CyberNews March 2024
Discover the CyberNews for March 2024. This is the recap of news on Cybersecurity during the month of March2024.
Discover the CyberNews for March 2024. This is the recap of news on Cybersecurity during the month of March2024.
A cyberattack against France Travail leads to the leak of 43 million data
On March 8, 2024, France Travail, formerly Pôle Emploi, notified the CNIL, National Commission for Information Technology and Liberties, the personal data regulator, of a leak of personal data of no less than 43 million accounts.
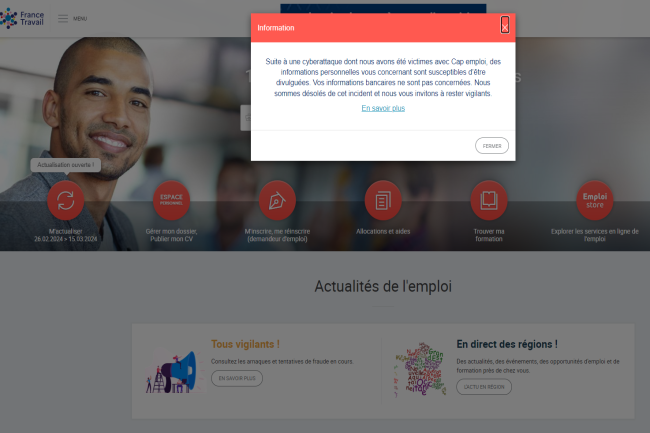
The data concerned are:
- Name,
- First name,
- Date of birth,
- Social security number,
- France Travail identifier,
- Email addresses,
- Telephone numbers,
- Postal addresses.
People arrested
Following this cyberattack and data theft, a judicial investigation was immediately opened.
“Three people were arrested on Sunday in the case of leaks of personal data to the detriment of France Travail,” the Paris prosecutor’s office announced in a press release.

On Sunday March 17, 3 people in their twenties were arrested at their home.
A search was carried out on their computer equipment, confirming fraudulent activity using phishing.
The public prosecutor announced: “Between February 6 and March 5, accounts of Cap Emploi agents, authorized to access the resources present on the France Travail information system, (were) used to proceed downloading data from the job seekers database estimated at 43 million pieces of personal data“.

A wave of DDOS attacks hit France
The course of events
At the beginning of March, a wave of cyberattacks of unprecedented scale hit French state services, as well as sites considered to be part of the French state.
No fewer than 2,500 sites were affected, including 800 administrative sites affected according to the French government.
Among the latter, we find:
- Ministries: Ministry of Labor, Ministry of the Interior, Ministry of Finance, Ministry of National Education, etc.
- Important websites: impots.gouv.fr, service-public.fr, diploweb.gouv.fr, etc.
- Local authorities: Town halls, regions, departments, etc.
Despite the scale of the attack, government IT security teams responded quickly to limit the damage and restore services. “Since yesterday evening, several state services have been the subject of computer attacks whose technical methods are classic, but the intensity is unprecedented,” indicated the Prime Minister’s press service the day after the attack. “At this point, the impact of these attacks has been reduced for most services and access to state sites restored.”
The impact of the attack varied depending on the websites and services affected. No data was recovered or stolen. Some websites were made inaccessible for several hours, others experienced significant slowdowns.
Who carried out this attack?
Different groups of hackers have claimed responsibility for these attacks on Telegram messaging.
The DDoS attacks targeting France were, in the majority, orchestrated by Anonymous Soudan with the support of InfraShutDown, a DDoS service provider.
The pro-Russian hacker group Anonymous Sudan claimed responsibility for the attack, saying it was acting in retaliation for economic sanctions taken by France against Russia following the invasion of Ukraine.

Anonymous Sudan is a group of pro-Russian hacktivists that emerged on the international scene in 2019. They are known for carrying out denial-of-service (DDoS) attacks against Western governments and companies.

