CVE May 2024
Discover several CVEs that marked the month of May 2024. They were selected based on their CVSS severity score and their EPSS exploitability score.
Computer attacks are increasingly common and sophisticated and use security vulnerabilities present in information systems. A CVE is a unique identifier assigned to a computer security vulnerability. The CVE repository makes it possible to centralize information on these vulnerabilities and facilitate their management by security actors.
Discover several CVEs that marked the month of May 2024. They were selected based on their CVSS severity score and their EPSS exploitability score.
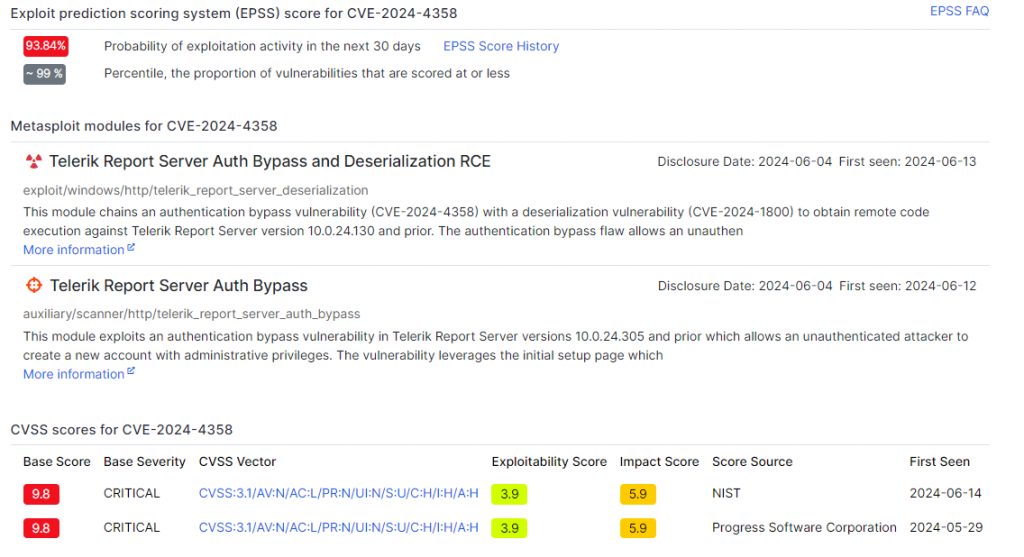
CVE-2024-4358
CVE-2024-4358 is a critical authentication bypass security vulnerability affecting Progress Telerik Report Server, a reporting solution widely used by enterprises. This flaw allows an unauthenticated attacker to access restricted functionality of the Report Server, which could lead to serious consequences, such as malicious code execution, theft of sensitive data, or complete system takeover.
This flaw has a CVSS severity score of 9.8/10 and an exploitability score of 93.84 %, demonstrating that 93% of other flaws are less likely to be exploited.
What does the flaw do?
The flaw lies in the authentication mechanism of Telerik Report Server, which allows users to connect to the server and access its features. A crafty attacker can exploit a vulnerability in this process to bypass the authentication process and gain unauthorized access to the server.
Potential consequences
Exploitation of this vulnerability can have major repercussions on an organization:
- Theft of sensitive data: An attacker can access confidential information stored on the reporting server, such as financial data, customer information, or company secrets.
- Execution of malicious code: The attacker can execute arbitrary code on the server, allowing them to install malware, modify critical files, or disrupt system operation.
- Server Takeover: In the worst case, the attacker can take full control of the report server, giving them access to the entire network and all the data it contains.
Discovery and disclosure
The flaw was discovered and responsibly reported to Progress by an anonymous researcher in May 2024. A PoC (proof of concept) exploit was released shortly after, making it easier for attackers to exploit the flaw.
Progress reaction
Progress responded promptly to the disclosure of the flaw by releasing a patch in version 2024 Q2 (10.1.24.514) of Telerik Report Server. It is crucial to apply this patch as soon as possible to mitigate the risk of exploitation.

