Browser Extensions – Real dangers in Cybersecurity
On Chrome, you can download extensions, which offer functions not provided as standards in the browser.
Some can be very useful, however others are dangerous and malicious.
In this blog post, we will see the problem of these search browser extensions, with different examples.
Google Chrome is currently the leader among search browsers with a market share of 64%, the followed by Safari with 19% (source: blog du moderareur).
On Chrome, you can download extensions, which offer functions not provided as standards in the browser.
Some can be very useful, however others are dangerous and malicious.
In this blog post, we will see the problem of these search browser extensions, with different examples.
Browser extensions
A browser extension is a plug-in that, when installed, allows you to add one or more features.
There are thousands of extensions with different purposes, some block ads (the famous Adblock), others check spelling, while others provide an Artificial Intelligence (AI) assistant. or convert a file from one format to another format (PDF converter for example).
In short, these extensions bring real added value to Internet users by providing them with new useful or aesthetic options and functionalities.
These plug-ins are easily found by searching for them in search engines (which we strongly advise against), or by going through official stores such as the Google Web Store, a store bringing together extensions validated by Google.
But be careful, just because Google approves an extension does not mean it is 100% secure, as we will see later in this article.
The problem of browser extension rights
Extensions therefore modify search browsers to add new possibilities and capabilities.
To do this, they must have the rights to read and modify the data collected on the sites.
To demonstrate this, we will use the official store of the most used search browser in the world, Google Chrome and its Google Web Store.
Save to Google Drive
Let’s take the example of an extension offered by Google itself, the “Save to Google Drive” extension.
Once installed in Chrome, it can save web content or photos directly to Google Drive.
However, when you click on “Add to Chrome”, a warning appears.
The warning states that “This Chrome extension may:
Read and edit all your data across all websites
Show notifications »
But that’s not all it does: if we go to the “Privacy Practices” tab on the extension’s page in the Chrome Web Store, we can see that the extension allows itself other rights.
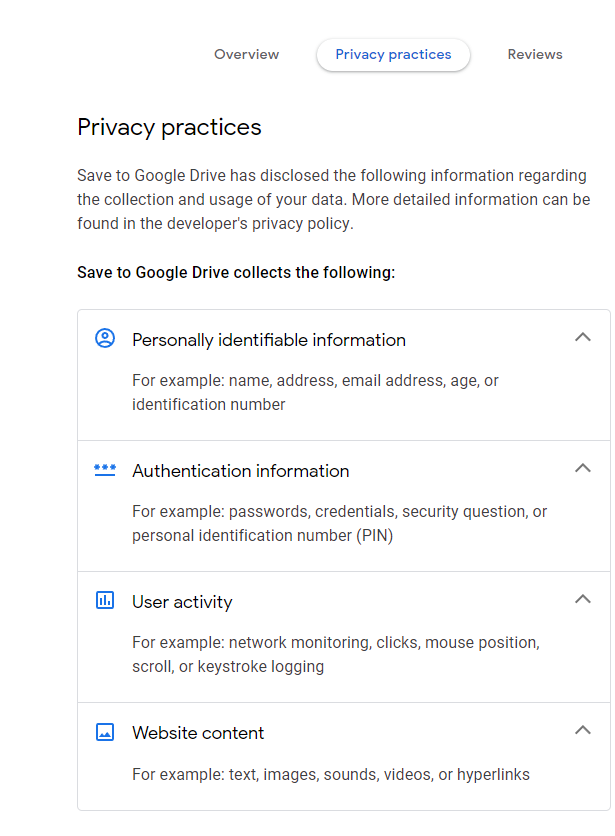
Indeed, the “Save to Google Drive” plug-in is authorized to collect the following user data:
- Information that personally identifies the user: name, address, e-mail address or age.
- Authentication information : for example: passwords, credentials, security question, or personal identification number (PIN).
- User activity : for example: network monitoring, clicks, mouse position, scroll, or keystroke logging.
- Website content : for example: text, images, sounds, videos, or hyperlinks.
So even an official Google extension requires numerous authorizations.
DeepL Translate
Let’s take the example of another plugin, a plugin downloaded more than 2,000,000 times, the DeepL translator.
Here too, when we click on “Add to Chrome”, we have a similar warning.
