What are CVEs?
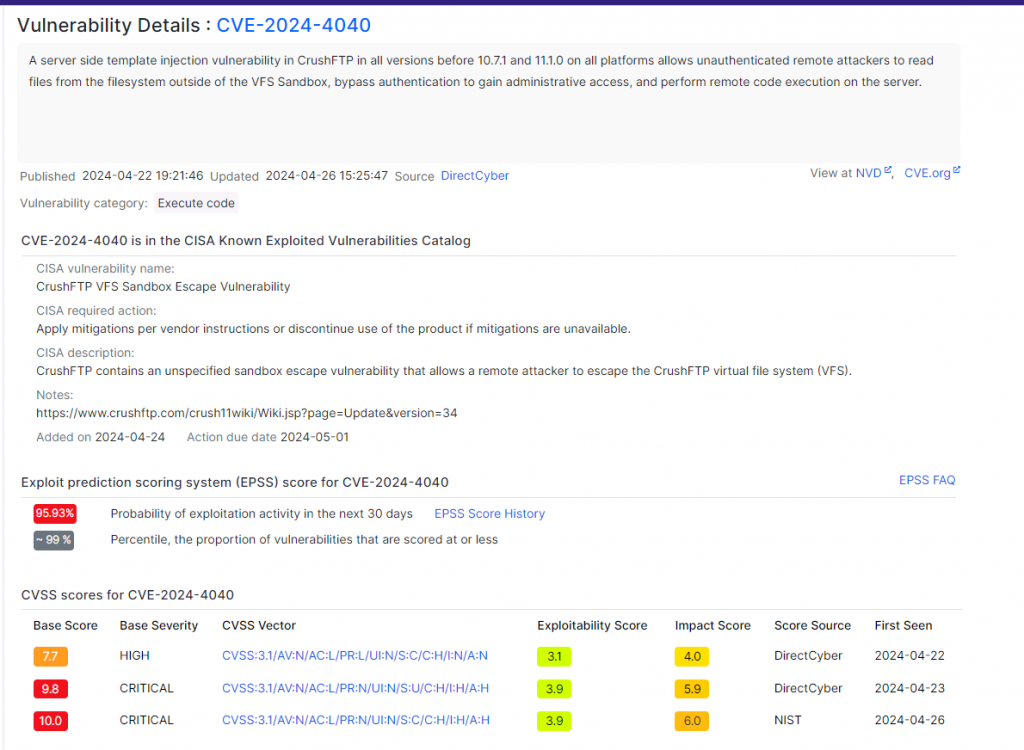
A CVE is a unique identifier assigned to each software security vulnerability listed in a public database maintained by MITRE.
In cybersecurity, it is crucial to have common tools and repositories to identify, classify and communicate security vulnerabilities. This is where CVE (Common Vulnerabilities & Exposures) comes in, a public dictionary that plays a vital role in combating cyberthreats.
Who manages the CVE database and how are identifiers assigned?
Vulnerabilities and Exposures (CVE) identifiers are assigned by a global network of CVE Numbering Authorities (CNAs). There are 376 CNAs, operating in 41 different countries, each responsible for a specific product area or technology. The list of CNAs is here.
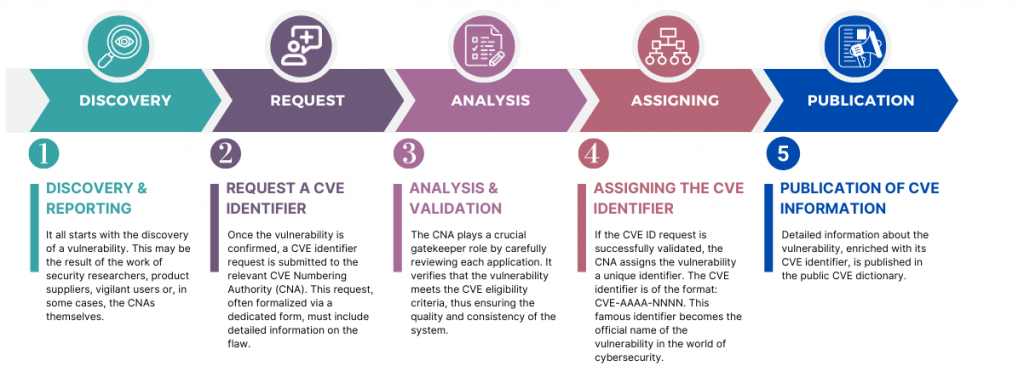
Here are the key steps for assigning a CVE identifier:
1. Discovery and reporting
It all starts with the discovery of a vulnerability. This may be the result of the work of security researchers, product suppliers, vigilant users or, in some cases, the CNAs themselves.
The discovered flaw must then be confirmed and analyzed in order to understand its exact nature, its potential impact and the products or components affected.