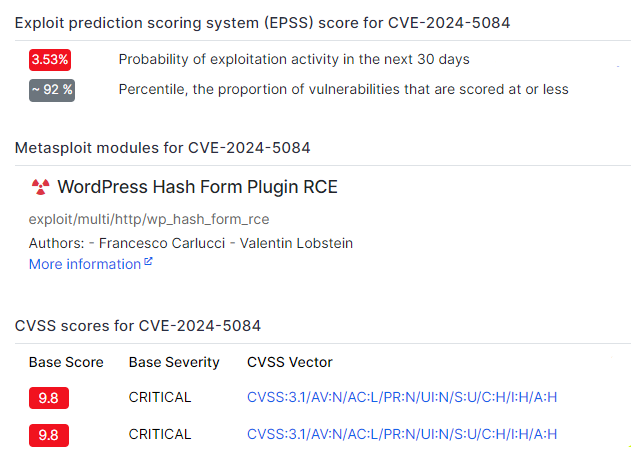
CVE-2024-5084
CVE-2024-5084 flaw affects the Hash Form – Drag & Drop Form Builder plugin for WordPress, introducing a major security risk for websites that use it. This flaw allows an unauthenticated attacker to upload arbitrary files to the site’s server, opening the door to remote code execution (RCE) and complete system takeover.
This flaw has a CVSS severity score of 9.8/10 and an exploitability score of 3.53%, demonstrating that 92% of other flaws are less likely to be exploited.
What does the flaw do?
The flaw lies in the file_upload_action function of the plugin, responsible for processing files uploaded via forms created with Hash Form. Without proper file type validation, an attacker can bypass restrictions and introduce malicious files, such as PHP scripts, which will be executed on the server during processing.
Potential consequences
Successfully exploiting this flaw can have disastrous consequences for a WordPress site. An attacker who has taken control of the server can:
- Steal sensitive data: Access confidential information stored in the site’s database, including user passwords, financial data or personal information.
- Install malware: Deploy malware on the server to mine cryptocurrencies, spread spam, or carry out denial of service (DDoS) attacks.
- Website hijack: Alter site content, spread disinformation, or redirect users to malicious websites.
- Take control of the system: Access other servers on the network and extend the scope of the attack.
Operation and proof of concept
Proofs of concept (PoC) exploiting this flaw are already available online, making it easier for attackers. Common exploitation involves sending a POST request to the file_upload_action function with a carefully crafted malicious file. Once downloaded, the file will be executed on the server, allowing the attacker to execute arbitrary code.
Impact and urgency of the update
The impact of this flaw is critical. The ease of exploitation and the serious potential consequences make it particularly dangerous. It is crucial to update the Hash Form plugin to version 1.1.1 or later as soon as possible. This version fixes the CVE-2024-5084 flaw and protects websites from danger.

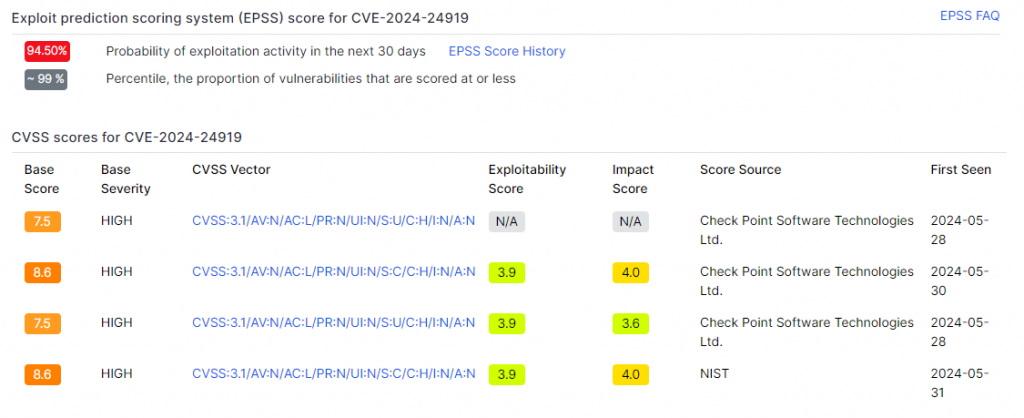
CVE-2024-24919
CVE-2024-24919 is a disclosed information vulnerability that affects Check Point Security Gateways. This critical flaw allows an unauthenticated, remote attacker to read arbitrary files on the compromised device, thereby exposing sensitive data and compromising network security.
