Malvertising
In this blog article, we will explain everything about Malvertising, how it works, the risks, but also how to protect yourself against it.
Nowadays, advertising is an integral part of our life. We find it on television, in the streets, in the cinema and on the Internet.
These advertisements have become more and more intrusive, so much so that extensions like ad blockers have appeared, preventing the display of pop-up, banner or video advertisements from appearing.
On the Internet, advertisements are regulated by companies such as Google or Taboola. However, sometimes these advertisements such as banners are infected with malware, this is called Malvertising.
In this blog article, we will explain everything about Malvertising, how it works, the risks, but also how to protect yourself against it.
Malvertising, what is it ?
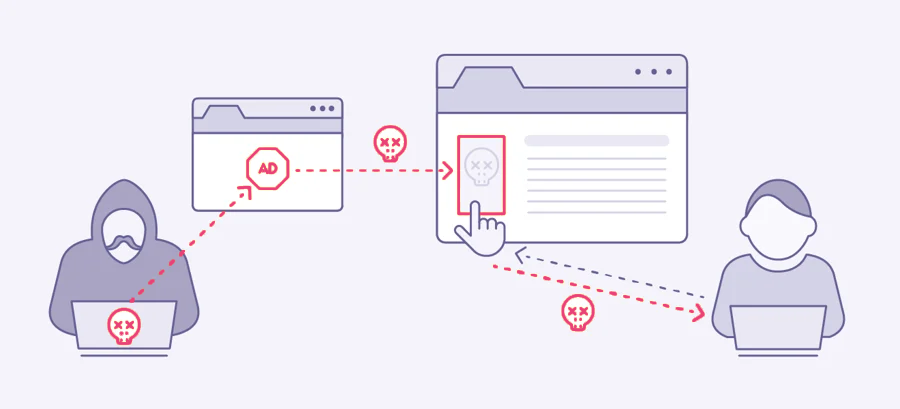
Quite simply, Malvertising is a type of cyberattack whose propagation medium is advertising space on the Internet.
Cybercriminals go through more or less dubious advertising networks to place ads and advertisements on trusted sites or sites with fairly high traffic.
The purpose of malicious ads is obviously to reach as many people as possible.
These advertisements can infect a surface in two different ways :
- Either the Internet user clicks on the advertisement displayed and therefore arrives on a malicious site.
- Either, the malicious code of the advertisement infects the victim as soon as the advertisement has loaded on the site, therefore without the Internet user interacting with it.
Whether it is the 1st case or the 2nd, it is often too late.
The risks of Malvertising
Finally, what does a victim risk when a malicious ad infects their surface ? There are several scenarios.
Theft of confidential data
Data theft is very common in the world of cybercrime.
It is thanks to spyware that installs itself on the victim’s computer or via a form on a malicious website that hackers can steal data.
These will then be resold on the Dark Web to other cybercriminals wishing to steal identities.
Theft of payment information
Like the theft of personal data, the theft of payment information can be done either via spyware or via a form on a fraudulent site.
However, stealing payment information is more serious than just confidential data.
Indeed, the information can be resold but also used by cybercriminals for various purchases on sites that do not require double authentication or bank verification.
The ransom demand
The malware present in the infected ad installs on your computer and will block and lock your files.
From there, the criminals will demand you a ransom in exchange for releasing your files.
However, we advise you not to pay, and recommend that you file a complaint.
Indeed, there is no guarantee that once the ransom has been paid your files will be returned to you, nor how many.
And nothing assures you either that the hackers did not make a copy of these files to resell them or use them later.
The site cybermalveillance.gouv.fr, the French government site on cybersecurity, advises to never pay a ransom.
Sabotage
Sabotage means destroying and rendering an Information System out of service via a virus.
The case of sabotage is quite rare for individuals or businesses in general.
This concerns more institutions, States and other essential services for countries, in this case, we are talking about Cyberwar, we refer you to our dedicated article.
