Biggest Cyber Incidents of 2023
Cyberattacks increased significantly in 2023. Find the biggest cyber incidents of 2023 in our infographic and blog article.
Cyberattacks increased significantly in 2023. According to Verizon’s annual cybersecurity report, the number of reported cybersecurity incidents increased by 15% compared to 2022.
The most common types of attacks in 2023 were ransomware attacks, phishing attacks, and distributed denial of service (DDoS) attacks.
Find the biggest cyber incidents of 2023 in our infographic and blog article.
DarkBeam
DarkBeam is a US-based cybersecurity company that provides security services to businesses and individuals.
DarkBeam suffered a data theft in September 2023. The company said a hack exposed the personal data of more than 3.8 billion people.
The compromised data included:
- Names.
- Email addresses.
- Phone numbers.
- Passwords.
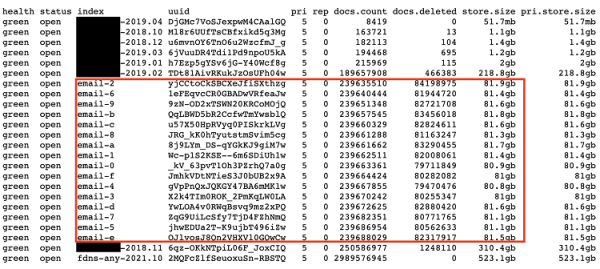
They came from multiple sources, including DarkBeam customers, business partners, and company employees.
DarkBeam said it believed the hack was carried out by a group of cybercriminals known as “DarkSide.”
The cybercriminals managed to access an interface of DarkBeam called Elasticsearch and Kibana. This interface allows companies to visualize and analyze their data. Cybercriminals were able to exploit a vulnerability in the interface to access sensitive data.
DarkBeam said it had taken steps to patch the vulnerability that allowed the data theft. The company also notified those whose data was compromised.
Real Estate Wealth Network
In 2023, a group of cybercriminals attacked the Real Estate Wealth Network (RWEN), a network of real estate professionals and investors. The attackers gained access to sensitive data, including:
- Personal information.
- Financial records.
- Investment strategies.
The attack was carried out using a targeted phishing email, which is a targeted email message that appears to come from a legitimate source. The attackers were able to trick RWEN employees into clicking on a malicious link, allowing them to install malware on the company’s network.
Once the malware was installed, the attackers were able to move laterally across the network, gaining access to more sensitive data. They ultimately stole a significant amount of data, which they threatened to sell on the dark web.
According to SecurityWeek, Real Estate Wealth Network exposed more than 1.5 billion records due to an exposed database on the Internet that contained 1.16 TB of data organized into numerous folders.

RWEN was forced to take its network offline for several days while it investigated the attack and implemented security measures to prevent future breaches. The company also notified law enforcement and offered credit monitoring and identity theft protection services to affected customers.
MGM
On September 12, 2023, MGM Resorts International, a Las Vegas-based hotel and casino company, was the victim of a cyberattack. The attack affected the computer systems of several MGM casinos in Las Vegas, including the MGM Grand, the Mandalay Bay and the Bellagio.
The hackers gained access to customers’ personal data, including:
- Names.
- Addresses.
- Phone numbers.
- Email addresses.
- Credit card numbers.
The hackers also gained access to customer bank account and credit card information.
MGM said the hackers used a security hole in its computer system to access the data. The company also said there has been no impact on casino operations.
After discovering the cyberattack, MGM took steps to secure its systems and notify affected customers. The company also offered affected customers a free credit monitoring service for one year.
The cost of the MGM cyberattack in 2023 is estimated at $1.5 billion. This cost includes direct costs, such as investigation, repair, and customer compensation costs, as well as indirect costs, such as loss of reputation and decreased sales.
The direct costs of the cyberattack include:
- Investigative costs: MGM hired a cybersecurity firm to investigate the attack. The costs of this investigation are estimated at $100 million.
- Repair costs: MGM had to invest in additional security measures to strengthen its computer systems. The costs of these measures are estimated at $500 million.