This flaw has a CVSS severity score of 8.6/10 and an exploitability score of 94.50%, demonstrating that more than 99% of other flaws are less likely to be exploited.
What does the flaw do?
The vulnerability lies in a buffer overflow in the firmware of Check Point security gateways. This override can be triggered by sending a malicious HTTP request to the vulnerable device. Once exploited, the flaw allows the attacker to execute arbitrary code on the device, giving them full access to internal files and systems.
Potential consequences
Successful exploitation of this vulnerability can have disastrous consequences for organizations using Check Point security gateways:
- Theft of sensitive data: Access to passwords, encryption keys, confidential customer or company information.
- System Takeover: The attacker can take full control of the gateway, reconfigure it, disable protections, or use it as a point of attack for other systems on the network.
- Bounce Attacks: The compromised gateway can serve as a springboard to launch denial of service attacks, internal network intrusions, or data exfiltration.
Mitigation measures
To limit the risks of exploiting this flaw, it is crucial to put in place several security measures:
1. Apply Check Point security patch
The top priority is to apply the patch released by Check Point as soon as possible. This patch closes the vulnerability and protects your security gateways.
2. Disable Remote VPN Access and Mobile Access Blade Software
While these features are not essential, disabling them removes a potential attack vector for cybercriminals.
3. Limit SSH access to security gateways
Restricting SSH access to trusted IP addresses significantly reduces the attack surface and limits malicious intrusion attempts.
4. Regularly update gateway firmware
Keeping firmware up to date ensures that the latest protections against known vulnerabilities are in place.
5. Monitor security gateways for suspicious activity
Implementing monitoring systems helps detect unusual behavior and intrusion attempts on gateways, enabling rapid response to potential incidents.

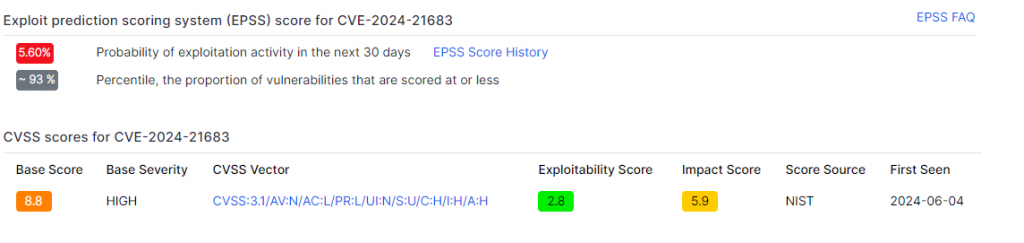
CVE-2024-21683
CVE -2024-21683 is a critical vulnerability affecting Atlassian Confluence Server and Data Center software. This remote code execution (RCE) flaw allows an authenticated attacker to execute arbitrary code on the targeted server, without any user interaction.
This flaw has a CVSS severity score of 8.8/10 and an exploitability score of 5.60%, demonstrating that 93% of other flaws are less likely to be exploited.
What does the flaw do?
This flaw lies in Confluence’s processing of JavaScript files. An attacker can exploit the flaw by injecting malicious JavaScript code into a specific file, accessible to an authenticated user. Once executed, this JavaScript code can take control of the server, thereby compromising the entire system.
Potential impact
The consequences of successful exploitation of this flaw are serious:
- Theft of sensitive data: The attacker can access all data stored on the Confluence server, including confidential information such as financial data, personal information or company secrets.
- Server takeover: The attacker can take full control of the Confluence server, allowing him to perform any action, install malware, modify or delete files, or spy on users.
