The importance of DAST (Dynamic Application Security Testing) in your web security strategy
Today, web environments are evolving quickly and integrating a wide variety of technologies, which requires security solutions to constantly adapt. DAST (Dynamic Application Security Testing) scanners, designed to detect vulnerabilities in dynamic applications, are among these solutions.
With the proliferation of web technologies and the increasing complexity of applications, threats are intensifying. However, cybersecurity teams, often with limited staff, still struggle to effectively identify, analyze, and correct vulnerabilities. Without a way to centralize visibility and management, simply adding more security tools to existing workflows offers diminishing returns at best and could even be detrimental if the tools generate more work than they save. This is why many companies purchase tools that remain unused, due to a lack of resources to exploit the new product and manage an additional source of security data.
One way to overcome this complexity is to simplify and centralize application security testing. This is where adopting a “DAST-first” approach can make the difference between having an arsenal of tools and having a functional AppSec program. And considering that application environments change quickly and one can never be sure what challenges will arise in the medium and long term, having a reliable and up-to-date DAST solution to keep everything in check is the best way to ensure the future security of your applications.
DAST (Dynamic Application Security Testing) solutions, which enable the detection of vulnerabilities in dynamic applications, are emerging as an essential response to securing modern web applications. Unlike static methods, DAST analyzes applications while they are running, providing a realistic view of exploitable vulnerabilities and methods to address them.
The Advantage of the DAST-First Approach
The “DAST-first” approach enables crucial centralization of application security efforts, offering several strategic advantages:
- Obtain Unified Visibility: A central DAST platform provides a coherent overview of the security status of all applications, facilitating the prioritization of efforts and decision-making.
- Optimize Resources: By centralizing security testing, teams can avoid duplicating efforts and optimize the use of limited resources.
- Standardize Processes: Adopting a centralized approach promotes the standardization of security practices within the organization, thereby improving the overall consistency and effectiveness of security efforts.
- Detect Vulnerabilities in Real Context: DAST identifies flaws as they would appear to a real attacker, including vulnerabilities related to server configuration or interactions between components.
- Reduce False Positives: By verifying the exploitability of vulnerabilities, DAST significantly limits the number of false positives, saving valuable time for security teams.
- Ease of Implementation: Unlike SAST, DAST does not require access to the source code, making it ideal for testing third-party applications or those using various technologies. DAST solutions can operate in production.
One of the major strengths of HTTPCS is its ability to perform security tests without requiring deep technical knowledge of the code or application architecture. As a dynamic vulnerability scanner, it can analyze the attack surface of any web application, regardless of the programming language used. This flexibility allows it to be deployed at any time, without requiring advance planning during the deployment phase. This is a significant advantage in a world where reactivity is often key to security.
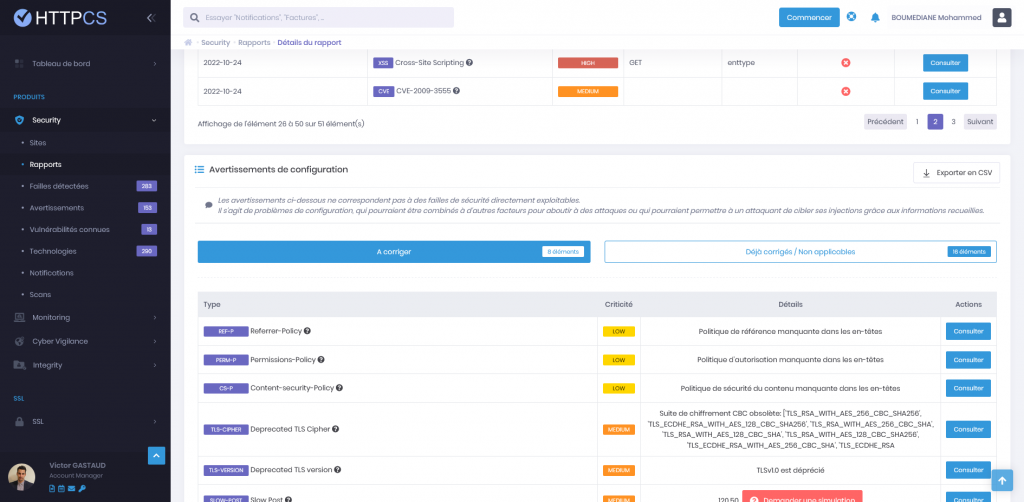
Example of technical details from HTTPCS vulnerability scan reports
How a Dynamic Vulnerability Scanner (DAST) Works
DAST operates through a multi-step process, beginning with crawling, where the scanner traverses the web application, identifying all accessible pages, forms, and entry points. It then performs a detailed analysis of requests and responses, examining each interaction with the application in order to detect anomalies or suspicious behaviors.
