CVSS score
The Common Vulnerability Scoring System, CVSS, or Common Vulnerability Scoring System, has established itself as an essential standard in the field of computer security, making it possible to assess the severity of CVEs, or vulnerabilities, discovered.
The Common Vulnerability Scoring System, CVSS, or Common Vulnerability Scoring System, has established itself as an essential standard in the field of computer security, making it possible to assess the severity of CVEs, or vulnerabilities, discovered.
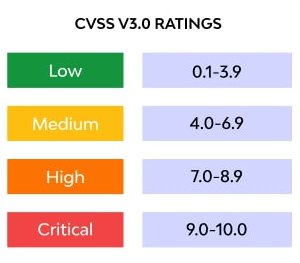
Assigning a score between 0 and 10, with a score of 10 representing the most critical flaw, the CVSS aims to provide an objective and consistent assessment, facilitating informed decision-making for security professionals.
Understanding CVSS Score Calculation
Here is a CVSS 3.1 score:
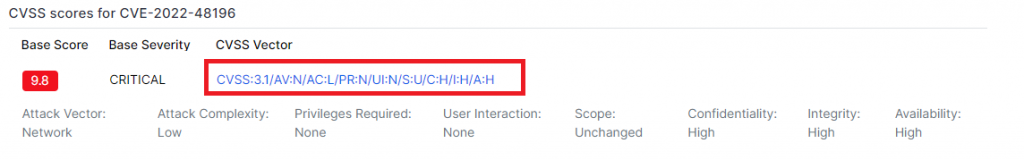
Let’s explain how this score works and what it contains.
The criteria assess the intrinsic impact of a vulnerability, without taking into account its context or environment. They include usability and impact metrics:
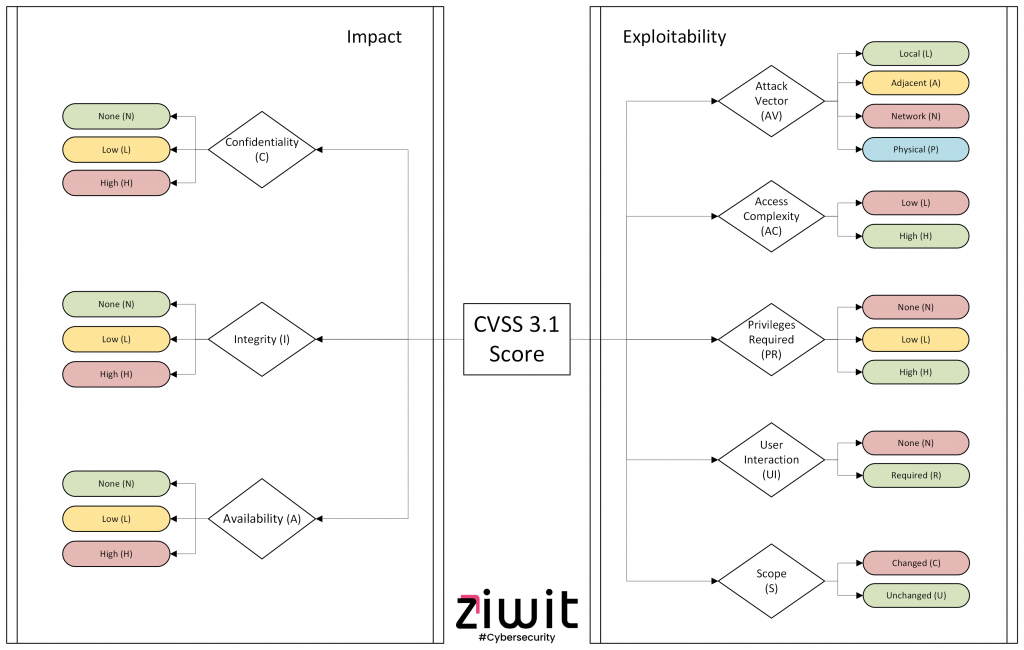
Exploitability
Attack Vector (AV)
The Attack Vector (AV) measures how difficult it is for an attacker to exploit the vulnerability. The possible values are:
- Local (L): The attacker must be present on the vulnerable system.
- Adjacent (A): The attacker must have access to the local network of the vulnerable system.
- Network (N): The attacker can exploit the vulnerability from anywhere on the Internet.
- Physical (P): The attacker must gain physical access to compromise the system.
Access Complexity (AC)
Access Complexity (AC) measures how difficult it is for an attacker to understand and exploit the vulnerability. The possible values are:
- Low (L): Exploitation of the vulnerability is simple and does not require any special skills.
- High (H): Exploitation of the vulnerability is complex and requires specialized skills and knowledge.