- Disruption of services: The attacker can disrupt or disable the Confluence server, leading to system unavailability and significant financial losses.
- Attack propagation: The attacker can use the compromised server as a starting point to attack other systems on the network.
Reduction measures
The best way to protect against this vulnerability is to apply the following Atlassian patches as soon as possible:
- Confluence Server and Data Center 7.18.1.
- Confluence Server and Data Center 7.17.7.
- Confluence Server and Data Center 7.16.8.

CVE-2024-3495
CVE-2024-3495 flaw seriously affects the Country State City Dropdown CF7 plugin for WordPress. This SQL injection flaw allows an unauthenticated attacker to inject malicious code into the targeted website, giving them access to sensitive information and potential control over the site.
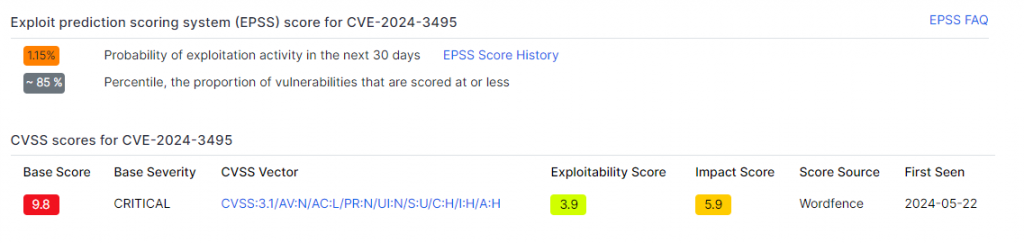
This flaw has a CVSS severity score of 9.8/10 and an exploitability score of 1.15%, demonstrating that 85% of other flaws are less likely to be exploited.
What does the flaw do?
Dropdown CF7 plugin allows users to easily add country, state, and city selector fields to their WordPress forms. Unfortunately, poor handling of user settings in versions 2.7 and earlier created a critical security vulnerability.
A malicious attacker can exploit this flaw by injecting SQL code into the “cnt” or “sid” parameters of a request to the plugin. This SQL code can then be executed against the website database.
Exploitation of the flaw
Exploitation of this flaw does not require any action on the part of the website administrator. An attacker can simply create a malicious web page containing a link to the vulnerable plugin. When a user clicks on this link, their browser sends a request to the plugin, including the parameters manipulated by the attacker. The injected SQL code is then executed against the site’s database, potentially compromising site security.
Impact and consequences
The attacker can achieve:
- Theft of sensitive data: Accessing usernames, passwords, email addresses, financial information and other data stored in the database.
- Site Takeover: Obtain administrator privileges, modify site content, install malware, or redirect users to malicious websites.
- Disruption of the site: Disfigure the site, make it inaccessible or cause errors.
- User Spying: Monitor users’ activities on the website, steal their cookies or track their sessions.
Update and mitigation
The best protection against this flaw is to update the Country State City Dropdown plugin to version 2.8 or later, which fixes the vulnerability.

CVE-2024-2876
CVE-2024-2876 is a critical severity SQL injection (SQLi) vulnerability affecting the WordPress plugin “Email Subscribers by Icegram Express”. This flaw allows an unauthenticated attacker to inject arbitrary SQL queries into the plugin, giving them access to sensitive information such as user data and passwords.
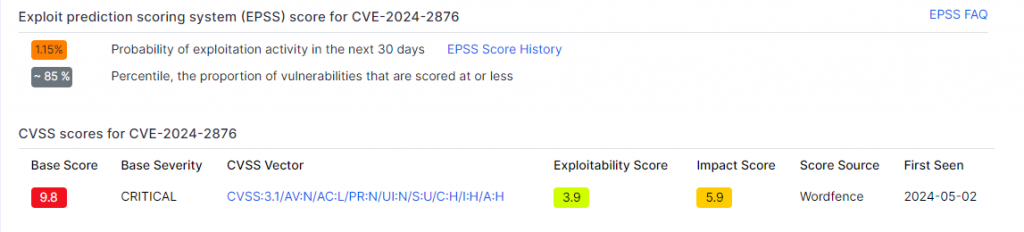
This flaw has a CVSS severity score of 9.8/10 and an exploitability score of 1.15%, demonstrating that 85% of other flaws are less likely to be exploited.