Threats of attack broadcast via ENT
Digital Workspaces (ENT) are online platforms that bring together different digital tools and services intended for the educational community. Teachers, parents and students have access to ENT.
On March 21, 2024, the Paris park opened an investigation following a computer hacking of the ENTs of more than 130 educational establishments in France.
Like the cyberattack against France Travail, the method used is phishing.
The perpetrators of this attack therefore sent emails or messages with the aim of stealing information allowing them to connect to the victims’ ENTs.
In addition, ENTs do not have a double authentication system to secure and warn of any malicious connection attempt.
Threats of attack
Several messages then appeared in the ENTs aimed at parents, students and teachers such as “I’m fed up with this shitty life, with you teachers and this high school. So I decided thanks to my brothers who are determined to Islamic State, to blow everything up.“
Fortunately, no threats were carried out.
Several people, young people, were arrested following messages announcing an attack or threatening a school establishment.
A 21-year-old man and bomb threats
The Angoulême public prosecutor’s office has remanded a 21-year-old man in custody. He admitted to sending several bomb threats to different schools.
According to his lawyer, this young man who was out of school and reclusive never wanted to take action.
17-year-old minor sends beheading videos
In Malakoff, south of Paris, a 17-year-old minor admitted to having hacked ENTs and sent threats of attack in the name of radical Islam. These threats were accompanied by beheading videos.
The young man was also placed in pre-trial detention and was presented to the investigating judge.
He stated that he had obtained the ENT accesses on the Internet, and had sent the threats and videos in order to “have fun”.
A hundred threats are attributed to him in Paris, in the west of France and in Hauts-de-France.
The results
The Paris public prosecutor’s office has opened an investigation for “fraudulent access and maintenance in an automated data processing system” and “fraudulent introduction of data”.
Mine clearance brigades moved to check for the presence of explosives.
On March 21, the Île-de-France region announced that it had suspended all ENTs in the region.
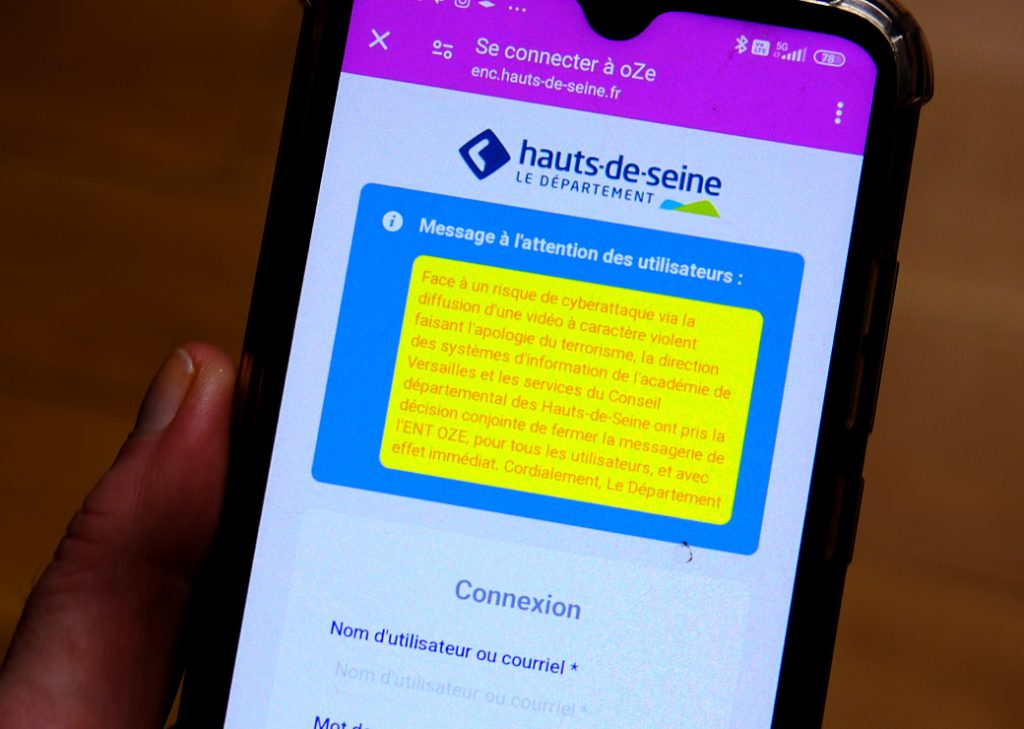
Nicole Belloubet, the Minister of National Education, announced that she would temporarily suspend all ENTs in France.
“Following the hacks and threats, I decided to preventively suspend all messaging in digital spaces in our schools,” the minister explained on X.
It is planned to strengthen the IT security of all ENTs.

