Emails.
- Social Engineering.
- Malicious attachment or deceptive link.
1. Acknowledgement
Before launching their offensive, cybercriminals carry out in-depth reconnaissance work on their targets. They gather valuable information about their potential victims such as:
- Names,
- Identities,
- Email addresses ,
- Passwords,
- Personal interests,
- Functions,
- Financial datas.
This information can be gleaned from a variety of sources:
- Social networks,
- Business websites,
- Data leaks,
- Social engineering, where psychological manipulation tricks targets into voluntarily disclosing their information.
2. Targeting
Once they have a precise profile, attackers select their targets carefully, favoring those who are more likely to fall for the trap.
They can target:
- Individuals occupying key positions within a company.
- Those who have access to sensitive information.
- Or those who are more inclined to trust the alleged sender of the message.
3. Emails
Spear phishing emails are designed to be extremely convincing, perfectly imitating the identity of a trusted source, such as a colleague, supervisor, bank or other trusted organization.
They can include information specific to the target, like their name, status, or recent details about their work, which further enhances their credibility.
4. Social Engineering
Spear Phishing attacks commonly exploit social engineering techniques.
The goal is to create a sense of urgency, curiosity or obligation in the victim to push them to act.
The email can alert the target of suspicious activity on their account, ask them to update their login credentials or offer them an attractive offer not to be missed.
5. Malicious attachment or deceptive link
The attachment or link contained in the Spear Phishing email is the crucial element of the attack.
If the victim opens the infected attachment or clicks on the fraudulent link, their device may be contaminated with malware, such as a Trojan or ransomware.
Attackers can then exploit this malware to steal sensitive data, take control of the victim’s device, or extort money.
What are the objectives of Spear Phishing?
Spear Phishing attacks are diverse and often lucrative. The perpetrators of these malicious attacks may have several objectives in mind, including:
Theft of sensitive data
- Financial information (credit card numbers, bank account information),
- Personal identification information (social security numbers, passports),
- Confidential commercial data (trade secrets, strategic plans).
Installation of malware
- Malicious attachments or links to infected websites, allowing data theft, spying on victim activity, taking control of their device, or launching denial of service attacks.
Disruption of operations
- Infiltration of a company’s systems with malware, causing service interruptions, production delays, financial losses and reputational damage.
- Inducing employees to disclose confidential information, passwords or install malware, thereby compromising the security of systems and data.
Damage to reputation
- Sending defamatory emails to a company’s customers or partners, tarnishing its image and damaging its trust.
Examples of Spear Phishing
There are several concrete cases of Spear Phishing attacks:
- Email attack targeting an employee.
- Email attack with malicious attachment.
- Smishing attack (SMS phishing).
- Vishing attack (voice phishing).
- President fraud attack (CEO Fraud).
1. Email attack targeting an employee
Scenario
An employee receives an email apparently from their manager, asking them to change the company’s banking information for a vendor. The email contains a company logo and is written in a style similar to legitimate emails from the manager.
Possible consequence
If the employee is not careful and provides the banking information, hackers can use it to embezzle funds from the company.
2. Email attack with malicious attachment
Scenario
An employee receives an email apparently from a colleague, with an attachment titled “urgent report.docx.” The email states that the report is important and should be reviewed urgently.
Possible consequence
If the employee opens the attachment, they can infect their computer with malware that allows hackers to steal data or take control of their system.
3. Smishing attack (SMS phishing)
Scenario
An employee receives a text message apparently from their bank, informing them that there has been suspicious activity on their account and asking them to click on a link to confirm their identity.
Possible consequence
If the employee clicks on the link, they may be directed to a fake bank website where they will be asked to enter their login information. Hackers can then use this information to steal money from their bank account.
4. Vishing attack (voice phishing)
Scenario
An employee receives a phone call apparently from their IT department, informing them that there is a problem with their computer and asking them to provide their remote access information.
Possible consequence
If the employee provides their access information, hackers can take control of their computer and steal their data.
5. President fraud attack (CEO Fraud)
Scenario
A senior executive receives an email apparently from the company’s CEO, asking him to make an urgent bank transfer. The email is very compelling and uses urgent language to urge the executive to act quickly.
Possible consequence
If the senior executive makes the transfer, hackers can steal a significant amount of money from the company.
How to protect yourself from Spear Phishing?
Spear Phishing is a formidable threat to individuals and organizations. Unlike classic phishing which sends generic emails to a large audience, Spear Phishing targets specific victims by relying on personal and professional information collected beforehand.
To protect against these sophisticated attacks, it is crucial to adopt increased vigilance and implement best practices:
1. Thorough email verification
- Never automatically click on links or open attachments in an email, even if it appears to come from a known source.
- Hover over the links to check the actual URL before clicking.
- Be wary of emails that create a sense of urgency or threat.
- Check the sender’s email address: fake addresses can deceptively resemble legitimate addresses.
- Spear Phishing emails may contain spelling or grammatical errors.
2 . Authentication and passwords
- Never use the same password for multiple accounts.
- Enable two-factor authentication (2FA) for added protection of your accounts.
- Avoid entering confidential information, such as passwords or banking details, directly into an email.
3. Updates and security solutions
- Keep your operating systems, web browsers and security software up to date.
- Install powerful antivirus and anti-malware and enable real-time protection.
- Consider security solutions dedicated to combating Spear Phishing for enhanced protection.
4. Procedures in the event of an attack
- If you think you have been the victim of a Spear Phishing attack, don’t panic.
- Change your affected passwords immediately .
- Report the attack to your IT department or the person responsible for cybersecurity within your organization.
- Never respond to the suspicious email or pass on any personal or confidential information.
5. Awareness and training
The first line of defense against Spear Phishing lies in user awareness.
Regular training allows them to learn to identify suspicious emails, to recognize the manipulation techniques used by attackers and to adopt appropriate behaviors.