The warning states that “This Chrome extension may:
Read and edit all your data on all websites »
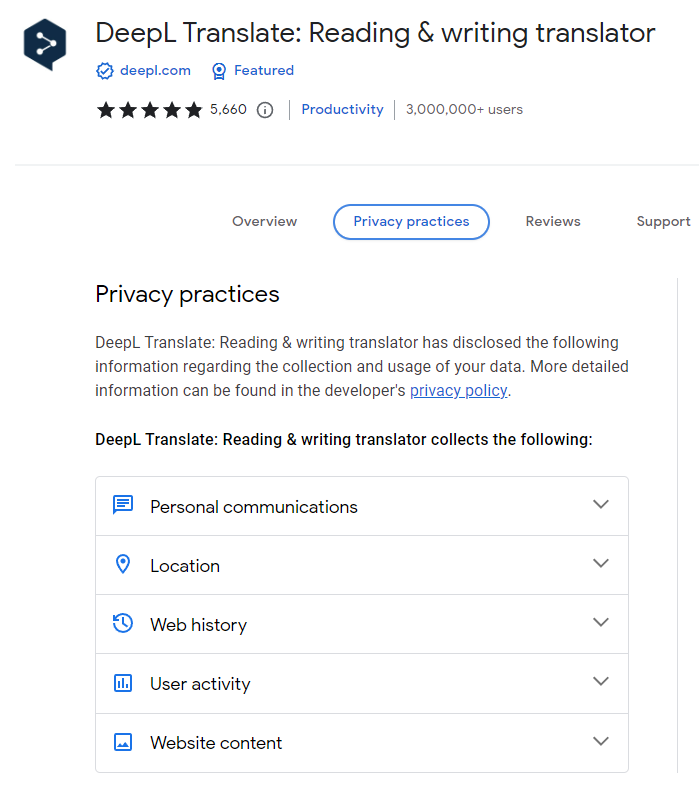
And there too, when we check in the “Privacy practices” tab, it’s easy to see that DeepL Translator requires further permissions and collects various data:
- Personal communications : for example: emails, texts, or chat messages.
- Location : for example: region, IP address, GPS coordinates, or information about things near the user’s device.
- Web history : the list of web pages a user has visited, as well as associated data such as page title and time of visit.
- User activity : for example: network monitoring, clicks, mouse position, scroll, or keystroke logging.
- Website content : for example: text, images, sounds, videos, or hyperlinks.
As we have seen, extensions request a lot of information and can modify the browser itself.
And when we offer so many rights to extension developers, it seems obvious that malicious people will take advantage of them.
Examples of dangerous browser extensions
Last July, researchers at Kapersky discovered that 34 extensions, present on the official Google Chrome store, the Google Web Store, were malicious.
That may not sound like much, but it represents no less than 87 million downloads.
One of them, called Autoskip for YouTube, represents 9 million downloads alone.
What was malicious about them? Quite simply, they had “additional functionalities”.
By this we mean that the extension does more than just what it was downloaded to do.
Here is the list of 34 extensions, it is essential to uninstall them as quickly as possible, knowing that Google has banned them from the Google Web Store:
- Adblock Dragon
- Alfablocker ad blocker
- Amazing Dark Mode
- Autoskip for Youtube
- Awesome Auto Refresh
- Base Image Downloader
- Brisk VPN
- Clickish fun cursors
- Clipboard Helper
- Craft Cursors
- Crystal Adblock
- Cursor-A custom cursor
- Easy Undo Closed Tabs
- Easyview Reader view
- Epsilon Ad blocker
- Font Customizer
- HyperVolume
- Image download center
- Leap Video Downloader
- Light picture-in-picture
- Maxi Refresher
- Maximum Color Changer for Youtube
- OneCleaner
- PDF Toolbox
- Qspeed Video Speed Controller
- Quick Translation
- Readl Reader mode
- Repeat button
- Screence screen recorder
- Soundboost
- Tap Image Downloader
- Venus Adblock
- Volume Frenzy
- Zoom Plus
What are the risks of installing malicious browser extensions?
Well, this depends very much on the extension, and can range from highly intrusive advertising to pure malware installation and theft of confidential data.
Adding advertisements
The malicious plug-in will insert more or less legal (rather less than more) intrusive ads into your browsing experience, all based on the user’s browsing path.
The extension publisher obviously takes commissions when a user clicks on the ad.
Another way is replacing addresses in search results with links to advertisements.
Editing the Search page
Some extensions, when installed, will replace the basic Google Search page with a WebSearch page.
This change of search engine enables criminals to record and analyze the searches made by users, in order to propose more relevant links on the new Web Search page and thus carry out targeted advertising.
Data capture and theft
A more serious case is the capture and theft of data.
Extensions to take screenshots, activate a computer’s microphone or camera, steal banking data and identifiers.
For example, the group of Cookie-stealing extensions, named FB Stealer, pretended to be a Google Trad extension once installed and stole the user’s session cookies when they visited Facebook.
This enabled cybercriminals to steal and capture user IDs in order to send messages to the victim’s relatives via the social network.
Phishing
Malicious plug-ins can redirect victim users, who have downloaded the extension, to fake sites, such as phishing campaigns, with the aim of stealing identifiers, confidential or banking information, believing that it was an official site.
Installing malware
A fairly simple way for hackers to install malware on the victim’s computer is to take them to a site where a script is downloaded and installed on their computer.
Protect yourself effectively from malicious browser extensions
First of all, we advise you now to go through all your extensions and check their legitimacy and reliability.
Be careful, some of these plug-ins cannot be uninstalled that easily.
Even if you remove the extension from your search browser, it will reinstall itself every time you reopen your web browser.
To avoid downloading a dangerous search browser extension, here are several tips to put into practice:
- Never download extensions outside the official stores like the Google Web Store. Indeed, Google checks before putting it online, and regularly removes questionable extensions.
- Check customer reviews. While this doesn’t mean that a popular extension isn’t dangerous, it does limit the risks quite a bit.
- Check the developer, his reliability and his reputation.
- Update your extensions regularly and uninstall extensions that are unused or unfamiliar to you.
- Install tools to protect yourself from data theft or the installation of malware.