The FFF victim of hacking and data theft of 1.5 million licensees
On March 22, 2024, the French Football Federation (FFF) announced that it had been the victim of a major computer hack. The personal data of 1.5 million licensees may have been compromised.
Compromised information includes:
- Names.
- First names.
- Dates of birth.
- Postal addresses.
- Emails.
- Telephone numbers.
- License numbers.
“Only data relating to license applications for the 2022-2023 and 2023-2024 seasons are likely to be affected. Passwords, bank details, medical data and identity photographs are, however, not affected,” indicates the Cybermalveillance site in a press release.
The FFF reacted promptly to the attack by:
- Filing a complaint with the courts: an investigation is underway to identify those responsible and bring them to justice.
- Informing the CNIL: the National Commission for Information Technology and Liberties was informed of the incident in order to ensure compliance with legal obligations regarding data protection.
- Taking measures to strengthen the security of its IT systems: the FFF has implemented corrective measures to limit the risks of future attacks.
- Communicating with licensees: the FFF informed licensees of the attack and provided them with advice to protect themselves from potential risks.
“The potential consequences of this case concern the different forms of phishing, attempted scams or identity theft of which the people affected by this incident could be victims,” indicated Cybermalveillance.gouv.fr.

Leak of 1.5 million LDLC customer data
On March 1, 2024, LDLC, a major player in the sale of computer equipment in France, suffered a major cyberattack. This intrusion resulted in the personal data of 1.5 million customers being compromised, an alarming figure that highlights the seriousness of the incident.
Epsilon Group claimed responsibility for the cyberattack and data theft.
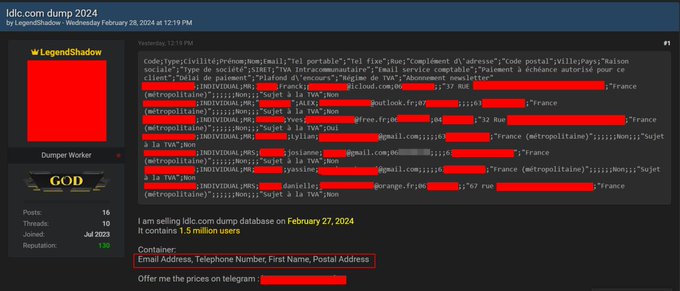
Hacked information includes a wide range of sensitive data, such as:
- First names,
- Names,
- Email addresses,
- Telephone numbers (mobile and landline),
- Postal addresses,
- Customer identifiers.
We also find information related to professional customers, including:
- Company name,
- SIRET number.
- VAT number.
LDLC reassured its customers by specifying that banking data and passwords were not affected.
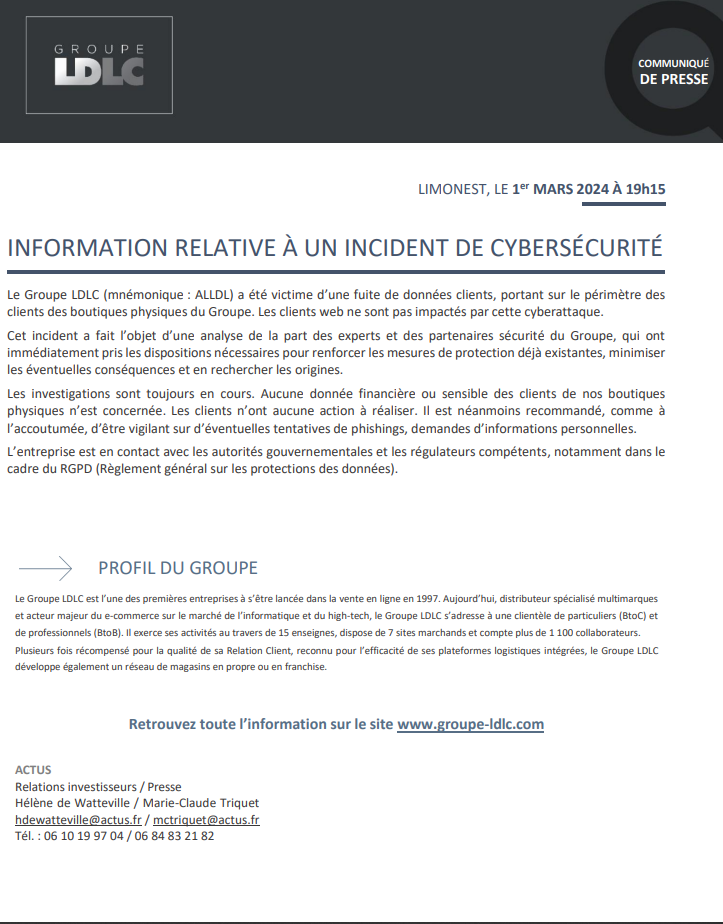
The LDLC group declared: “The LDLC Group (ticker: ALLDL) was the victim of a customer data leak, relating to the scope of customers of the Group’s physical stores. Web clients are not impacted by this cyberattack. »