- Customer Compensation: MGM offered customers whose data was compromised a free credit monitoring service for one year. The costs of this service are estimated at $500 million.
The indirect costs of the cyber attack include:
- Loss of reputation: The cyberattack tarnished MGM’s reputation. The company has received criticism from customers, investors and regulators.
- Decreased sales: The cyberattack led to a decrease in MGM’s sales. Customers were reluctant to patronize the company’s casinos after the cyberattack.
23andMe
23andMe is an American biotechnology company based in Mountain View, California. The company offers genetic testing to individuals, which allows them to trace their origins, discover their predisposition to certain diseases and better understand their health.
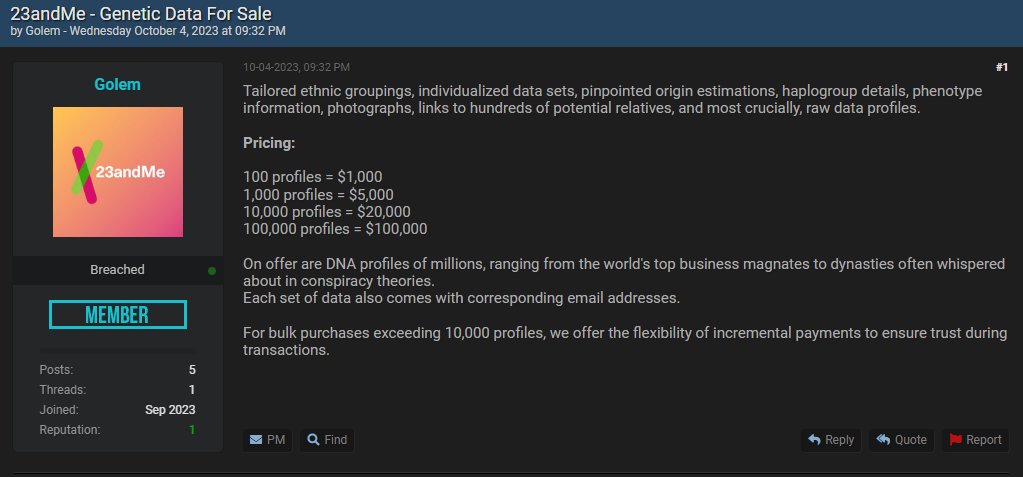
In October 2023, a major computer attack affected 23andMe.
Hackers gained access to 23andMe data by exploiting a security vulnerability in the company’s internal systems. The compromised data included:
- Names.
- Email addresses.
- Dates of birth .
- Zip codes for all affected customers.
For a subset of customers, hackers also accessed more sensitive information, such as:
- Genetic information.
- Biometric data.
- Health data.
The compromised genetic information included information about ancestry, disease predisposition, and other data that could be used to identify individuals or to target individuals for malicious purposes.
The compromised biometric data included:
- Fingerprint information.
- Irises.
- Other data that could be used for identity theft.
The compromised health data included:
- Informations about medical conditions.
- Treatments.
- Other data that could be used for medical fraud or blackmail.
After discovering the cyberattack, 23andMe took steps to secure its systems and notify affected customers. The company also offered free credit monitoring and identity protection services to affected customers.
