Health Structures & Cyberattacks in France in 2022
Health Structures are often subject to Cyberattacks in France. These healthcare establishments must protect themselves effectively against hackers.
Every month, we hear in the news an orchestrated attack against a health establishment, whether it is a private establishment, such as a radiology center, or a public one such as university hospitals.
At the end of June 2023, the Rennes University Hospital was the victim of a cyberattack impacting its activity and leading to a data leak. The director of digital systems at Rennes University Hospital recalls that the hospital center has 1,000 servers and 7,000 workstations. The hospital was prepared for such an attack, so an hour after the attack, the crisis unit was triggered, leading to a suspension of online appointment bookings, teleconsultations but also bank card payments.
Incidents similar to that at Rennes University Hospital happen frequently. Each year, the Digital Health Agency, or ANS, in collaboration with the Ministry of Health and Prevention as well as the CERT Santé, publishes a report on security incidents of information systems for the health and medico-social.

Health structures – a key target
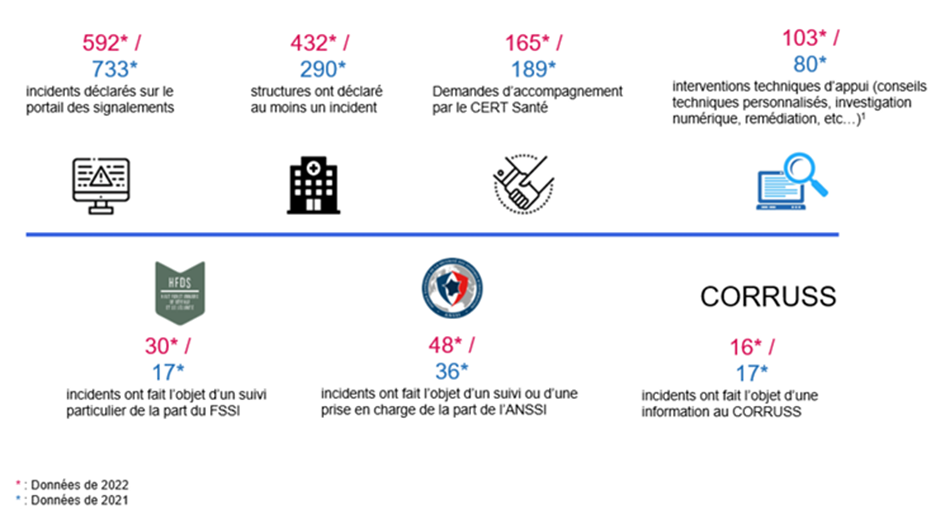
Thus, in the report communicated by the ANS, we learn both that there was an increase of 33% in the number of structures having declared at least one incident, but also a decrease of 19% in the number of incidents declared. However, more incidents were handled by ANSSI, incidents being therefore serious and important.
Healthcare establishments represent a real opportunity for hackers. Full of confidential and personal information and lacking cutting-edge cybersecurity, they have today become real targets of choice.
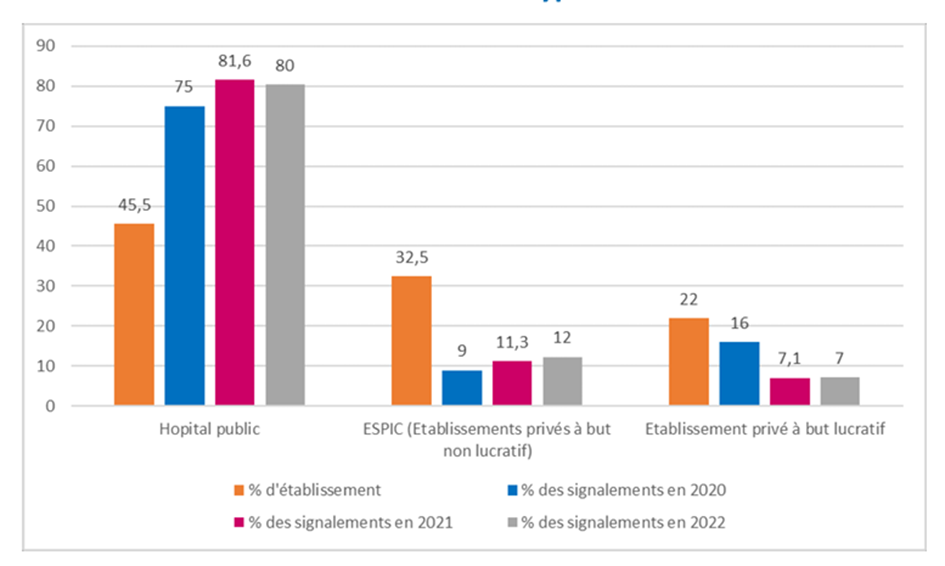
And a large proportion of incidents in these health establishments affect the public sector. In 2022, 80% of these establishments having reported an incident are public hospitals.