Critical flaw in FortiClient EMS
On March 21, 2024, security researchers published a technical analysis and proof of concept (PoC) for the critical remote code execution (RCE) vulnerability, CVE-2023-48788, in Fortinet’s FortiClientEMS.
This vulnerability, with a severity of 9.8, allows an unauthenticated malicious actor to reach the RCE via manipulation of SQL commands.
Note that the vulnerability exploiting improper neutralization of special elements used in an SQL command (“SQL Injection”) [CWE-89] in FortiClientEMS may allow an unauthenticated attacker to execute unauthorized code or commands via queries specially designed.
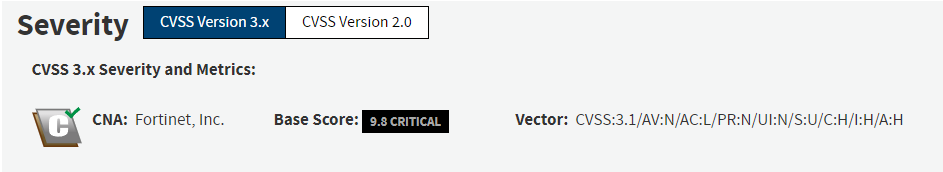
Fortinet said this vulnerability was being actively exploited. The PoC exploit code is also now publicly available.
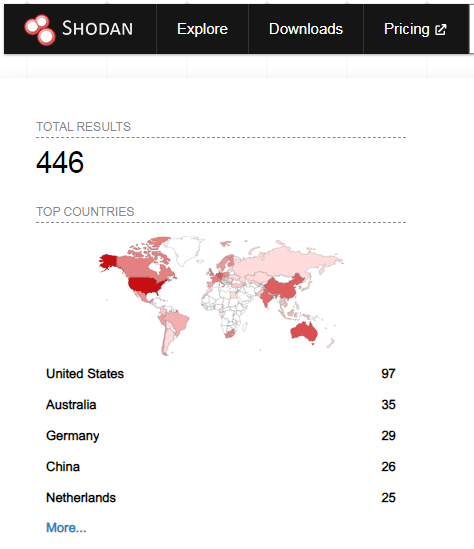
A search on Shodan shows that there are currently 446 FortiClient EMS servers exposed on the Internet, including 13 in France and Canada, 8 in Switzerland and 4 in Belgium.

A final of an Apex Legends e-Sports competition suffers a live cyberattack
On March 18, 2024, the Apex Legends Global Series Regional Finals for the North American region was interrupted by a live cyberattack. Hackers have managed to install cheat software on several players’ PCs, giving them an unfair advantage.
The course of the cyber attack
The attack took place right in the middle of the final. Spectators noticed that some players, including Noyan “Genburten” Ozkose and Phillip “ImperialHal” Dosen, were behaving strangely. They suddenly seemed to have a precision and knowledge of the map that was impossible to explain.
NO WAY @Genburten getting hacked mid algs game pic.twitter.com/PaVOjmnEGs
— Apryze🌹 (@Apryze_) March 18, 2024
By analyzing the footage of the competition, it appeared that the hackers had managed to install cheating software on the players’ PCs. This software gave players several advantages, including:
- Aimbot : visée automatique des ennemis.
- Wallhack : vision des ennemis à travers les murs.
- Speedhack : augmentation de la vitesse de déplacement.
The attack had a major impact on the competition. Players who fell victim to the cheating were forced to log out, and the final was postponed.
“Due to the competitive integrity that has been compromised, we have made the decision to postpone the North American Finals at this time. We will provide more information soon,” Electronic Arts said.
Respawn Entertainment, the developer of Apex Legends, has opened an investigation to determine the origin of the attack. The company also announced that it is implementing new security measures to protect players.