Indian Council of Medical Research (ICMR)
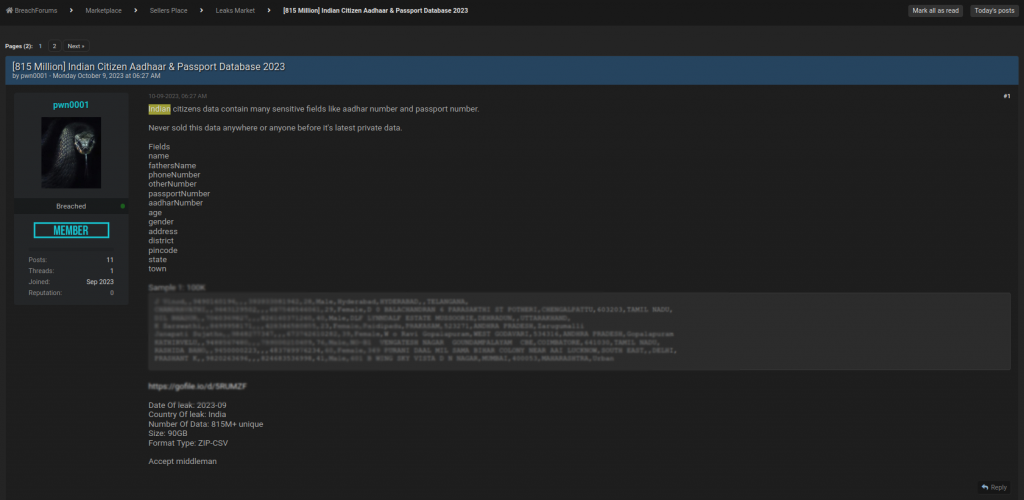
In October 2023, a data breach occurred within the Indian Council of Medical Research (ICMR), the Indian government body responsible for medical research.
The leak revealed personal information of more than 815 million people, including:
- COVID-19 test results.
- Email addresses.
- Phone numbers.
- Health information.
The leak was discovered by an Indian cybersecurity researcher, who alerted authorities. The ICMR confirmed the leak and launched an investigation.
The information disclosed includes:
- The names, addresses, telephone numbers and email addresses of those tested.
- COVID-19 test results, including test dates, positive or negative results, and types of variants detected.
- Health information, such as medical history and allergies.
The ICMR has taken steps to address the data leak. The agency blocked access to the database and launched an investigation. The ICMR also advised affected individuals to take steps to protect their privacy, such as changing their passwords and being vigilant against fraudulent messages.
The Indian government has also taken steps to address the data leak. The government has established a cybersecurity team to investigate the incident and propose protective measures.
T-Mobile
T-Mobile is an American wireless carrier that provides telecommunications services to individuals and businesses. The company is a subsidiary of Deutsche Telekom, a German telecommunications company.
T-Mobile suffered two hacks in 2023. The first hack, which took place in January, affected the data of 37 million customers. The second hack, which took place in April, affected the data of 836 customers.
The January hack
The first hack was carried out by a group of hackers known as Lapsus$. Lapsus$ is a group of hackers known for their attacks against major companies, such as Microsoft, Nvidia and Samsung.
Lapsus$ said it gained unauthorized access to a T-Mobile API, which allowed it to access the data of 37 million customers. The hacked data included:
- Names.
- Addresses.
- Phone numbers.
- Dates of birth.
- Account numbers.
T-Mobile said it had taken steps to strengthen the security of its information systems. The company also offered customers affected by the attack a free credit monitoring service for one year.
The March hack
The second hack was committed by an unidentified individual. The individual used a security hole in T-Mobile’s billing system to access the data of 836 customers. The hacked data included:
- Names.
- Addresses.
- Phone numbers.
- Account numbers.
T-Mobile said it fixed the security breach and offered customers affected by the attack free credit monitoring service for six months.
Pôle Emploi
Pôle emploi is a French public administrative establishment whose mission is to support job seekers in their job search and to facilitate company recruitment.
In August 2023, Pôle emploi announced that it had been the victim of a cyberattack. The attack hit an IT service provider for the national employment agency, which houses the personal data of millions of job seekers.
According to Pôle emploi, the data affected by the attack includes:
- Names.
- First names.
- Social security numbers.
- Addresses.
- Dates of birth.
- Telephone numbers of 10.2 million people.
The data of 9.6 million people concerns job seekers registered in February 2022, and the data of the other 600,000 people concerns former beneficiaries.
French authorities have opened an investigation to determine the origin of the attack and identify those responsible.
The consequences of this cyberattack are potentially serious. Victims’ personal data could be used for identity theft, fraud or blackmail. Victims are therefore advised to be vigilant and take protective measures, such as setting up a security code on their bank accounts and complex passwords.
