CyberNews April 2024
Discover the CyberNews for March 2024. This is the recap of news on Cybersecurity during the month of March2024 in France.
Discover the CyberNews for March 2024. This is the recap of news on Cybersecurity during the month of March2024 in France.
Simone Veil hospital in Cannes victim of Ransomware
The Simone Veil hospital in Cannes was the victim of a ransomware cyberattack on April 16, 2024.
This attack resulted in the encryption of data in the hospital’s computer system, rendering many essential services, such as medical records, the drug prescription system and the radiology system, unavailable.
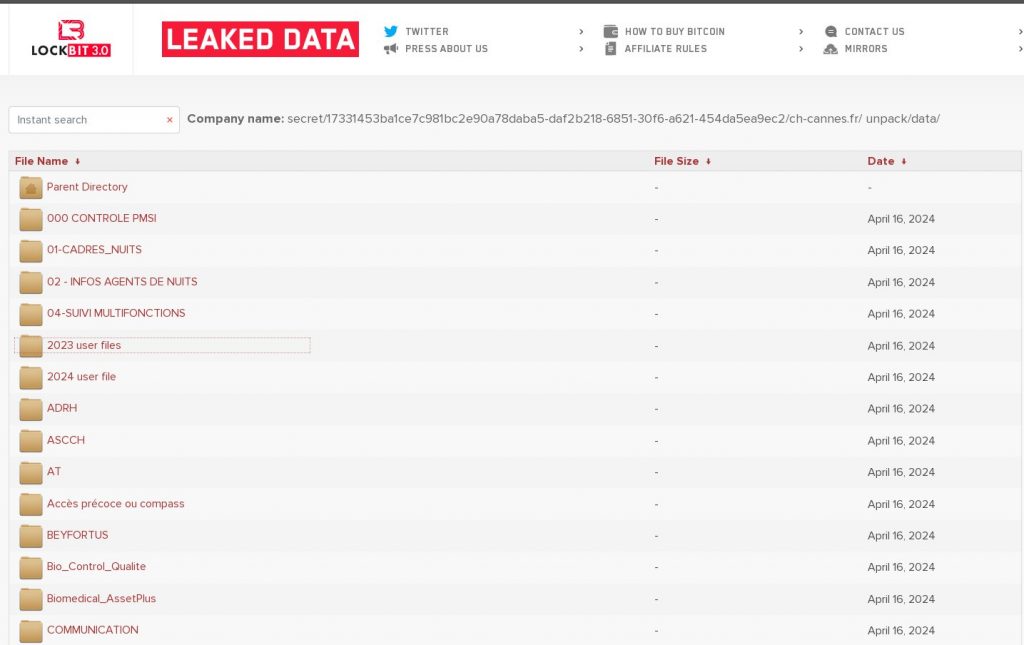
Lockbit hacker group is responsible for this intrusion and data theft, threatening to release the information on May 1 if the ransom demand is not paid.
Consequences of the attack
- Postponement of non-urgent operations and consultations : Doctors did not have access to patients’ medical records, making it impossible for them to perform surgeries or consultations safely.
- Increased workload for staff : Hospital staff had to resort to manual methods to complete many tasks, which significantly slowed down work.
- Stress and anxiety for patients : Uncertainty and delays in care have caused stress and anxiety for patients.
- Sensitive data leak : On the evening of May 1 , 2024, the hacker group LockBit , responsible for the attack, released 61 GB of stolen data, including confidential medical and personal information of patients and employees.
Regarding patients, the leaked data includes:
- Last Names.
- Addresses.
- Dates and places of birth.
- Phone numbers.