What does the flaw do?
SQL injection (SQLi) is a type of attack that exploits security vulnerabilities in web applications to execute malicious SQL queries.
In the case of the CVE-2024-2876 flaw, the flaw is found in the run( ) function of the IG_ES_Subscribers_Query class of the plugin. This function is responsible for executing SQL queries against the WordPress database.
Exploitation of the flaw
An attacker can exploit the CVE-2024-2876 flaw by sending a specially crafted HTTP request to the plugin. The query may contain a malicious parameter which will then be included in an SQL query by the plugin. The attacker can thus modify the SQL query to perform unauthorized actions, such as retrieving sensitive data or executing commands on the server.
Potential consequences
Successful exploitation of CVE-2024-2876 can have serious consequences for an affected WordPress website. The attacker can:
- Installation of malware: The attacker can install malware on the website, which can give them complete control over the site.
- Theft of sensitive data: The attacker can access user data, such as names, email addresses, passwords, and payment information.
- Website Hijacking: The attacker can redirect users to malicious websites or modify the content of the website.
Affected versions and solution
All versions of the Email plugin Subscribers by Icegram Express up to and including version 5.7.14 are affected by this flaw. The flaw has been corrected in version 5.7.15 of the plugin. It is crucial to update the plugin as soon as possible to protect against this flaw.

CVE-2024-23692
CVE-2024-23692 flaw severely affects Rejetto HTTP File Server, a widely used open source HTTP file server. This template injection vulnerability allows an unauthenticated, remote attacker to execute arbitrary commands on the targeted system, opening the door to complete takeover and disastrous consequences.
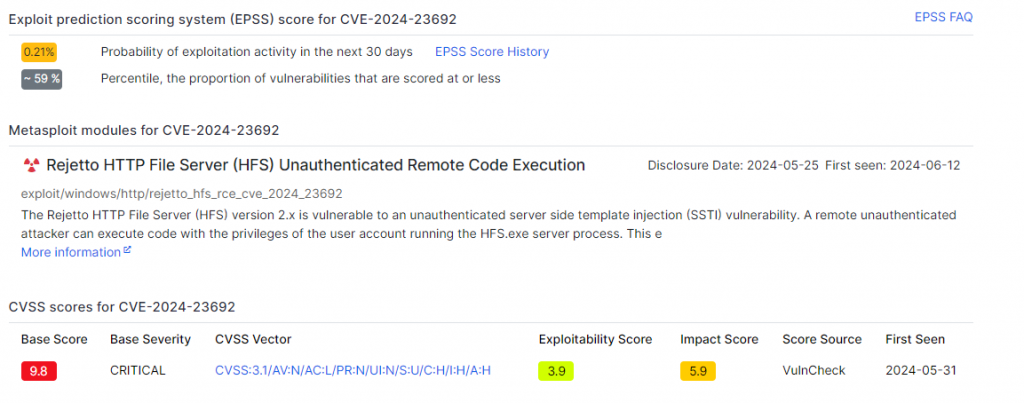
This flaw has a CVSS severity score of 9.8/10 and an exploitability score of 0.21%, demonstrating that 59% of other flaws are less likely to be exploited.
What does the flaw do?
Exploitation of the CVE-2024-23692 flaw relies on the injection of malicious code into the web page templates used by Rejetto HTTP File Server. These models, dynamically generating the content of web pages, are vulnerable to manipulation by an attacker. By injecting malicious code into these templates, the attacker can force the server to execute this code when a user visits an affected web page.
Potential attack scenarios
An attacker who exploited this flaw can carry out a multitude of malicious actions, such as:
- Malware installation: The attacker can install malware on the targeted system, enabling data theft, account takeover, spying, or data encryption via ransomware.