Types of incidents
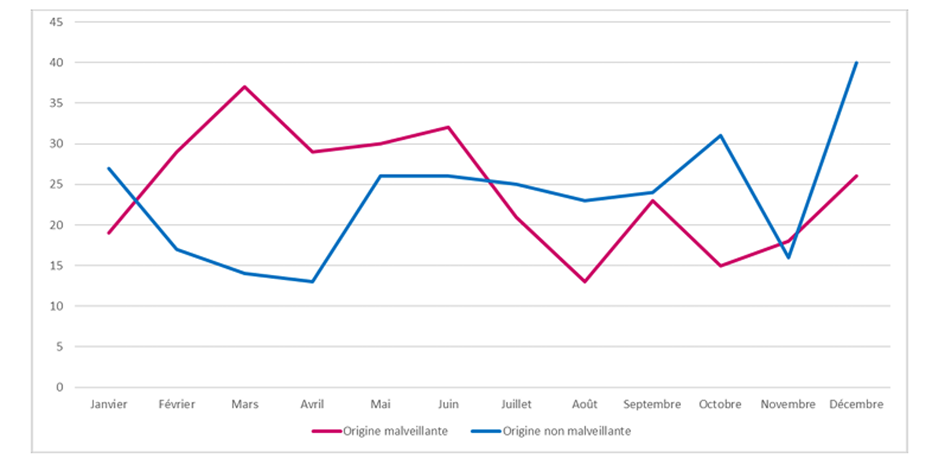
Among the incidents declared in 2022, half are of malicious origin, and the other half are non-malicious.
Malicious incidents
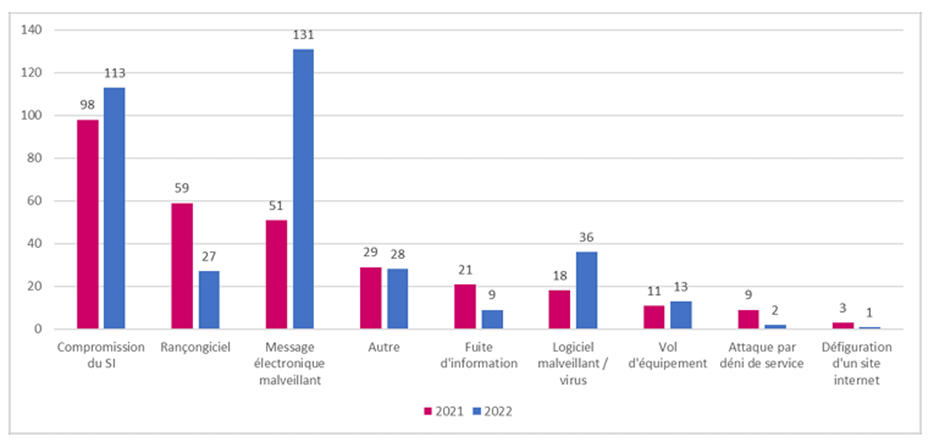
Of the 592 incidents reported by health structures in 2022, 50% of these were of malicious origin. The ANS counted and classified the types of malicious acts.
Malicious email message
Thus, as we can see, with 131 incidents, the year 2022 was strongly marked by the use of malicious electronic messages, which consists of the theft of identifiers (logins and passwords) of electronic messaging accounts.
Compromise of the IS
The compromise of the Information System is also strongly noticed with 113 incidents in 2022. Here, it concerns the compromise of maintenance accounts for infrastructure and application solutions.