Duvel Moortgat brewery shut down due to cyberattack
On the night of Tuesday March 5 to Wednesday March 6, 2024, the Belgian brewery Duvel Moortgat suffered a cyberattack which forced the company to shut down its activities.
The Duvel brewery was the victim of ransomware by pro-Russian hackers “Stormous”.
On March 6, a spokesperson said: “The IT division was immediately informed of the attack. The servers were shut down and production was halted in all the group’s Belgian breweries, as a safety measure. […] The IT division is doing everything possible to restart the servers as quickly and safely as possible. The impact should be limited and there are more than enough stocks currently. »
On Thursday March 7, 2024, the Belgian brewery Duvel Moortgat announced that production had resumed at its Breendonk site after a cyberattack which forced the company to interrupt its activities for two days.
The group’s other sites, in Oudenaarde, Antwerp and Achouffe, were also put on pause and have now been able to resume their activities.
The ransom demand
A journalist from Laatste Nieuws was able to get in touch with the activist group “Stormous”.
The hackers discuss their demands regarding the ransom: “We cannot mention the exact amount, because it depends on the negotiations of our subcontractor,” they explain. “The negotiations are aligned on the exact damage caused by the attack on the victim. But the amount we initially demanded is more than $500,000 (456,000 euros),” the hackers add.
The Duvel group has not commented on its comments, however the hackers are threatening to disclose the stolen information, proving the cybercriminal group’s loss of patience.

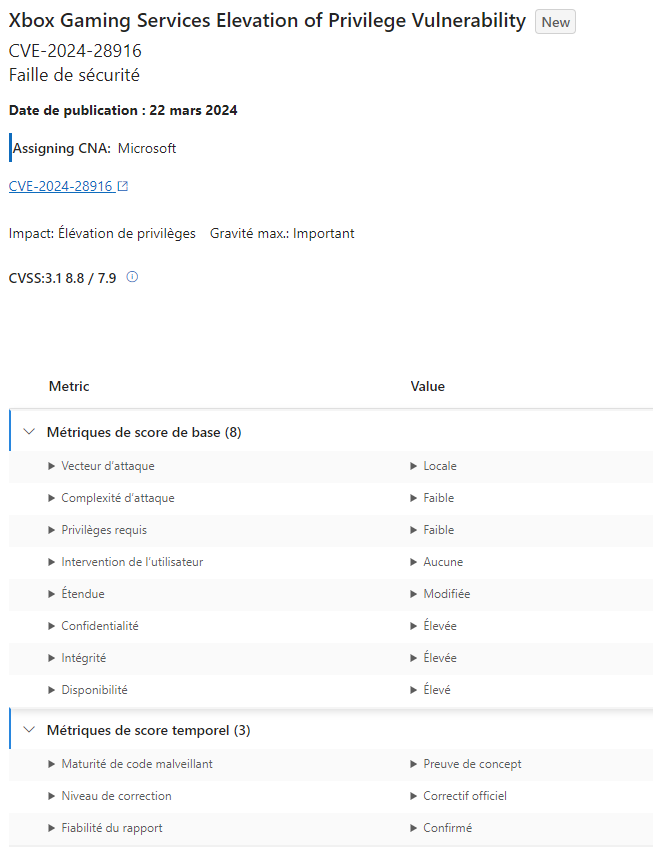
Xbox: Significant security flaw discovered
On March 20, 2024, Microsoft revealed a significant security vulnerability in its Xbox Gaming services. This flaw, with a criticality level of 8.8 and named CVE-2024-28916, could allow an attacker to obtain system privileges on a user’s Xbox console.
“An attacker who successfully exploited this vulnerability could gain system privileges,” Microsoft says.
Microsoft very quickly released a security update to correct the flaw. It is important that all Xbox users install this update as soon as possible.

Two engineers take control of a Tesla
Talal Haj Bakry and Tommy Mysk, two engineers, managed to take control of a Telsa very easily. In a video posted on YouTube on Thursday March 7, the two engineers demonstrated how to steal connection information in order to take control of a Tesla.
The course of events
The two researchers used a handheld device called Flipper Zero. This tool is designed for hackers and offers a variety of features, such as programming smart cards, analyzing radio signals, and creating fake WiFi hotspots.
They managed to hack Tesla’s software by creating a fake WiFi hotspot near a Supercharger charging station.
Tesla drivers, thinking they were connecting to a legitimate WiFi hotspot, were duped into entering their credentials on a fake web page mimicking Tesla’s interface.
In possession of this information, the hackers were able to remotely access, unlock and start the victim’s vehicle, even with multi-factor authentication enabled. According to the researchers, the latter can be easily circumvented.
Tesla does not recognize this vulnerability as a security flaw, arguing that phishing is distinct from traditional hacking. However, this situation raises real concerns about the security of Tesla users, particularly those who are less vigilant or less aware of the risks associated with phishing.

Bug Bounty: France, Blablacar, SNCF & Google
After France Public, Démarches Simplifiées
Like France Identity and its bug bounty at the beginning of the year, the French State has decided to set up a Bug Bounty for its service for simplifying online procedures, called “Démarches Simplifiées”.
Blablacar relaunches its program
After a session in July 2023, the carpooling giant is relaunching its Bug Bounty service at the beginning of March.

