Internal Pentest VS External Pentest
Penetration testing is a security assessment method that simulates real-world cyberattacks to identify and exploit vulnerabilities in an organization’s systems and networks. Penetration testing can be performed internally, from within the organization’s network, or externally, from outside the network.
Penetration testing is a security assessment method that simulates real-world cyberattacks to identify and exploit vulnerabilities in an organization’s systems and networks. Penetration testing can be performed internally, from within the organization’s network, or externally, from outside the network.
Internal Pentest
An internal pentest is a simulated attack that takes place within an organization’s network, with the pentester assuming the role of a malicious insider.
This type of pentesting provides a comprehensive assessment of an organization’s security posture by identifying and exploiting vulnerabilities that could be exploited by an attacker who has already gained unauthorized access to the network.
Approach
When conducting an internal pentest, the pentester will generally follow a structured approach which involves:
- Information Gathering: Collect as much information as possible about the organization’s network, systems, and security controls.
- Vulnerability Scanning: Scanning the network for known vulnerabilities using automated tools.
- Exploitation: exploit identified vulnerabilities to gain access to systems and elevate privileges.
- Post-exploitation: moving lateral within the network to identify additional vulnerabilities and collect sensitive data.
The results of an internal pentest can be used to identify and remediate vulnerabilities, strengthen internal security controls, and improve overall security posture.
Main features of internal pentesting
- Scope: Can cover the entire internal network or focus on specific areas of interest, such as high-risk systems or critical applications.
- Access: Pentesters typically have authorized access to the network, allowing them to gain deeper insights into the organization’s security posture and exploit vulnerabilities more effectively.
- Results: Focus on vulnerabilities that could be exploited by an insider attacker, such as weak passwords, misconfigured system settings, and unpatched software.
- Objectives: Evaluate the effectiveness of internal security controls, identify vulnerabilities and develop remediation plans.
External Pentest
An external pentest is a simulated attack that takes place from outside an organization’s network, with the pentester attempting to access the network through publicly accessible assets, such as web servers, email servers, and FTP servers.
This type of pentest evaluates the effectiveness of an organization’s external security controls, such as firewalls, intrusion detection systems (IDS), and web application firewalls (WAF).
Techniques
When conducting external pentesting, the pentester will generally follow a similar approach to internal pentesting, but with a focus on vulnerabilities accessible from outside the network. This may involve techniques such as:
- Web Application Testing: Scans websites for vulnerabilities such as cross-site scripting (XSS), SQL injection, and insecure direct object references (IDOR).
- Network reconnaissance: map the perimeter of the organization’s network and identify potential entry points.
- Password cracking: Attempting to gain access to systems using default or weak passwords.
- Social engineering: using various techniques to trick employees into revealing sensitive information or clicking on malicious links.
The results of an external pentest can be used to identify and remediate vulnerabilities, strengthen external security controls, and improve an organization’s overall cybersecurity posture.
Main features of external pentesting
- Scope: Typically focuses on assets accessible over the Internet, but may also include internal assets accessible from the Internet.
- Access: Pentesters do not have authorized access to the network, so they must rely on publicly available information and techniques to identify and exploit vulnerabilities.
- Results: Focus on vulnerabilities that could be exploited by an external attacker, such as misconfigured firewalls, weak passwords, and vulnerable web applications.
- Objectives: evaluate the effectiveness of external security controls, identify vulnerabilities and develop remediation plans.
Differences between Internal Pentest and External Pentest
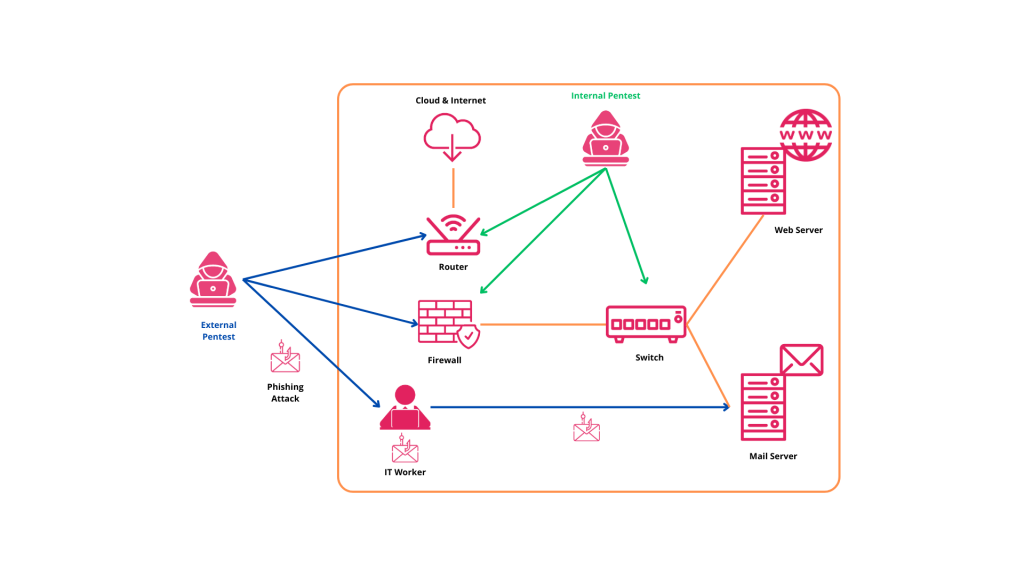
Internal and external pentests have several important differences, including:
The perimeter
Internal pentesting tests the security of an organization’s internal network, including internal applications, workstations, network equipment, etc.