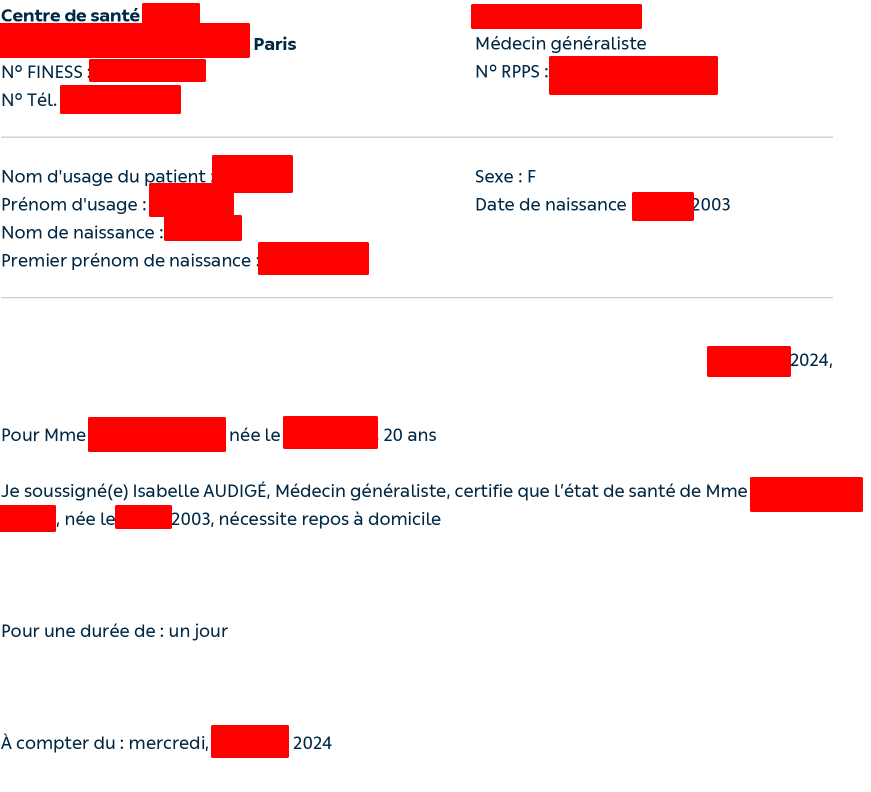
- Health Checks.
- Prescriptions.
- Pediatric assessments.
- Psychological assessments.
Concerning hospital staff, a lot of confidential information is concerned, including:
- Last Names.
- Addresses.
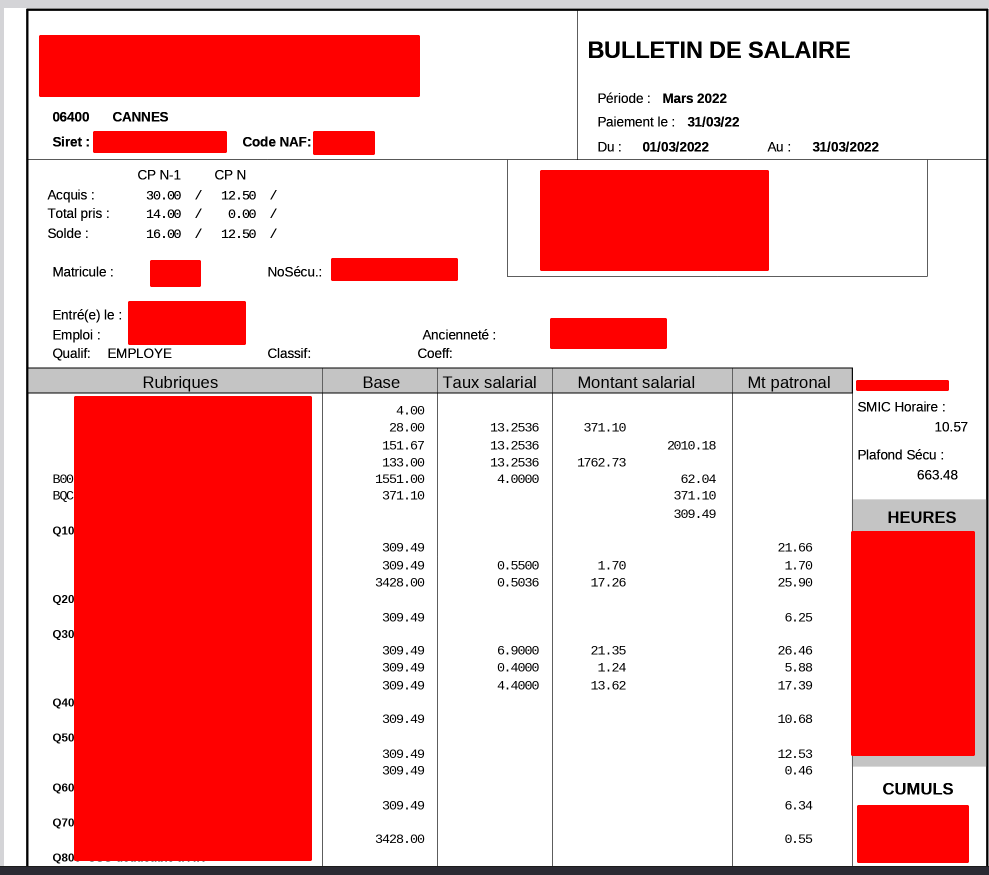
- Payslips.