The SNCF is moving ahead
In view of the Paris 2024 Olympic Games, SNCF is opening its SNCF Connect&Tech application to Bug Bounty in public.
For 6 years, the leader in French trains has allowed the public to find security flaws, with €10,000 up for grabs for the most critical flaws.
Google spent $10 million in 2023 on Bug Bounty
In 2023, Google distributed $10 million in bug bounties to security researchers around the world.
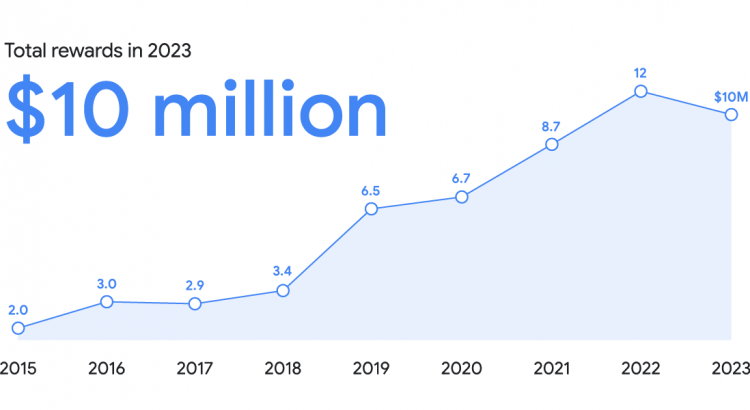
This initiative is part of the company’s bug bounty program, which aims to encourage the research community to identify and report security vulnerabilities in its products and services.
Google’s bug bounty program rewarded 632 researchers from 68 different countries. The highest bonus paid in 2023 was $113,337. The amount of bounties depends on the severity of the vulnerability discovered and the ease with which it can be exploited.

The SensCyber initiative opens to the general public and to VSEs & SMEs
In June 2023, ANSSI, the National Information Systems Security Agency, set up the SensCyber system exclusively for public service agents.
SensCyber is a free French program to raise awareness of cybersecurity risks, available on the website www.cybermalveillance.gouv.fr.
Faced with the critical success of this initiative, the state announces the opening of this system to the general public at the end of March 2024.
SensCyber aims to educate and test your cybersecurity knowledge through educational resources and interactive tests. It is aimed at all audiences, novices or experienced.
“9 out of 10 French people have already been victims of a threat. If technical security is essential, the human factor is also decisive in protecting yourself. This is why, after having been offered to 5 million public service agents, we decided to extend this e-awareness to businesses and the general public, who more than ever need simple tools to adopt the right reflexes in the face of attacks. Completely free, SensCyber is a cyberResponsible initiative and, like our mission, is part of a public interest approach,” explains Laurent Verdier, Director of the Awareness division of Cybermalveillance.gouv.fr
The 3 modules of SensCyber
SensCyber offers cybersecurity training divided into 3 distinct modules.
1. Understand
This first module aims to establish a solid foundation in cybersecurity. It’s about understanding the nature of the threats that exist on the internet, the risks to which you are exposed as an individual or organization, and what to do if you are the victim of a cyber attack.
2. Take action
This module aims to adopt and master the key actions for responsible daily use of digital technology (mobile phones, social networks, etc.) and better digital hygiene.
3. Transmit
This module contains:
- Understand the importance and means of sharing these values, both in private and professional life, due to the growing overlap of digital uses.
- Know how to identify public actors to contact in the event of an attack, to receive and provide optimal support.
What does the SensCyber initiative offer?
SensCyber stands out for its ease of access and its innovative educational approach:
Free and open to all
You don’t need to be a computer expert to take advantage of it. SensCyber is designed for the general public, whether you are a complete novice or a more experienced user.
Interactive and fun learning
No more boring lectures! SensCyber relies on varied and stimulating formats to capture your attention. Expect short, dynamic videos, quizzes to test your knowledge, and other interactive elements that will make learning more enjoyable.
Varied and concrete subjects
SensCyber addresses a wide range of online threats that you may encounter on a daily basis.
Learn :
- How to identify and protect yourself against common dangers like phishing, fraudulent emails that attempt to steal your personal information.
- Yhe importance of creating strong, unique passwords for each online account.
- Way to recognize and protect yourself against malware (malicious software).
- Social engineering techniques used by hackers to manipulate you and trick you into disclosing your confidential information.