Privileges Required (PR)
The Required Privileges (PR) criterion allows you to better understand the level of access necessary to exploit a vulnerability. The possible options for the PR criterion are:
- None (N): Exploitation of the flaw does not require any special access privileges.
- Low (L): Exploitation requires standard user privileges.
- High (H): Exploiting the vulnerability requires elevated privileges, such as administrative privileges.
User Interaction (UI)
The User Interaction (UI) criterion allows you to refine the base score of a vulnerability by taking into account the level of interaction necessary to exploit it. This criterion comes in three options:
- None (N): Exploitation of the flaw requires no interaction from the user.
- Required (R): The user must perform a specific action for the vulnerability to be exploited.
Scope (S)
The Scope (S) criterion makes it possible to refine the assessment of the severity of a vulnerability by taking into account its scope or extent. It is interested in the impact of exploiting the flaw on the compromised system. This criterion can be:
- Changed (C): Exploitation of the flaw allows the attacker to change execution context within the compromised system.
- Unchanged (U): Exploiting the flaw does not allow this.
The Impact
Impact on confidentiality (C)
It measures the potential impact of exploitation on data privacy. The options are:
- None (N): Exploitation has no impact on confidentiality.
- Low (L): The operation may disclose confidential information with low impact.
- High (H): The operation may disclose high-impact confidential information.
Impact on integrity (I)
It measures the potential impact of exploitation on data integrity. The options are:
- None (N): Operation has no impact on integrity.
- Low (L): Exploitation may modify data with low impact.
- High (H): Exploitation can modify high-impact data.
Impact on availability (A)
It measures the potential impact of operation on the availability of systems or services. The options are:
- None (N): Operation has no impact on availability.
- Low (L): Operation may affect the availability of systems or services for a short period of time.
- High (H): Operation may affect the availability of systems or services for an extended period of time.
CVSS 3.1 score Example
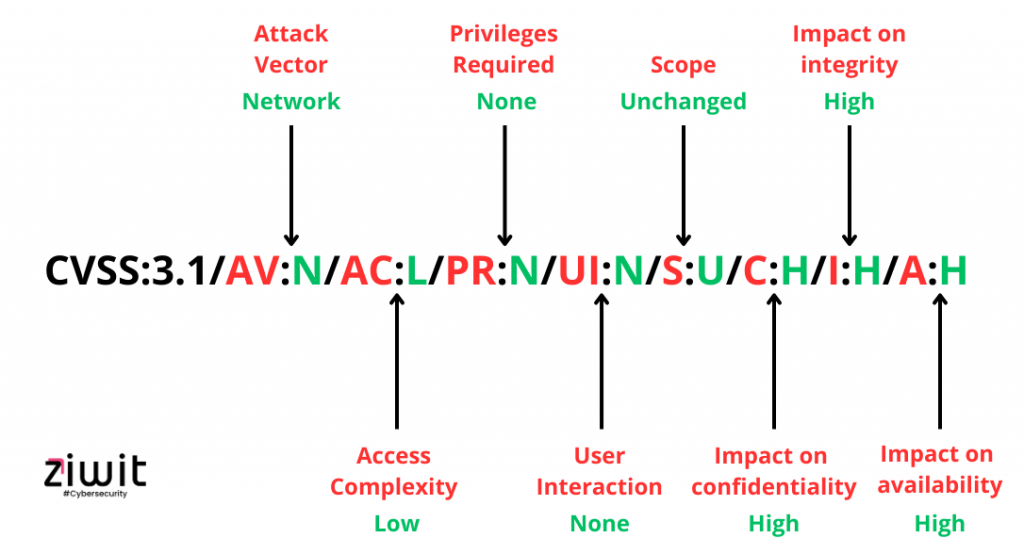
So, let’s go back to our previously cited example:

- Attack vector: Network.
- Complexity of the attack: Low, therefore low complexity of the attack.
- Required privileges: None, no privileges required.
- User interaction: None, no interaction required.
- Scope: Unchanged, or not modified.
- Privacy Impact: High, so confidential data may be revealed.
- Impact on integrity: High, the CVE has a strong impact on the integrity of the system.
- Impact on availability: High, the flaw may impact system availability in the long term.
Here is a summary of the flaw and what it tells us:
The evolution of the CVSS Score
Version 1 (published in 2005)
- Simple structure with two main metrics:
- Severity: measured the overall impact of a vulnerability (low, medium, high).
- Exploitability: indicated how easy it was to exploit a vulnerability (easy, difficult, impossible).
- Final Score: A number from 0 to 10, derived from the combination of Severity and Exploit values.
Limitations of version 1
- Lack of granularity: the metrics offered too limited a choice, not allowing a precise assessment of severity.
- Did not take contextual factors into account: the impact of a vulnerability could vary depending on the environment and specific configurations.