- ID cards.
- RIB.
Here is what the hospital said regarding the stolen data: “ The management of the hospital center condemns this publication and regrets the damage possibly caused to some of these patients, professionals and partners […] The qualification of the exfiltrated data continues and detailed and personalized feedback will be provided in the coming days to the people and institutions concerned .
We recall that in February 2024, Operation Cronos, led by around ten countries, led to the dismantling of a large part of the Lockbit group . Unfortunately, less than two months later, they returned and resumed their criminal activities.

Cities in France paralyzed after cyberattacks
Albi
The Albi town hall services were victims of a cyber attack on Monday April 22, 2024 at 6 a.m. This attack resulted in the unavailability of several essential services, such as:
- The usual telephone numbers.
- Email addresses .
- Everyday IT services.
This had a significant impact on the functioning of the town hall and on the daily life of the Albi’s residents. Many municipal services could not be provided, and residents encountered difficulties in contacting the town hall.
It took April 30 for the city’s telephone network to be accessible again.
Gravelines
The town of Gravelines was the victim of a cyberattack on Thursday April 25, 2024. This resulted in a significant interruption of municipal services, including:
- Internet access restricted or unavailable for municipal services.
- Closure of the city’s website.
- Malfunctions of bank card payments.
- Disruptions in canteen and daycare services.
The town hall took immediate measures to limit the damage, in particular by disconnecting its servers from the internet.
The attack has not yet been claimed and its motives are unknown. According to authorities, it could be a ransomware attack. The town hall has filed a complaint and an investigation is underway.
The city has gradually restored its services since April 25, but some are still operating in a “very degraded” manner.

The SREN bill definitively adopted
On April 10, 2024, after an intense legislative process, the bill aimed at securing and regulating the digital space (SREN) was definitively adopted by the French Parliament, with 134 votes for and 75 against.
This ambitious law, supported by the French government, aims to adapt French law to European Digital Services Act (DSA) and Digital Markets regulations. Act (DMA), while introducing specific measures to strengthen the security and regulation of the French digital space.
This major bill brings together several measures including:
Fight against online scams
The bill puts in place several measures to better identify and block fraudulent sites, such as the creation of an anti-scam filter and the obligation for platforms to remove illegal websites more quickly.
Protection of minors
The text aims to better protect minors against dangerous content online, particularly pornography. It provides in particular for the rapid blocking of pornographic sites accessible to minors and reinforced parental control tools.
Fight against cyberbullying
The bill toughens sanctions against cyberstalking and provides for the possibility of banning cyberstalkers from social networks.

Platform closures and arrests of cybercriminals
SelkiScan
At the end of March 2024, French authorities shut down the activities of SelkiScan, a website that allowed the automated generation of false French identity documents.
This operation, carried out jointly by the national police, the gendarmerie and the intelligence services, made it possible to arrest two individuals suspected of being behind this site and to seize critical IT infrastructures.
SelkiScan was accessible to everyone, with no authentication required. It allowed anyone to create fake French identity documents in a few clicks, for just a few euros. This site posed a significant danger to public safety because it facilitated identity theft, document fraud and other illegal activities.