External pentest tests the security of public IP addresses and servers exposed to the Internet.
Access
As mentioned above, pentesters performing internal pentests generally have authorized access to the network, while pentesters performing external pentests do not. This difference in access has a significant impact on the types of vulnerabilities that can be found.
Internal pentesters can exploit vulnerabilities that require authorized access, such as weak passwords, misconfigured system settings, and unpatched software.
External pentesters can only exploit vulnerabilities accessible from the Internet, such as misconfigured web applications, weak utility passwords, and open ports.
The attacker
Internal pentest simulates an internal or external attacker, while external pentest simulates an external attacker.
The objective
The goals of internal and external pentests are similar: to assess the effectiveness of an organization’s security controls and identify vulnerabilities. However, the specific objective of each type of pentest is different due to the different types of attackers.
Internal pentests are typically used to identify vulnerabilities that could be exploited by an insider to steal sensitive data or disrupt operations.
External pentests are typically used to identify vulnerabilities that could be exploited by an external attacker to gain unauthorized access to the network.
The methods
Internal and external pentesting use similar methods, including vulnerability auditing, vulnerability exploitation, and post-exploitation. However, internal pentesting can also use social testing, which simulates human attacks such as phishing or social engineering.
The duration
Internal pentesting generally takes longer than external pentesting because it requires physical access to the organization’s internal network.
The cost
Internal pentesting is generally more expensive than external pentesting because it requires more time and resources.
The settings
When deciding whether to conduct an internal or external penetration test, organizations should consider the severity of the potential impact of a breach, their budget and resources, and their security maturity level.
Organizations very concerned about internal threats may benefit from internal pentesting, while organizations more concerned with external threats may benefit from external pentesting.
Organizations with limited budgets can get away with periodic external pentesting, while organizations with larger budgets can afford internal and external pentesting on a regular basis.
Organizations with a high level of security maturity may be able to identify and remediate vulnerabilities without the need for a penetration test, while organizations with a lower level of security maturity may benefit from more frequent intrusion tests.
Table of differences between External Pentest and Internal Pentest
| Criteria | Internal Pentest | External Pentest |
|---|---|---|
| Perimeter | Internal network, internal applications, workstations, network equipment | Public IP adresses, servers exposed on the internet |
| Access | Remote or on-site | Remote |
| Attacker | Internal or external attacker | External attacker |
| Objective | Identify vulnerabilities exploitable by an internal or external attacker | Identify vulnerabilities exploitable by an external attacker |
| Methods | Vulnerability audit, vulnerability exploitation, post-exploitation, social testing | Vulnerability audit, vulnerability exploitation, post-exploitation |
| Results | Vulnerabilities that can be exploited by an external attacker | Vulnerabilities that can be exploited by an insider |
| Duration | Usually longer | Generally shorter |
| Cost | Usually more expensive | Generally cheaper |
| Settings | Budget and resources, security maturity level of the organization | Severity of potential impact of a breach, organization’s budget and resources, organization’s security maturity level |
Choice of pentest type
The decision to perform an internal or external penetration test depends on the specific security needs and risk profile of the organization.
Organizations with a high risk of insider threats or a complex internal network may benefit from internal pentesting.
Organizations at high risk of external attacks or that focus on internet-accessible assets may benefit from external pentesting.
In some cases, internal and external penetration testing can be performed to provide a comprehensive assessment of an organization’s security posture.
The choice of the type of pentest to perform depends on the needs and objectives of the organization.
In general, an internal pentest is recommended for organizations that want to:
- Test the security of their entire internal network, including configuration vulnerabilities, software vulnerabilities and physical vulnerabilities.
- Test the security of their organization against internal and external attacks.
- Identify vulnerabilities that could be exploited by an attacker to access sensitive data or disrupt the organization’s operations.
An external pentest is recommended for organizations that wish to:
- Test the security of their servers exposed on the Internet.
- Identify vulnerabilities that could be exploited by an attacker to access sensitive data or disrupt the organization’s operations.
It is also possible to combine an internal pentest and an external pentest to obtain more complete coverage of the security of the information system.
Examples of Internal Pentest and External Pentest
Examples of Internal Pentest
An internal pentest could identify:
- A configuration vulnerability on an internal server that would allow an attacker to connect to it without authentication.
- A software vulnerability on an internal application that would allow an attacker to steal sensitive data.
- A physical vulnerability on an organization’s building that would allow an attacker to break into the internal network.
Examples of External Pentest
An external pentest could identify:
- A configuration vulnerability on a web server exposed to the Internet that would allow an attacker to take control of the server.
- A software vulnerability on a website exposed to the Internet that would allow an attacker to steal sensitive data.
- A physical vulnerability on a network infrastructure exposed on the Internet that would allow an attacker to disrupt operations.