Version 2 (published in 2007)
- Introduction of additional metrics:
- Access: Specifies the privileges necessary to exploit the vulnerability.
- Integrity Impact: measured the extent of potential damage caused by exploitation.
- Availability Impact: Measured the potential impact of an operation on system availability.
- Final score: still 0 to 10 but calculated using a more complex formula taking into account the new metrics.
Version 3 (released in 2013)
- Adoption of a structure with three groups of metrics:
- Base: reflected the intrinsic characteristics of the vulnerability.
- Temporal: took into account the evolution of the vulnerability over time (discovery, exploitation, availability of patches).
- Environmental: took into account contextual factors specific to the environment where vulnerability was present.
- Final score: always 0 to 10, calculated separately for each metric group (CVSS v3.0) or by combining all three groups (CVSS v3.1).
Version 4 (released in 2023)
Major changes for more granular and contextual evaluation:
Basic Group
- Added new metrics and refined existing ones for better vulnerability differentiation.
- Distinction between impact on confidentiality and impact on integrity.
Threat Group
- Replacement of the Temporal group, with a focus on attacker capabilities and the evolution of the threat.
- Introduction of metrics like “action capacity” and “action probability”.
Environmental Group
- Refinement of existing metrics to better account for specific contextual factors.
Final score
- Four possible scores: CVSS-B (Base), CVSS-BT (Base + Threat), CVSS-BE (Base + Environment), CVSS-BTE (Base + Threat + Environment).
- Each score is a floating number between 0 and 100, providing better granular precision.
Who uses the CVSS Score?
The Common Vulnerability Scoring System (CVSS) Score is used by a wide range of actors in the cybersecurity field, including:
Organizations
- IT security teams use CVSS to assess the severity of vulnerabilities discovered in their systems and networks. This allows them to prioritize remediation efforts by focusing on the most critical vulnerabilities first.
- System and network administrators use CVSS to make informed decisions about updating software and applying security patches.
- Risk managers use CVSS to assess the potential impact of vulnerabilities on their organization and to implement appropriate security controls.
Security Solution Providers
- Security software vendors integrate CVSS into their products to help users identify and prioritize vulnerabilities.
- Security consulting companies use CVSS to conduct security assessments and provide recommendations to organizations.
- Security researchers use CVSS to communicate the severity of vulnerabilities they discover.
Government agencies
- Government agencies use CVSS to develop security policies and regulations.
- Standards organizations use CVSS to define security standards.
- Law enforcement uses CVSS to investigate cybercrimes.
Advantages and limitations of the CVSS Score
Advantages of CVSS Score
- Standardization: CVSS offers a common language to assess the severity of vulnerabilities, facilitating communication and collaboration between the different IT security players.
- Objectivity: The calculation of the CVSS score is based on a rigorous and structured methodology, making it possible to obtain an objective and consistent assessment of vulnerabilities.
- Understanding simplified: The CVSS score, in numerical and graduated form, offers a clear and intuitive representation of the severity of a flaw, making it easier to understand by a wide audience.
- Socket of decision Informed: CVSS provides security professionals with valuable information to prioritize remediation actions and efficiently allocate resources.
- Evolution continues: The CVSS is subject to regular maintenance, with updates and enrichments to adapt to new threats and technological developments.
CVSS Score Limitations
- Complexity relative: Considering various factors and metrics can make CVSS score calculation complex, requiring some expertise for accurate interpretation.
- Specific context not exhaustive: The CVSS does not always take into account all contextual aspects specific to an organization or system, which may limit the accuracy of the assessment in some cases.
- Handling Potential: The subjective nature of certain metrics, such as product impact or system priority, can open the door to manipulation of the CVSS score.
- Evolution of the vulnerabilities: The severity of a vulnerability can change over time, particularly with the discovery of new modes of exploitation, which the CVSS score does not always reflect instantly.
- Focus on the vulnerabilities Technical: CVSS focuses primarily on technical vulnerabilities, not taking into account other important security factors, such as configuration errors or human flaws.
CVSS and EPSS score
The Common Vulnerability Scoring System (CVSS) and the Exploit Prediction Scoring System (EPSS) are two distinct, but complementary, assessment systems used in the field of IT security to better understand the risks associated with vulnerabilities.
CVSS score: Focus on technical severity
Remember that the CVSS assigns a score between 0 and 10, reflecting the intrinsic severity of a vulnerability. It is based on technical characteristics of the fault and does not take into account its actual exploitation. In other words, the CVSS indicates the potential severity of a vulnerability if it were to be exploited.
EPSS score: Probability of exploitation
EPSS, on the other hand, focuses on the likelihood that a vulnerability will be exploited in the near future (usually within a 30-day period). This score is based on predictive analytics and threat data observed in today’s cybersecurity landscape.