The two individuals arrested as part of this operation were indicted for criminal conspiracy, counterfeiting and money laundering. They face heavy sentences if found guilty.
Fast Scam
In mid-April 2024, French authorities dealt a new blow to the Fast Scama criminal network by closing its Telegram account . This account, used by the network to communicate with its customers and distribute its advertisements, constituted a centerpiece of its illegal activities.
As a reminder, the Fast Scama network was dismantled in February 2024. This network specializing in the creation and sale of false identity documents, diplomas and banking documents had been rampant for several years and would have generated millions of euros in profits. The operation led to the arrest of two suspects and the seizure of critical IT infrastructure.
The closure of Fast Scama ‘s Telegram account adds to the measures taken in February 2024 and constitutes an additional blow to the network.
CosaNostra
The 03 april 2024, a cyber police operation resulted in the closure of the CosaNostra store, a notorious hub of illegal activity on the dark web. This platform, infamous for its wide range of illicit content, posed a significant danger to the security of individuals and societies.
CosaNostra functioned as a virtual black market, offering a range of illegal products for sale:
- Drugs,
- Fire arms,
- Malware,
- Hacked data,
- etc.
This platform constituted a privileged meeting point for cybercriminals, allowing them to carry out their dubious transactions with relative impunity.
The closure of CosaNostra is part of a determined fight against cybercrime. The authorities, aware of the dangers posed by these platforms, have taken firm measures to neutralize them and protect citizens.

The arrest of the administrator of CosaNostra , identified under the pseudonym ” CosaNostra “, and the seizure of a second platform managed by this individual constitute hard blows to organized cybercrime.
This closure is a close collaboration between the anti-cybercrime section (J3) of JUNALCO, the cyber customs service of DNRED and the C3N of the National Cyber Unit of the National Gendarmerie.
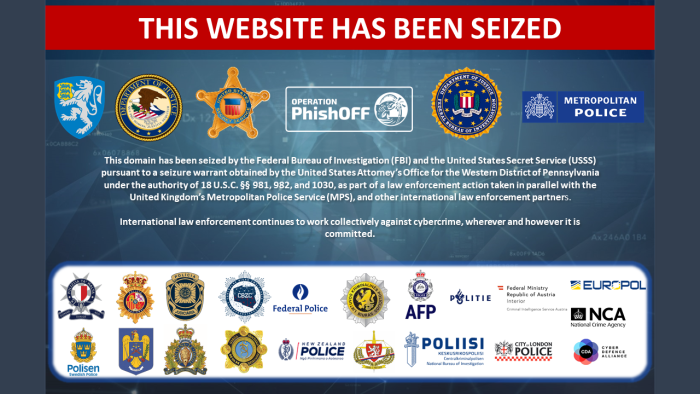
LabHost
Between April 14 and 17, 2024, a coordinated international operation significantly disrupted one of the world’s largest phishing-as-a-service (PaaS) platforms, known as LabHost .
This platform, infamous for its wide range of services enabling the creation and distribution of sophisticated phishing attempts, posed a significant danger to the security of individuals and businesses.
LabHost offered its customers a full range of tools and services to carry out targeted and effective phishing attacks. The platform provided customizable templates, secure hosting for malicious websites, email and SMS phishing techniques, and analytics tools to evaluate campaign success.
LabHost has been responsible for millions of phishing attacks causing considerable financial and moral damage to its victims. Personal and financial information stolen through these attacks has been used for fraudulent purposes, such as identity theft, hacking of bank accounts and spreading malware.
LabHost takedown operation was carried out by a consortium of police and cybercrime agencies from several countries, under the coordination of Europol. The authorities seized the platform’s servers, closed its domain names and arrested its administrator.