For these two techniques, the hackers were able to recover the identifiers using several methods:
- Phishing, or phishing in English, consisting of obtaining confidential information via email. As this type of technique is increasingly used, it is necessary to train and raise awareness among healthcare personnel through personalized phishing campaigns.
- Exploiting flaws and vulnerabilities on equipment. Using a vulnerability scanner allows you to act before security vulnerabilities are exploited.
- The Brute Force technique, consisting of testing a large number of passwords to access the victim’s account.
Malware/Virus
The 3rd malicious act observed during the year 2022, with 36 incidents, is the use of malware and/or viruses. These are therefore malicious codes used to recover data, bring down or disrupt systems and machines, deploy malicious bots or carry out cryptojacking.
” Other “
The “Other” category concerns unsuccessful attempts at phone or email scams, or intrusion attempts.
Ransomware
With a clear drop between 2021 and 2022, a decrease of 54% between the two years, we have ransomware, or ransomware. Ransomware attacks are often the most devastating, causing serious problems for some organizations.
Ransomware consists of data recovery and encryption. Then the criminals will threaten to disclose the recovered information if the health establishments do not pay a certain amount.
The government has recommended never paying the requested ransom, for several reasons:
- Paying the ransom does not guarantee decryption of the stolen data.
- Payment of the ransom does not guarantee the resale of data on the Dark Web.
- This encourages cybercriminals to continue their activities.
- This will not protect the health structure from being targeted by hackers again.
- Obtaining a decryption key does not always make it possible to reconstruct all of the encrypted files; in fact, globally, health establishments having paid a ransom have only been able to recover 65% of their data.
- Payment helps subsidize criminal organizations
Information leak
The information leaks concern login credentials and personal health data. It is strongly recommended to use Data Leak software to constantly and continuously monitor whether information has been leaked or disclosed.
Incidents of malicious origin represent a significant portion of reported incidents, however not all are of the same magnitude and do not lead to the same consequences. Thus, ransomware is often the most notable and the most publicized because confidential and personal data is stolen and is threatened with disclosure or resale.
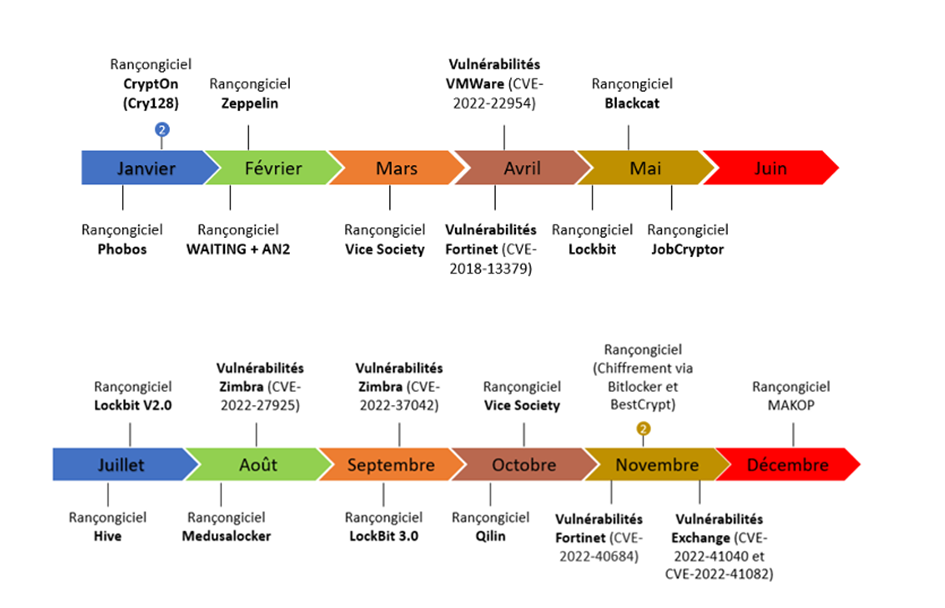
Incidents of non-malicious origin
If 50% of incidents are malicious acts, 50% are therefore non-malicious. Here are the incidents reported to the ANS.