2. Request a CVE identifier
Once the vulnerability is confirmed, a CVE identifier request is submitted to the relevant CVE Numbering Authority (CNA). This request, often formalized via a dedicated form, must include detailed information on the flaw, such as:
- Precise description of the vulnerability : nature of the flaw, operating code, affected components, etc.
- Analysis of the potential impact : severity of the fault, risks incurred, affected populations, etc.
- Demonstration of uniqueness : comparison with existing CVEs to avoid duplicates.
- Evidence of remediation : existence of a fix or workaround.
3. Analysis and validation by the CNA
The CNA plays a crucial gatekeeper role by carefully reviewing each application. It verifies that the vulnerability meets the CVE eligibility criteria, thus ensuring the quality and consistency of the system.
There are many points to watch out for:
- Proven severity : The vulnerability must present a sufficient level of severity to justify a CVE identifier.
- Concrete impact : The vulnerability must affect a product or component actually used.
- Possible fix : There must be a way to fix or work around the flaw.
- Compliance with the rules : The request must respect the rules and formats defined by the CVE system.
4. Assigning the CVE identifier
If the CVE ID request is successfully validated, the CNA assigns the vulnerability a unique identifier.
The CVE identifier is of the format: CVE-AAAA-NNNN , where AAAA corresponds to the year of discovery and NNNN , a sequential unique number.
This famous identifier becomes the official name of the vulnerability in the world of cybersecurity.
5. Publication of CVE information
Detailed information about the vulnerability, enriched with its CVE identifier, is published in the public CVE dictionary. This online directory, accessible free to all, constitutes a valuable source of truth for researchers, security professionals and the general public.
There we find in particular:
- The complete description of the vulnerability : exact nature, technical details, affected components.
- An analysis of the potential impact : severity of the fault, risks incurred, vulnerable populations.
- Workarounds : temporary measures to limit exposure to the flaw while waiting for a fix.
- Information about available patches : links to software updates that close the flaw.
Variations and complexity
The CVE system may seem simple at first glance, but it handles sometimes complex situations.
- Identical vulnerabilities in different products : If the same vulnerability affects several products from different vendors, a single CVE ID is generally assigned, accompanied by specific details for each affected product.
- Hidden and Later Disclosed Vulnerabilities : Some vulnerabilities can be discovered and exploited secretly before being officially reported. A retroactive CVE ID can then be assigned.
- Already patched vulnerabilities : In some cases, a patch may exist before the flaw is officially discovered. A CVE ID can still be assigned for reasons of transparency and communication.
What is the purpose of CVEs?
CVEs are much more than just a system for identifying security vulnerabilities. It is a true pillar of modern cybersecurity, facilitating communication, collaboration and decision-making in the face of omnipresent digital threats.
At the heart of its operation is a centralized public dictionary listing known vulnerabilities, each with a unique identifier, the CVE ID.
Clear and fluid communication
Imagine researchers discovering a critical flaw in software. Without CVE ID, their communication with vendors, CERTs, and end users would be chaotic.
The CVE ID acts as a common language, allowing all stakeholders to speak with one voice and refer to the same specific vulnerability.
Informed prioritization of fixes
Not all vulnerabilities are equal. CVEs are often accompanied by information about the severity of the vulnerability, allowing organizations to prioritize their remediation efforts based on the actual risk involved.
Critical flaws, for example, require immediate attention, while minor flaws can be addressed in a longer time frame.
Targeted research and development
CVEs serve as a compass for security researchers, directing them to areas where research efforts are most urgent.
By analyzing CVE trends, they can identify the most prevalent types of vulnerabilities and develop innovative solutions to thwart them.
Increased trust in digital products
The use and sharing of CVEs by organizations demonstrates their commitment to security and transparency to their customers.
This approach builds trust in digital products and services, establishing a relationship of trust between businesses and their users.
Valuable resources
The CVE system is not limited to assigning identifiers. Each CVE entry is enriched with valuable metadata: detailed description of the vulnerability, discovery date, potential impact, workarounds, available patches, etc.
This information allows users to fully understand the risks involved and take informed steps to protect themselves.
A collaborative community
The success of CVEs relies on global collaboration. Organizations around the world, from independent researchers to government agencies, help identify, analyze and publish vulnerabilities in the CVE database.
What information is present in CVEs?