Pôle emploi has taken measures to strengthen the security of its information systems. The agency has also set up a toll-free number for victims of the cyberattack.
MOVEit
In 2023, a series of cyberattacks targeted MOVEit, a secure data transfer software. The attacks were carried out by a group of cybercriminals known as “Lace Tempest”.
The first attack
The first attack took place on May 27, 2023. Hackers used a zero-day security flaw in MOVEit to access data from several organizations. The flaw allowed hackers to execute malicious code on MOVEit’s servers, giving them full access to data stored on those servers.
Organizations hit by the first attack included a bank, a technology company and a government agency. The compromised data included:
- Names.
- Addresses.
- Phone numbers.
- Email addresses.
- Credit card numbers.
The following attacks
Attacks continued over the following weeks, affecting more than 600 organizations, including businesses, governments, and nonprofits. The compromised data included sensitive information, such as financial data, medical data and personal data.
Cybercriminals have threatened to auction the compromised data on the dark web. They also demanded ransoms from affected organizations.
The consequences of the attacks
MOVEit cyberattacks in 2023 have had significant consequences for affected organizations. Compromised data could have been used for identity theft, fraud or blackmail.
Organizations also incurred significant costs in dealing with the attacks, including investigation costs, remediation costs, and victim compensation costs.
The British Electoral Commission
In August 2023, the UK Electoral Commission suffered a hack. Hackers gained access to the data of 40 million British citizens, including:
- Names.
- Email addresses.
- Postal addresses.
- Phone numbers.
- Voter registration dates.
The Electoral Commission said the hackers used a security flaw in its IT system to access the data. The organization also said there was no impact on UK electoral processes.
British authorities have opened an investigation to determine the origin of the attack and identify those responsible.
The consequences of hacking the UK Electoral Commission are potentially serious. Victims’ personal data could be used for identity theft, fraud or blackmail.
Victims are therefore advised to be vigilant and take protective measures, such as setting up a security code on their bank accounts and complex passwords.
The HTTP/2 protocol
In August 2023, a zero-day vulnerability was discovered in the HTTP/2 protocol. This vulnerability, called “HTTP/2 Rapid Reset”, allows attackers to launch large-scale distributed denial of service (DDoS) attacks.
How does the vulnerability work?
The HTTP/2 protocol allows clients to request multiple resources at the same time, and each resource is identified by a stream. Streams are multiplexed over a single TCP connection, which improves performance.
The vulnerability lies in the flow management in the HTTP/2 protocol. When a client requests a resource, the HTTP/2 server creates a stream for that resource. If the client cancels the request, the HTTP/2 server must release the stream.
Attackers can exploit this vulnerability by sending requests to an HTTP/2 server and then quickly canceling those requests. This may cause server overload, which may make it unavailable to legitimate users.
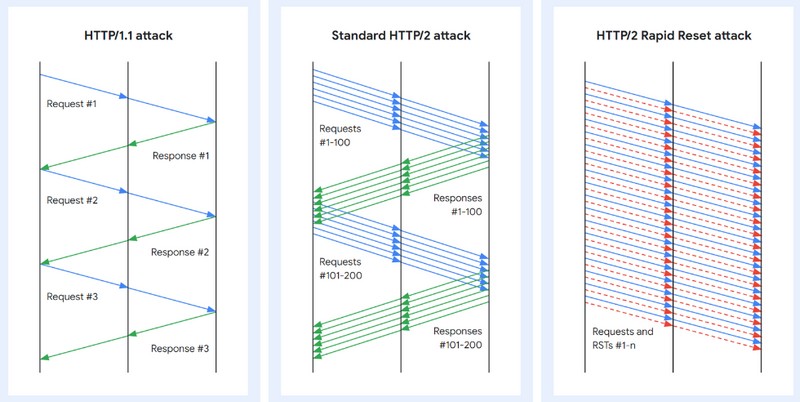
How did attackers exploit this vulnerability?