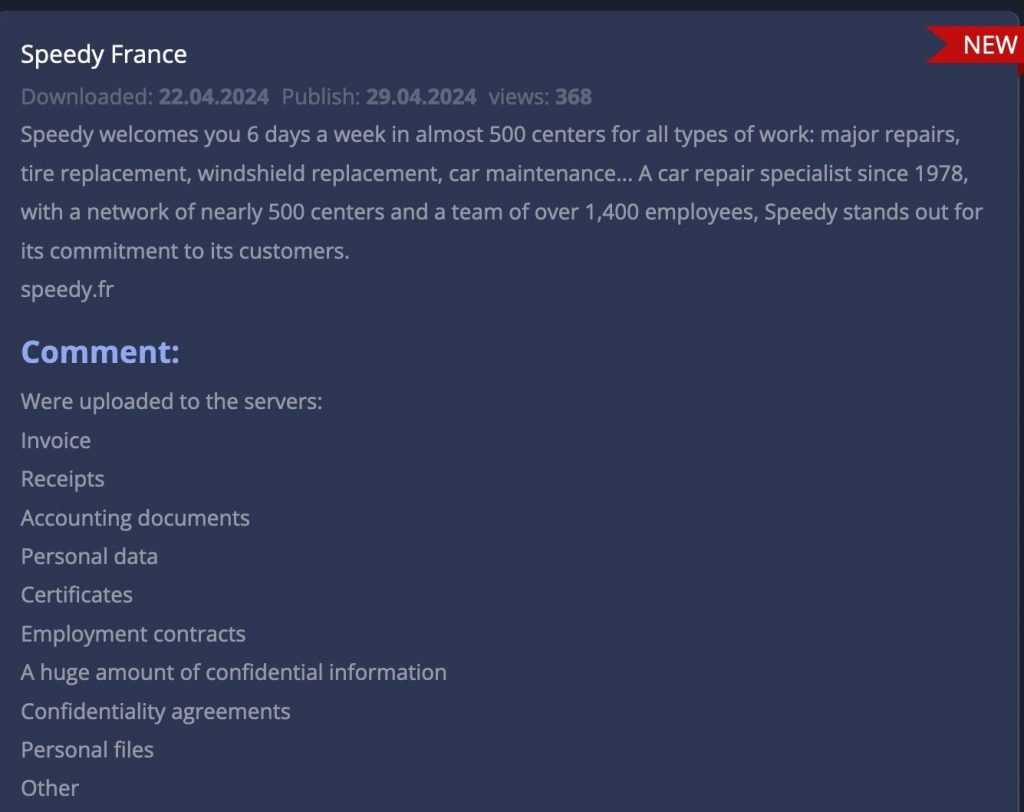
Speedy France victim of a cyber attack
Since Friday April 19, 2024, Speedy, a French company specializing in vehicle repair and maintenance, has suffered a computer attack which impacts its online services and customer data. The company confirmed this in a statement published on its website.
Direct consequence of this cyberattack: online appointment booking is temporarily unavailable. Customers wishing to schedule an intervention on their vehicle will therefore have to contact Speedy by telephone or go directly to a center.
In a press release addressed to affected customers, Speedy specifies: “ You are registered in our databases and we inform you that a cybersecurity incident has been identified at Speedy France […] It is possible that some of your personal data has been compromised .
The cybercriminals behind this attack and data theft are the 8Base group. Here is their message:
Speedy France’s reaction
In addition to having deactivated online appointment booking, Speedy reacted quickly by:
- Mobilizing experts to take protective measures: “ We immediately mobilized our teams of experts and our partners specializing in the management of this type of incident, in order to take the necessary protective measures, then carry out the appropriate investigations ” .
- Notifying the CNIL (National Commission for Information Technology and Liberties).

Sport 2000: Data from 4.5 Million leaks
On April 18, 2024, Sport 2000, a French brand selling sporting goods, confirmed that it had been the victim of a computer intrusion having compromised the personal data of more than 4 million customers.
According to the Sport 2000 brand, the hacked data includes, among others:
- Last Names
- Postal addresses
- Phone numbers
- Email addresses
- Existence of children in the family home
- Loyalty card number and related information
- Store identifier attached to the account
- Amount of purchases over the last few months
Sport 2000 reacted by taking several decisions:
- Carrying out investigations by their experts.
- Implementation of corrective actions and improvement of their protection.
- Filing a complaint with the courts.
- Notification to the CNIL for personal data violation.
- Notify customers directly.