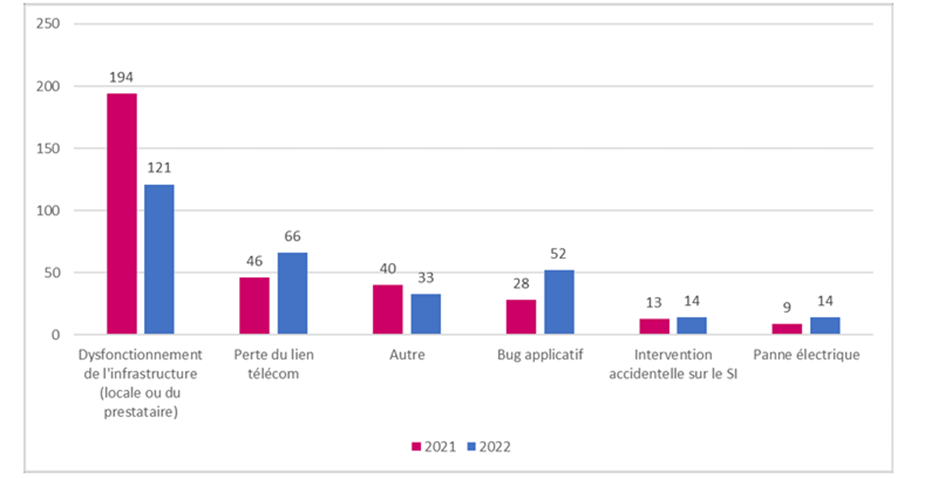
- In these incidents of non-malicious origin, we find, in the majority, malfunctions of the infrastructure. This concerns, for example, uncontrolled changes made to the Information System internally or incidents originating from hosts or service providers. These malfunctions cause more or less prolonged interruptions of service or hosted applications.
- Next comes the loss of the telecom link. This type of incident has a strong impact on emergency or SAMU services. Operators resolve these issues as a priority.
- Application bugs are linked to external or internal applications having problems in their functioning. In most cases, publishers react quickly and offer an update that resolves the bug(s).
- In the “other” category, we find the majority of flaws and vulnerabilities not exploited and subsequently corrected.
The consequences of these incidents
Whether these are acts of malicious or non-malicious origin, the consequences for health structures can be serious and can impact both the structure, the services and also the patients.
The impact on activities
One of the major impacts when a health structure suffers a cyberattack concerns the proper functioning of its activities.
When this concerns a fault at the telecommunications level, the links with the SAMU are no longer operational, causing problems in the care of people and patients.
Concerning other types of incidents, according to the ANS report, 39% of structures affected by incidents, whether malicious or not, were forced to implement operation in degraded mode.
This degraded mode operation forces healthcare establishments to change their methods and processes. This mode can, for example, force the use of paper to manage patients, implement workaround solutions to take into account malfunctions in prescription software or even prohibit payment by bank card.
In cases where the incident does not involve ransomware, the use of such a mode of operation is implemented, on average, for an entire day.
In the serious case where it is ransomware, the degraded mode lasts for more than a month, with the need, during the first week, to organize patient care in neighboring establishments, in this case concerns 19% of establishments, and for good reason, they were forced to interrupt patient care.
The financial impact
Operating in degraded mode obviously entails significant financial costs. During this type of process, operational changes increase costs and treatment time for each patient. Thus, the loss of time, the slowdown in task execution and the mobilization of staff lead, de facto, to greater financial expenses.
In the case of ransomware, even if in France the ministry recommends not paying the ransom, you should know that healthcare establishments are the most likely to pay the ransom to recover encrypted data. Thus, globally, 61% of organizations pay the ransom compared to an average of 46% for other organizations.
The average ransom in the medical sector is €189,000, which is significantly less than the global average of €779,000.
Even if the average ransom in the healthcare sector is not as high as the global average, the fact remains that this sum represents a significant cost for hospitals.
The impact on data
In the ANS report, it is indicated that 63% of health structures having suffered an incident were impacted in terms of their data, whether personal, technical or relating to the proper functioning of the structure.