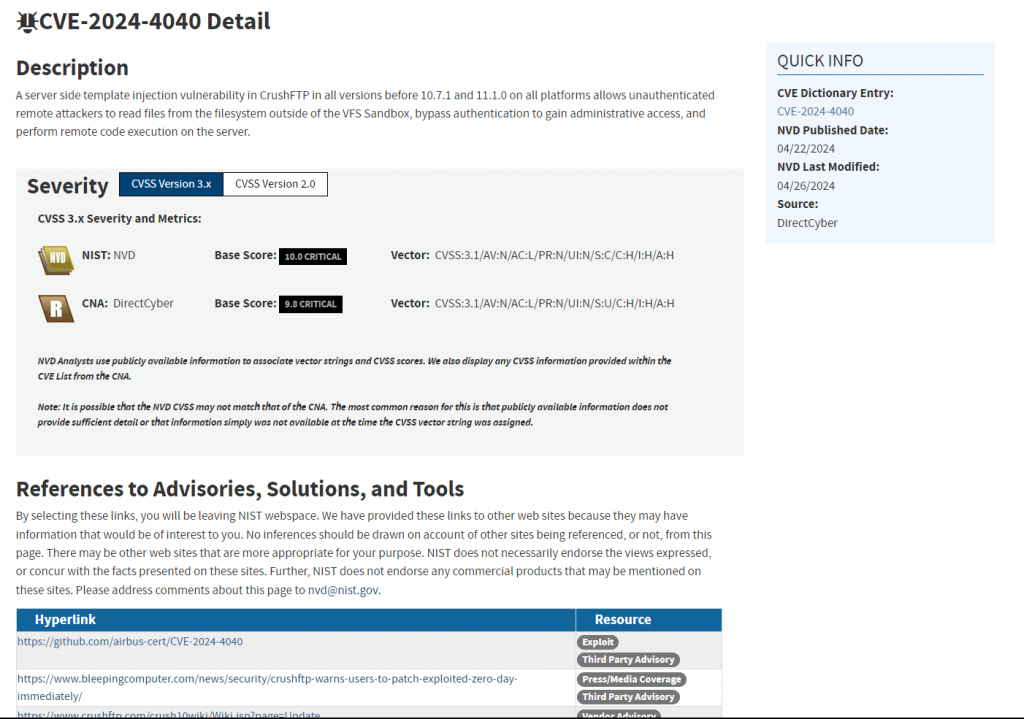
Unique identifiers
Imagine a critical flaw discovered in popular software. Without CVE, chaos would ensue in communication between researchers, suppliers, CERTs and end users. Each party would speak a different language, making coordinating remediation efforts and implementing workarounds nearly impossible.
CVEs overcome this problem by assigning a unique identifier to each flaw. This unique name acts as a common language, allowing all actors to refer to the same vulnerability precisely and unambiguously.
Concise summaries
Each CVE entry provides a succinct summary of the vulnerability, describing its nature in simple, understandable terms. This concise description allows users, whether security experts or ordinary users, to quickly understand the essence of the flaw and its potential implications.
Detailed descriptions
For those who need more in-depth information, CVEs offer detailed descriptions that dive into the heart of the flaws. These technical descriptions, often accompanied by specifications, code examples and precise explanations, allow security experts to analyze the vulnerability in depth, understand how it works and identify ways to exploit it.
Exhaustive list of affected products
Knowing if your system is vulnerable is crucial to taking appropriate protective measures. CVEs specifically list the products or software components affected by each flaw.
This comprehensive list helps users determine whether their systems are exposed and whether they should apply patches or workarounds.
Severity assessment
Not all vulnerabilities are equal. CVEs include a severity rating that indicates the level of potential risk that a vulnerability represents.
This crucial information allows organizations to prioritize their remediation efforts and focus on the most critical vulnerabilities, those that could cause the greatest damage if exploited.
This criticality score is produced by the CVSS evaluation system.
CVSS
CVSS (Common Vulnerability Scoring System), translated into French as “Common Vulnerability Scoring System”, is another essential link in the cybersecurity chain.
Think of it as a rating system that assigns a score to each vulnerability listed in the CVE catalog. Just like exam papers are graded, the CVSS assigns a grade ranging from 0 (low severity) to 10 (critical) to each flaw. This score is calculated according to precise criteria taking into account several factors including:
- Ease of exploitation of the vulnerability : the easier a vulnerability is to exploit, the higher the CVSS score.
- Potential impact on the system : the score takes into account the damage that an attacker could cause by exploiting the flaw (data loss, file corruption, etc.).
- Propagation of the flaw : the CVSS score also takes into consideration the diffusion of the affected software or component. The more widespread it is, the potentially higher the score.
Discovery and update dates
Knowing the date a vulnerability was discovered can be useful for tracing its history, understanding its evolution over time and evaluating the reaction times of the different actors involved in its correction.
Workarounds
Until a final patch is released, workarounds may be available to limit the impact of a vulnerability and protect systems.
CVEs often describe these temporary solutions, providing users with concrete measures to implement to reduce their exposure to risk.
Links to patches
As soon as patches are available to correct a vulnerability, CVEs provide direct links to these patches. This information allows users to quickly update their systems and protect against exploitation of the vulnerability.
References
CVEs, striving to provide complete information, often include links to external resources such as technical articles, security advisories, or online discussions.
These resources allow curious users to deepen their knowledge of a particular vulnerability, its technical implications and the solutions implemented to correct it.
Status to follow the evolution of the situation
The status of a CVE indicates the current state of the vulnerability. This could be a scan in progress, a patch released, new information discovered, or a permanent resolution to the issue.
This information allows users to monitor the situation and take action accordingly.