Le Slip Français victim of a data leak
On April 15, 2024, Le Slip Français, a French underwear brand, announced that it had been the victim of a cyberattack resulting in a leak of customer data.
A sample of stolen data was published online on April 13 on a specialized forum, citing a base of more than 1.5 million affected customers.
Compromised information includes:
- Last Names
- Postal addresses
- Email addresses
- Phone numbers
- Order numbers
Le Slip Français said it immediately put in place measures to secure its systems and limit the impact of the incident. The company also informed the National Commission for Information Technology and Liberties (CNIL) and notified its customers by email .
This is a hard blow for Slip Français which is currently experiencing a drastic drop in its number of orders, leading to a drop in prices and a change in its communication.

A huge Data Breach for PandaBuy
PandaBuy is a Chinese shopping platform that helps international customers purchase products from Chinese resellers.
In early April 2024, hackers successfully infiltrated the platform and exposed the personal information of more than 1.3 million users.
The exact scope of the leak is not entirely clear at this time, but the compromised data could include sensitive items such as:
- PandaBuy login credentials .
- Full names.
- Phone numbers.
- Personal and professional email addresses .
- Postal addresses for billing and delivery.
- Login IP addresses used to access the account.
- Data relating to orders placed, potentially including details of products purchased.
Here is the message on Discord from a person at the head of PandaBuy.

Dropbox Sign , victim of an intrusion
Dropbox Sign, an electronic signature service integrated with Dropbox, experienced an intrusion on April 24, 2024.
Hackers managed to illegally access Dropbox Sign systems, compromising sensitive information. However, the contents of Dropbox storage and Dropbox Sign documents were not affected.
Here is the data compromised in the hack attack:
Basic credentials
This includes the usernames and email addresses of all Dropbox Sign users, including those who don’t use Dropbox itself. Phone numbers were also compromised for some users.
Login information
Hackers were able to access users’ hashed passwords. Fortunately, hashed passwords are not stored in a readable form and cannot be easily cracked by hackers. However, to be on the safe side, it is essential to change your Dropbox Sign password immediately.
Multi-factor authentication data
Information about multi-factor authentication (MFA) settings was also compromised. Multi-factor authentication adds an extra layer of security by requiring an additional verification code when logging in. Even if hackers have obtained information about the MFA setup, it is likely that they need the additional verification code to hack your account.
Confidential access tokens
Hackers also got their hands on API keys and OAuth tokens . These tokens are used to connect Dropbox Sign to other applications. If you’ve connected Dropbox Sign to other apps and services, consider changing your login credentials for those apps as a precaution.

The PSG ticket office, victim of an intrusion
On April 3, 2024, Paris Saint-Germain was the victim of a cyberattack targeting its online ticketing system. This attack compromised the personal data of some club supporters.
Here are the facts:
- Unusual access attempts on the ticketing platform were detected by the PSG IT department on April 3.
- A security breach was identified and corrected in less than 24 hours.
- The personal data of some supporters, such as names, email addresses , postal addresses, telephone numbers, dates of birth and account information, may have been accessed by the hackers.
- Bank card numbers are not affected by the flaw, but the last three digits of IBANs have been exposed.
- PSG informed the National Commission for Information Technology and Liberties (CNIL) of this data breach.
- The club also contacted supporters affected by the breach individually.

Web giants & CRITICAL security breaches
Palo Alto Networks
A critical zero-day flaw, referenced CVE-2024-3400 and having a criticality score of 10, recently affected Palo Alto Networks’ next generation firewalls (NGFW). This vulnerability, which affects the PAN-OS operating system, represents a major risk for organizations that use these firewalls.
The flaw resides in the GlobalProtect functionality of PAN-OS and allows an unauthenticated attacker to execute arbitrary code with root privileges on the firewall if successfully exploited. In other words, a hacker could take full control of the firewall, compromising the security of the protected network.
Palo Alto Networks has released patches to address this flaw. It is crucial to apply these patches as soon as possible to protect your firewalls.