- Exfiltration of sensitive data: The attacker can access confidential data stored on the server, such as financial information, personal data or company secrets.
- System disruption: The attacker can disrupt the normal operation of the server, causing service outages, data corruption or denials of service.
- Complete Takeover: In the worst case, the attacker can take full control of the system, allowing them to perform any action with administrative privileges.
Impact and urgency of the situation
The severity of the CVE-2024-23692 flaw should not be underestimated. Successful exploitation of this vulnerability can have devastating consequences for individuals, organizations, and critical infrastructure. It is crucial to put in place urgent corrective measures to mitigate the risks associated with this vulnerability.
Affected versions and solutions
The CVE-2024-23692 flaw affects all versions of Rejetto HTTP File Server prior to version 2.4. The most effective solution is to immediately upgrade to version 2.4, which fixes the vulnerability.

CVE-2024-25641
Cacti is a widely used open-source network monitoring tool for monitoring the performance and health of computer networks.
CVE-2024-25641 flaw seriously affects the Cacti network monitoring software, widely used by companies and organizations. This security flaw, classified as remote arbitrary code execution (RCE), allows a malicious attacker to take complete control of a compromised Cacti server, leading to potentially disastrous consequences.
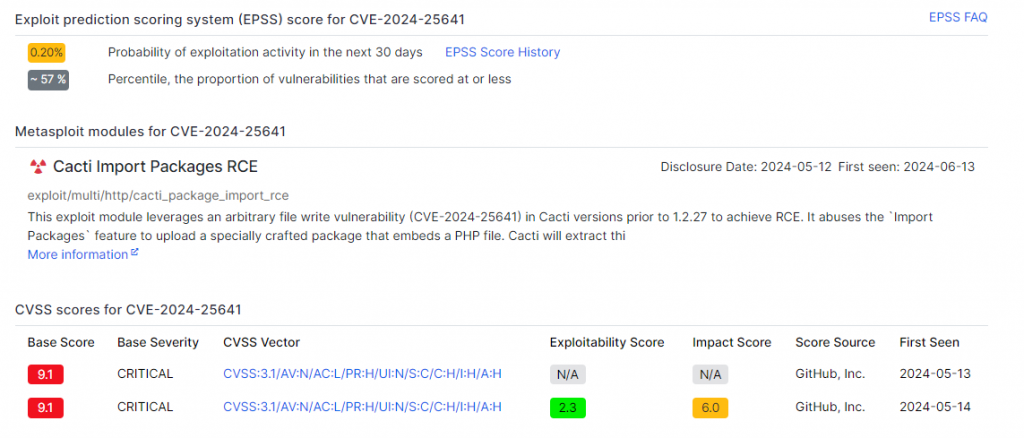
This flaw has a CVSS severity score of 9.1/10 and an exploitability score of 0.20%, demonstrating that 57% of other flaws are less likely to be exploited.
What does the flaw do?
The origin of the vulnerability lies in inadequate handling of escape characters in the /lib/import.php library of the Cacti package import component. This component is designed to allow authorized users to import predefined configuration templates to simplify software configuration. However, due to the flaw, a user authenticated with the “Import Templates” privilege can exploit this functionality to introduce arbitrary PHP code into the system.
Exploitation and consequences
An attacker can craft a malicious package containing malicious PHP code and import it into Cacti taking advantage of the flaw. Once the package is imported, the malicious PHP code executes on the Cacti server, providing the attacker with full control over the system. This control can be used for various nefarious purposes, such as:
- Theft of sensitive data: The attacker can access confidential information stored on the Cacti server, including login credentials, financial data or sensitive personal information.
- System hijacking: The attacker can use the compromised Cacti server as a platform to launch denial of service (DoS) attacks, distribute malware, or compromise other systems on the network.
- Spying and Monitoring: The attacker can install monitoring tools on the Cacti server to spy on user activities and steal additional information.