How does Malvertising work ?
Here is how a Malvertising attack works :
- A cyberattacker acquires advertising space from a site or a network.
- It provides an infected ad with the aim of displaying it in the rented space.
- Malvertising is triggered when :
- The Internet user clicks on the malicious ad.
- The site loads the malicious advertisement, infecting the device. These kinds of ads can attack a device without the need for victim action.
Malvertising cyberattacks take many different forms and strategies.
Steganography
Used since Antiquity, this technique consists of hiding information in other information, such as hiding a message in an image, or a text.

This is the most used ploy in the field of Malvertising.
Concretely, cybercriminals inject malicious content into an image by altering a few pixels of the latter.
Obviously, this change is imperceptible to the naked eye so that neither the Internet user nor the advertising agency can take note of this change.
Image Polyglot
The principle of Polyglot Image is similar to that of Steganography but more sophisticated.
In addition to containing malicious code, these images contain and conceal scripts that can execute the code and launch the attack against the victim.
Once the malicious ad containing the image is loaded on the site, the victims quickly get infected as soon as the ad is loaded. They are therefore autonomous and extremely dangerous cyberattacks.
Fake Tech Support
Imagine, you’re browsing the Internet, and suddenly a blue screen appears telling you that your computer is having a major problem (another version is the blocking of the screen by the so-called “police” for acts that the victim allegedly committed).
This blue screen asks you to call a number pretending to be Windows Technical Support.
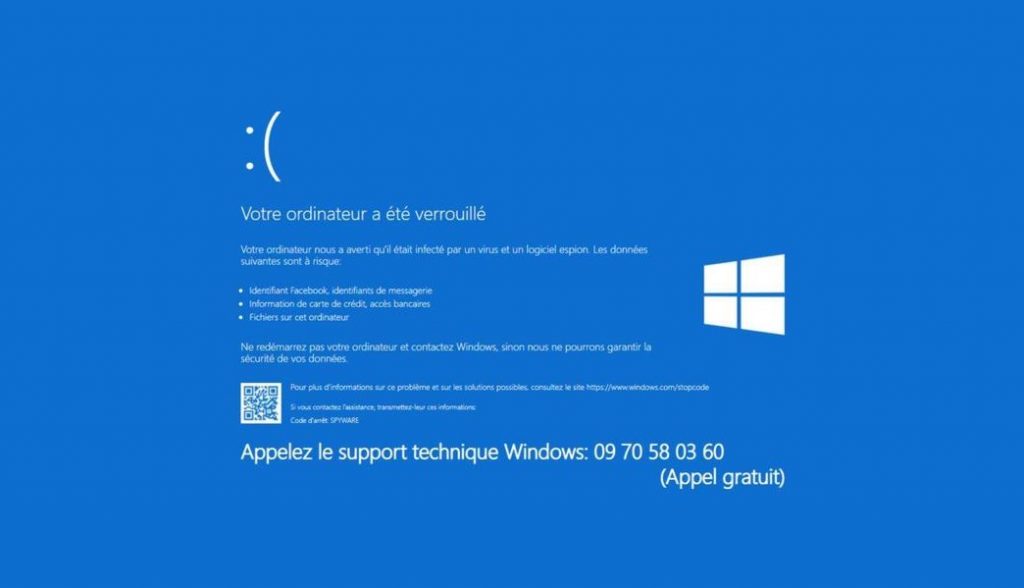
You call this number, and there you are caught in the trap. Because the person you called is not a technical support technician, but a scammer who will ask you for confidential information and will try to extract as much money as possible from you.
In fact, the blue screen isn’t anything serious or alarming, it’s just browser hijacking malware faking a glitch. Be aware that this blue screen is easily diverted using the Windows console.
Scareware
Like fake technical media, the Scareware works in the same way by scaring the user with a blue screen of technical error or a message from the “police”.