Attackers exploited this vulnerability by using bots or botnet farms to send HTTP/2 requests to a target server. Requests were canceled quickly, causing server overload.
In some cases, attackers used social engineering techniques to trick users into clicking on malicious links. These links resulted in the download of malware that exploited the HTTP/2 Rapid Reset vulnerability.
What were the impacts of this vulnerability?
This vulnerability was exploited in several record DDoS attacks in 2023. Google said it blocked a 398 million requests per second (RPS) DDoS attack that exploited this vulnerability.
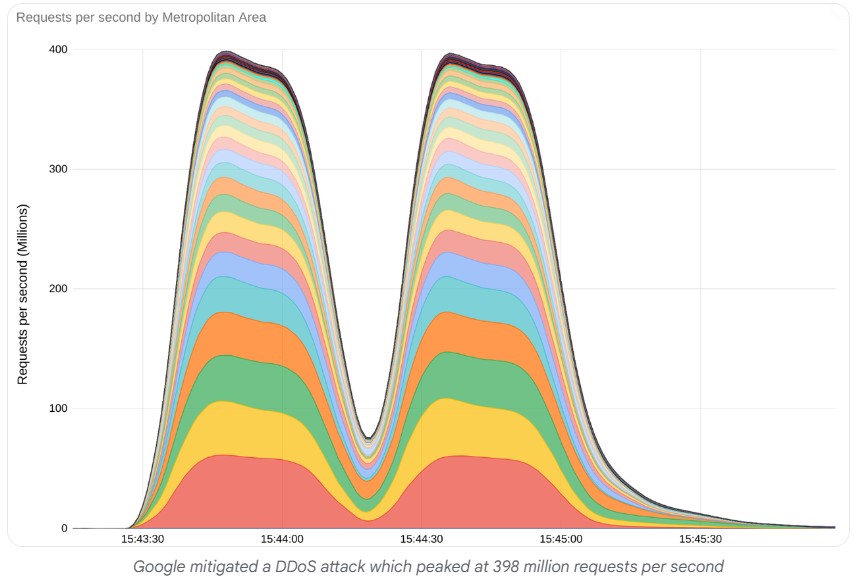
This attack caused several major websites and services to become unavailable, including banks, internet service providers, and social media sites.
GoAnywhere
GoAnywhere is a managed file transfer (MFT) solution developed by Fortra. It allows organizations to centralize and secure their file transfers, regardless of their location.
In March 2023, GoAnywhere suffered a cyberattack by the Clop ransomware group.
Hackers exploited an undisclosed vulnerability in GoAnywhere MFT to gain access to the computer systems of Fortra and its customers. They then encrypted the victims’ data and demanded a ransom in exchange for the decryption key.
Fortra said the attack affected more than 130 organizations worldwide. Victims include businesses, governments and nonprofit organizations.
The attack had a significant impact on the victims’ businesses. Some businesses were forced to suspend their services, causing disruption for their customers.
Fortra has released a patch for the vulnerability exploited by hackers. However, some organizations were unable to recover their data even after applying the patch.
The GoAnywhere attack is a reminder of the growing threat of ransomware cyberattacks. Businesses should take steps to protect themselves against these attacks, including taking regular backups of their data and updating their software regularly.
Coaxis
Coaxis is a French digital services company, specializing in outsourcing, cloud computing, cybersecurity and solution integration. It was founded in 1992 and today has more than 200 employees.
Coaxis is an ISO 9001, ISO 27001 and ISO 22301 certified company. It is also a member of the France Digitale association.
The cyberattack against Coaxis took place on the night of December 7-8, 2023. The hackers used ransomware to encrypt data, which prevented the company from accessing its IT systems.
The hackers demanded a ransom of 10 million euros in exchange for the decryption key. Coaxis refused to pay the ransom, and said it would not negotiate with the pirates.
The attack had a significant impact on the company’s operations. It was forced to suspend its services, causing disruption for its clients, including accounting firms.
Coaxis has implemented a disaster recovery plan to restore its services. The company was able to recover some of its data from backups, but some data was lost.