Affected versions and solutions
Cacti versions prior to 1.2.27 are vulnerable to CVE-2024-25641. To fix this issue, it is crucial to update Cacti to version 1.2.27 or later as soon as possible. This update applies a fix that neutralizes the vulnerability and protects the system against attacks.

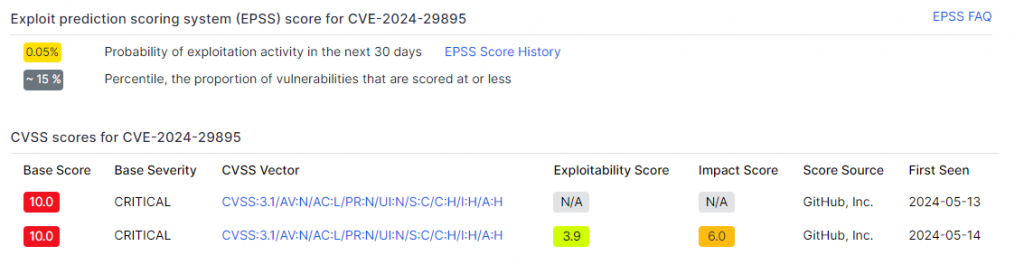
CVE-2024-29895
Recently, a critical severity command injection flaw was discovered in the 1.3.x DEV branch of Cacti. This flaw allows an unauthenticated user to execute arbitrary commands on the server, which can result in a complete system takeover by an attacker.
This flaw has a CVSS severity score of 10/10 and an exploitability score of 0.05%, demonstrating that only 15% of other flaws are less likely to be exploited. He is therefore of critical severity but is not easily exploitable.
Understanding the flaw
The origin of the vulnerability lies in the use of the register_argc_argv function of PHP, which allows additional arguments to be passed to the PHP script. This feature is enabled by default in the 1.3.x DEV branch of Cacti, making it vulnerable to command injection attacks.
Exploitation of the flaw
An attacker can exploit this flaw by sending a specially crafted HTTP request to Cacti. The request must contain malicious arguments which will then be executed by the Cacti server. The attacker can thus execute arbitrary commands on the system, allowing him to install malware, steal sensitive data or even take complete control of the server.
Impact of the fault
The consequences of exploiting this flaw are serious. An attacker can:
- Install malware to mine cryptocurrencies, steal sensitive information or disrupt system operation.
- Steal confidential data such as credentials, financial data or company secrets.
- Take complete control of the server, using it as a base for other attacks or to distribute malware across the network.
Affected versions
Only the 1.3.x DEV branch of Cacti is affected by this flaw. Stable versions (1.2.x and earlier) are not vulnerable.

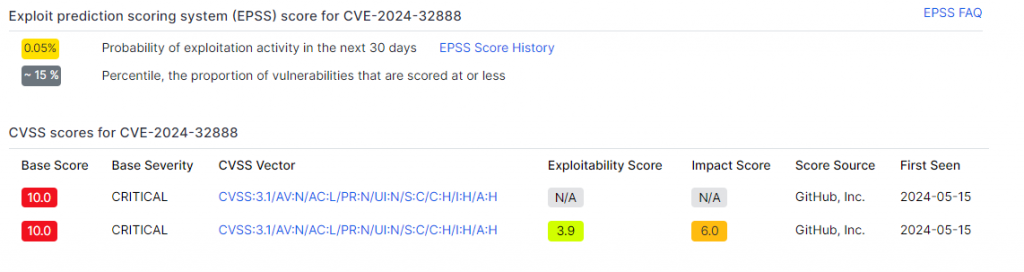
CVE-2024-32888
CVE-2024-32888 affects the Amazon JDBC driver for Redshift, a crucial component allowing Java applications to interact with Redshift databases. This security flaw, classified as critical, exposes systems to malicious intrusions with potentially disastrous consequences.
This flaw has a CVSS severity score of 10/10 and an exploitability score of 0.05%, demonstrating that only 15% of other flaws are less likely to be exploited. He is therefore of critical severity but is not easily exploitable.
What does the flaw do?