But here, the message that appears on the screen does not ask to call a certain number but rather to install an “anti-virus” to correct the blue screen.
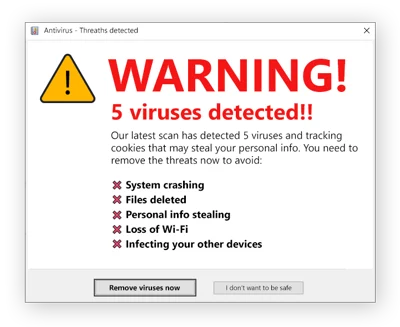
However, and you can guess it, the “anti-virus” is actually a virus itself infecting the victim’s computer or surface.
Clickbaits
I call Clickbaits advertisements promising you mountains and wonders, like “You will get rich in 5 minutes”.
Mostly these ads hide viruses, which will get launched on the victim’s device as soon as he clicks on the fake advertisement.
Another version of these clickbaits also concerns the software update. The Internet user can see an ad indicating a Chrome update, he clicks on it and downloads the famous update which is not one, but which is above all potentially a virus.
Examples of Malvertising
We will briefly discuss various cyberattacks using the Malvertising technique.
2020 – COVID-19
During the Coronavirus pandemic, cybercriminals, targeting older versions of Internet Explorer, created an ad prompting Internet users to respond to a COVID-19 advisory.
Obviously, once Internet users have clicked on the ad, malware is installed on their computer, stealing users’ personal information and passwords.
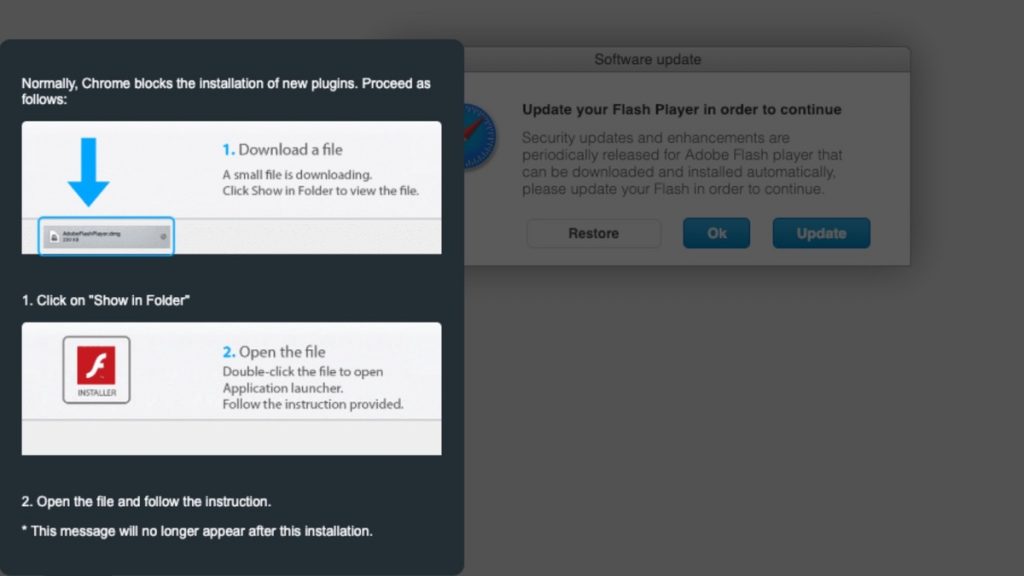
2019 – VeryMal
In 2019, a cyberattack, named VeryMal, hit Mac users. She was using the steganography ploy.
A hidden code redirected users to a fake website that installed the Shlayer Trojan on their machine, this virus was disguised as a Flash update.
2016 – AdGholas
The Malvertising AdGholas cyberattack hit Yahoo, MSN and other big names with fake advertising for privacy software.
With no requirement for user interaction, the steganography-based ad redirected victims to a malicious page and installed malware using multiple Flash exploits.