The scanning process revolves around several essential steps aimed at effectively detecting website vulnerabilities:
- Site Mapping and Scanner Learning: The scanner begins with an exploration phase to identify and catalog all accessible resources on the target platform. This step relies on two complementary approaches: static detection of URLs and resources through source code analysis, and advanced dynamic crawling to explore navigation paths in real-time. The goal is to maximize scan coverage and continuously enrich the learning base. Note: Continuous optimization through machine learning (HTTPCS technology): To maximize precision and efficiency, the crawling bot integrates machine learning techniques to identify the most relevant navigation paths. This adaptive approach improves scan coverage and optimizes vulnerability detection by adjusting in real-time to the specifics of each audited site.
- Analysis of Site Technologies: Once mapping is complete, the scanner analyzes the technologies used by the site, including frameworks, CMS, libraries, programming languages, and hosting servers. This precise identification not only helps detect known vulnerabilities associated with the detected versions but also adapts attack techniques to the site’s specific technological environment.
- Detection and Qualification of Exploitable Parameters: The scanner then identifies potentially exploitable entry points, such as form fields, API requests, and URL parameters. It qualifies these elements by analyzing their behavior in response to various injection payloads, considering the application context and protection mechanisms in place.
- Simulation of Attacks and Highlighting Vulnerabilities: Once exploitable parameters are identified, the scanner executes a series of automated tests to simulate attacks. These tests evaluate the robustness of implemented protections and detect potential exploitable flaws. Analyzing server responses then validates the presence of a vulnerability and measures its criticality.
The advantage of DAST is that it allows the reproduction of exploitation payloads (vulnerability “trust” phase), enabling users to reproduce the vulnerability and concretely understand its consequences.
Seamless Integration of DAST into DevOps Processes
With much of web development now following agile methodologies in automated CI/CD pipelines, application security testing must be part of this automated chain. Traditionally, each stage of the software development lifecycle (SDLC) required a distinct set of security testing tools, as you could only perform static analysis during development, vulnerability analysis during evaluation, and penetration testing in production. This is no longer the case, as advances over the past decade have significantly expanded the utility of automated DAST solutions in the SDLC.
Due to their nature, DAST tools test from the outside and do not need to know what is happening under the hood. An effective DAST allows you to analyze the entire environment of your web applications and probe each potential attack point without knowing or worrying about internal elements: programming languages, application architecture, deployment details, external dependencies, etc.
Practical Application: The Example of HTTPCS
To concretely illustrate the application of these principles, consider HTTPCS, a DAST solution developed by Ziwit, which embodies the “DAST-first” approach:
- Advanced Heuristic Analysis: HTTPCS uses artificial intelligence techniques, including machine learning, to analyze attack patterns and categorize vulnerabilities. Through this approach, it detects complex and contextual threats often overlooked by traditional scanners by identifying correlations and anomalies in web interactions.
- Deep DevSecOps Integration: With its REST API and plugins for major CI/CD tools, HTTPCS seamlessly integrates into modern development environments, enabling extensive automation of security tests and ensuring early detection of vulnerabilities.
- Centralized Platform: HTTPCS offers a unified dashboard, providing complete visibility into the security status of monitored web applications and services, thereby facilitating the management and prioritization of security efforts.
- Reduction of False Positives: Through active validation of vulnerabilities, the HTTPCS vulnerability scanner drastically reduces the number of false positives. When a problem is detected, the scanner performs controlled exploitation by sending injection or verification payloads (e.g., self-validated XSS, data exfiltration demonstration, display of exposed directories and files, etc.). This allows security teams to focus on genuinely exploitable vulnerabilities, optimizing remediation time.
- Adaptability to Emerging Technologies: HTTPCS is constantly updated to support the latest web technologies, ensuring effective protection even against the most modern application environments.
- The Advantage of Continuous Monitoring: The power of HTTPCS lies in its ability to perform frequent tests, even without complex preconfiguration, other than scheduling related to scan campaigns. Through frequent execution and adaptive analysis (e.g., differential scan after deployment), it adapts to environments where code changes are constant. HTTPCS enables the automation of both comprehensive and targeted analyses, ensuring that security is maintained continuously.
Conclusion
In an era where web application security is more crucial than ever, DAST scanners are indispensable tools for companies managing the security of a large volume of sites and applications, or those whose applications are primary sources of value (e.g., software publishers).
By providing a robust, fast, and adaptable solution, HTTPCS enables security teams to stay ahead of ever-evolving threats.
Adopting a “DAST-first” approach, exemplified by solutions like HTTPCS, represents more than just a technological choice. It is a paradigm shift in how web application security is approached, moving from a reactive to a proactive and integrated stance.
By centralizing security efforts around a robust DAST platform, organizations can significantly improve their security posture, optimize resources, and accelerate development cycles. Faced with increasingly complex application environments and evolving threats, DAST is one of the most suitable solutions for ensuring effective and lasting protection of the exposed web perimeter.
The future of application security lies in the ability to combine flexibility, efficiency, and integration. Organizations that embrace this approach will gain a crucial competitive advantage, as mastering application security becomes a major differentiating factor, and the “DAST-first” approach is the cornerstone.