The origin of the vulnerability lies in an insufficient neutralization of special characters within SQL queries. A clever attacker can exploit this flaw to inject arbitrary SQL code into a legitimate query, allowing them to manipulate sensitive data stored in the database.
Potential impact
The repercussions of successful exploitation of CVE-2024-32888 are considerable:
- Theft of confidential data: An attacker can access, modify or steal sensitive information such as financial data, personal information or company secrets.
- Execution of malicious code: The flaw allows the execution of arbitrary commands on the database server, opening the door to the installation of malware, data corruption or exfiltration of sensitive data.
- Server disruption or deactivation: Exploitation of the flaw can lead to server saturation, service outages or even complete system deactivation, seriously impacting business continuity.
Affected versions and solutions
CVE-2024-32888 affects versions of the Amazon JDBC driver for Redshift prior to 2.1.0.28. To address this vulnerability, it is imperative to update the driver to the latest available version (currently 2.1.0.28) or later.

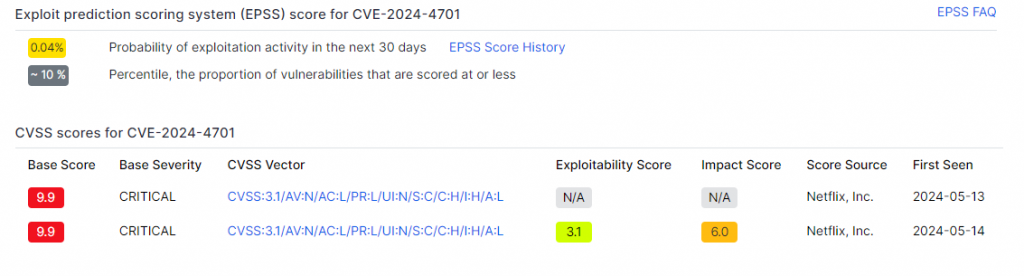
CVE-2024-4701
CVE-2024-4701 is a high-severity directory traversal security vulnerability affecting Genie versions prior to 4.3.18. This flaw allows a malicious attacker to execute arbitrary code on a vulnerable server, which can lead to serious consequences such as data theft, system takeover, and denial of service.
This flaw has a CVSS severity score of 9.9/10 and an exploitability score of 0.04%, demonstrating that only 10% of other flaws are less likely to be exploited. He is therefore of critical severity but is not easily exploitable.
What does the flaw do?
Genie’s mechanism for processing multipart / form -data requests. By manipulating the file name and content of a multipart / form -data request, an attacker can force the application to write a malicious file to an arbitrary location on the server. If the Java process running Genie has the necessary write permissions, the attacker can exploit this flaw to execute arbitrary code with the privileges of the Java process.
Potential attack scenario
Imagine a scenario where an attacker sends a multipart / form -data request to a vulnerable Genie server. The request contains a malicious file named myfile.jsp and a path parameter set to .. /../../../ etc / passwd. By exploiting the directory traversal flaw, the attacker can trick Genie into writing the myfile.jsp file to the server’s / etc directory. If the Java Genie process has write permissions to this directory, the attacker can execute malicious JSP code, giving them unauthorized access to sensitive system files such as the / etc / passwd file containing passwords users.
Impact of exploitation
Successful exploitation of this vulnerability can have disastrous consequences for organizations and individuals. Potential impacts include:
- Data theft: The attacker can access sensitive data such as user credentials, financial data or company secrets.
- Remote Code Execution (RCE): The attacker can execute any code on the vulnerable server, giving them full control over the system.
- System Takeover: The attacker can take complete control of the server, using it to distribute malware, launch denial of service attacks, or carry out other malicious activities.
- Denial of Service (DoS): The attacker can overwhelm the server with malicious requests, making it unavailable to legitimate users.
Mitigation measures and fixes
The best way to protect against this critical flaw is to apply the security patch provided by Netflix. Updating Genie to version 4.3.18 or later eliminates the vulnerability and protects the system against attacks based on CVE-2024-4701.