Cybercriminal group AdGholas even managed to get their fake privacy protection tool added in the Chrome store as an official plugin.
2013 – Yahoo
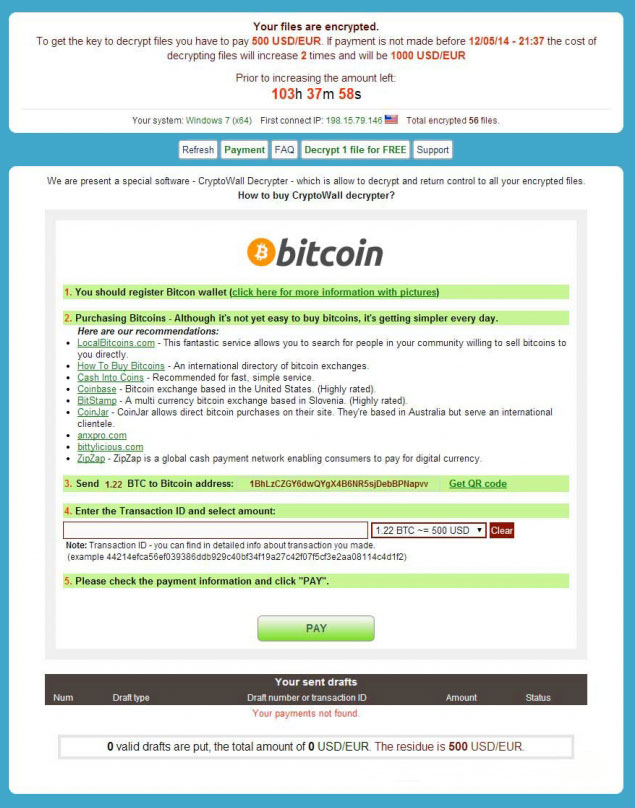
A major malvertising campaign was waged against Yahoo.com, one of the largest advertising platforms with 6.9 billion monthly visits. The malware exploit was based on Cross-site scripting (XSS).
The attack infected users machines with Cryptowall ransomware, a type of malware that extorts money from users by encrypting their data and placing a ransom of up to $1,000 in bitcoins, to be paid in seven days, to decrypt the data.
Counter Malvertising
To counter malvertising, several measures can be taken :
An ad blocker
An ad blocker allows, as its name suggests, to block ads so that they do not appear and thus avoid the risk of infection by a malicious ad.
However, be aware that more and more sites and advertising agencies are deploying means and strategies to circumvent ad blockers and thus display their ads.
A firewall and antivirus
Having a firewall and an antivirus is essential today when you own a computer.
The increase in the number of viruses, phishing attacks and ransomware today forces Internet users to protect themselves against these threats.
Regularly update your software and operating system
Indeed, often in the case of malware, attackers exploit unpatched vulnerabilities.
Updating therefore reduces the risks because the publishers correct the security vulnerabilities.
Use a secure web browser
Some internet browsers have increased protection against cyberattacks such as Malvertising and other threats.
Be aware that Chrome is not necessarily the best choice in terms of cybersecurity against malicious ads, but it is not the worst either.
Limit the use of plug-ins in your browser
Some plug-ins have security vulnerabilities that can be easily exploited by a hacker.
Limiting the use of plug-ins reduces a possible risk.
Use a vulnerability scanner
These kinds of solutions can detect if computer security vulnerabilities are present and tell you how to fix them.
Use cyber threat intelligence software
What does this kind of tool do? Quite simply, it helps to check if your data has not been stolen and made available on the Web, Deep Web and Dark Web.
We are here in the event that the cyberattacker has managed to steal your data and therefore your surface has been infected.
And above all : Be careful!
This may seem like futile advice, but most of these malicious ads are present on rather dubious or considered illegal sites (illegal streaming sites for example), so we recommend you to be careful.
It is better to be safe than sorry!