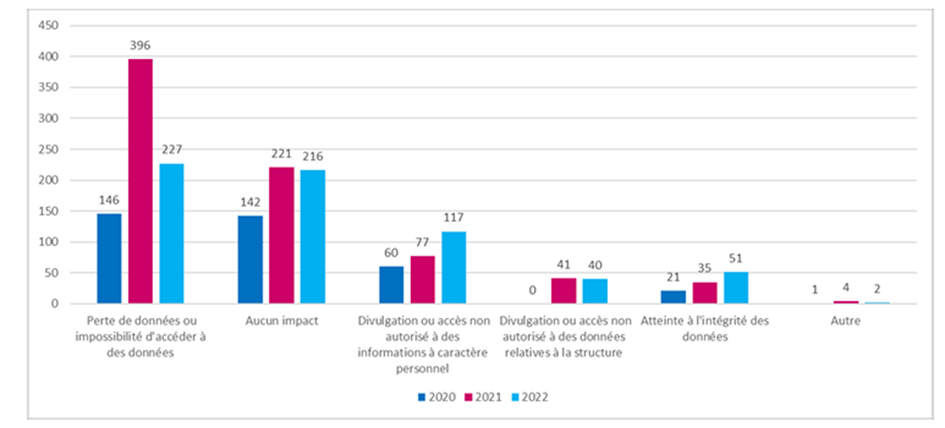
More than 50% of the information impacted by a leak, loss or inability to access data concerns personal and confidential patient information such as patient files or analysis results.
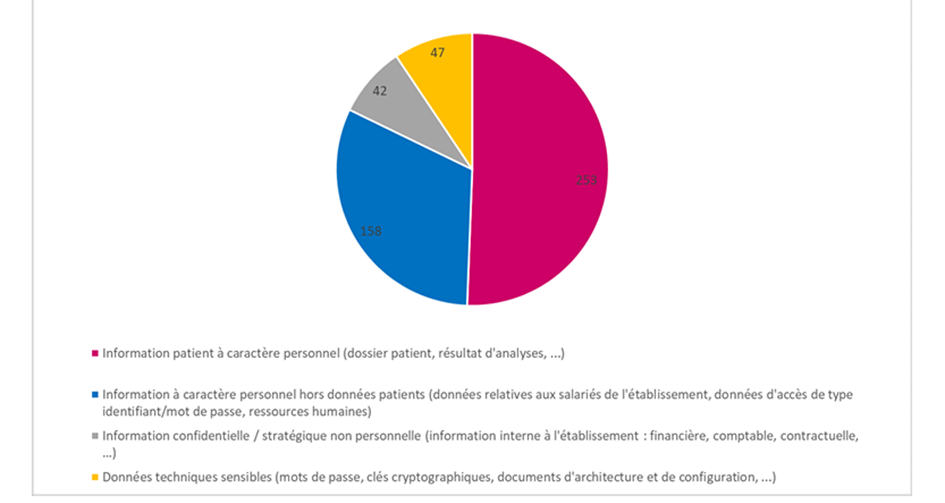
32% of data impacts concern unauthorized disclosure or access to information, whether personal data or data concerning the structure itself.
The disclosure of data on the health facility can lead to serious problems in the security of the latter.
Concerning personal data about patients, they do not want to see their information leaked. A health establishment with leaked data creates a serious problem of patient trust in the establishment.
When data has leaked, it is essential to announce it to the CNIL within 72 hours; if this is not done, the structures may be fined.
Due to their lack of IT protection and security coupled with the fact that they process a lot of confidential and personal data, healthcare structures have become an important target for hackers and hackers.
Hospitals and other health establishments must now have a set of protocols in the event of a cyberattack, such as operating in degraded mode.
In addition, the state has allocated more financial and human resources to provide better IT security for hospitals and public health establishments. Staff are starting to train and become aware of IT risks, such as phishing. More and more hospital information systems have vulnerability scanners and other cybersecurity software allowing them to detect flaws and vulnerabilities before they are exploited by malicious people. Implementing Cyber Threat Intelligence software, or data leak detection, also allows healthcare establishments to monitor whether their information has been leaked.
Finally, it is strongly recommended, at least once a year, to carry out a Pentest, or intrusion test, by cybersecurity experts to check the entire information system of the healthcare establishment.