Cisco & ArcaneDoor
ArcaneDoor is a targeted, long-running hacking campaign that compromised Cisco equipment at multiple organizations around the world.
The cybercriminals behind this campaign have demonstrated a high level of sophistication and persistence in their attacks, exploiting zero-day vulnerabilities and advanced techniques to infiltrate networks and steal sensitive data.
ArcaneDoor attackers used a combination of attack vectors and techniques to carry out their intrusions, including:
- Exploitation of zero-day vulnerabilities : Attackers took advantage of unpublished flaws in Cisco Adaptive Security Appliance (ASA) firewalls to gain initial access to targeted networks.
- Backdoor attacks : Once inside networks, attackers installed persistent backdoors allowing them to maintain discreet access and bypass security measures.
- Lateral Movement : Attackers used lateral movement techniques to move stealthily through compromised networks, identifying and accessing sensitive systems and data.
- Data theft : Attackers exfiltrated sensitive data, such as employee credentials and company secrets.
ArcaneDoor ‘s targets were primarily government and private sector organizations in critical industries such as defense, aerospace, and manufacturing.
Critical vulnerabilities CVE-2024-20353 and CVE-2024-20359 affect the management and VPN web servers of Cisco Adaptive Security Appliance (ASA) and Cisco Firepower appliances Threat Defense (FTD). These flaws allow an unauthenticated attacker to cause an unexpected reboot of the device, leading to a denial of service ( DoS ).
Explanation of vulnerabilities:
- CVE-2024-20353 : This flaw lies in the processing of HTTP headers by the web servers of Cisco ASA and FTD appliances . An attacker can send a specially crafted HTTP request to trigger infinite processing, resulting in a device reboot.
- CVE-2024-20359 : This flaw is also linked to the processing of HTTP headers by the web servers of Cisco ASA and FTD appliances . An attacker can send an HTTP request containing a malicious header field, which causes a buffer overflow and a device reboot.
Magento / Adobe Commerce
A critical security flaw, referenced CVE-2024-20720, recently affected the Magento e-commerce platforms, now known as Adobe Commerce.
In April 2024, malicious actors begin actively exploiting the flaw to steal payment data from Magento e-commerce websites.
This vulnerability, classified as critical by CVSS with a score of 9.1, allows arbitrary code execution (RCE) by an authenticated attacker with administrative privileges.
This flaw results from improper neutralization of special elements used in operating system commands, which allows an attacker to inject malicious code and execute it on the Magento server.
An attacker who successfully exploited this flaw could take full control of the compromised server, accessing sensitive data, installing malware or disrupting the operation of the e-commerce platform.
Windows
BatBadBut ” security flaw , referenced CVE-2024-24576 and criticality 10, affects Windows operating systems and represents a serious threat to users.
Classified as critical by Microsoft, this vulnerability allows an attacker to execute arbitrary code with elevated system privileges on a vulnerable Windows system if successfully exploited.
The flaw lies in the “Win32k.sys” component, a system driver essential to the operation of the Windows graphics subsystem. An attacker could exploit this vulnerability by sending a malicious message to a process running on the target system. If the message is processed successfully, the attacker could take full control of the system.
Microsoft has classified this flaw as “critical”, indicating an extremely high risk of exploitation. The vulnerability affects all supported versions of Windows, including Windows 11, Windows 10, and Windows 8.1.
Google Chrome
A critical security flaw, referenced CVE-2024-4058, affects the Google Chrome web browser. This remote code execution (RCE) flaw allows a remote attacker to execute arbitrary code on a vulnerable device if successfully exploited.
The flaw lies in Chrome’s JavaScript rendering engine, V8. An attacker could exploit this vulnerability by creating a malicious web page and tricking a user into visiting it. If the user visits the web page, the attacker could execute arbitrary code on their device, allowing them to take control of the device or steal sensitive data.
Google has classified this flaw as “critical”, indicating a high exploitation risk. The vulnerability affects all versions of Google Chrome, including desktop, mobile, and tablet versions.
Google has released a security update to address this flaw in Chrome version 108.0.5409.122. It is crucial to install this update as soon as possible to protect your device from exploit attacks.