Vulnerability in SSL checkers
Most SSL certificate testing tools, which rely on data in certificates issued by certification authorities, have been vulnerable to XSS attacks conducted with a self-signed certificate. Discover them!
Abstract
Many services on the internet allow to check SSL Certificates. They display information about certificates and indicate if they are valid and well configured.
JavaScript Injection:
With OpenSSL library, it is easy to create a self-signed SSL Certificate with the information you want. You can thus create and install a fake SSL certificate like this one :
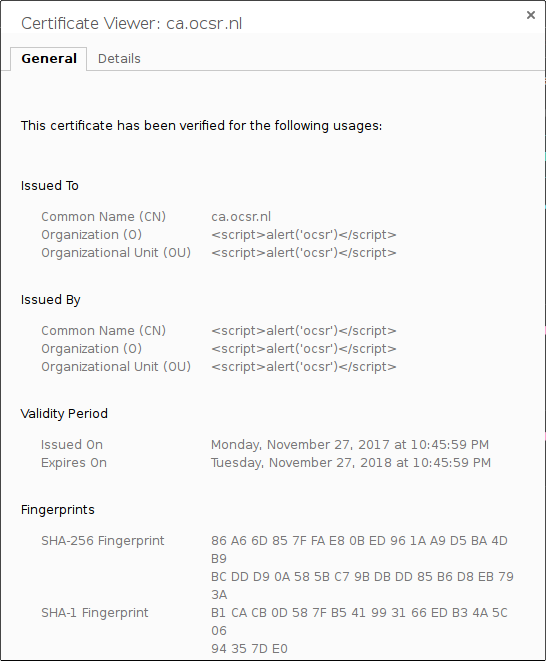
This certificate contains XSS injections in several fields. So the question is : what happens if you test this SSL Certificate with online checkers ?
This was tried a few days ago on several of these services, among the most famous :
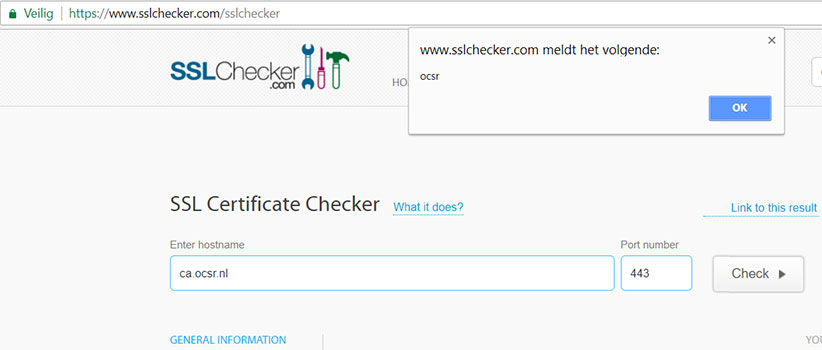
1. SSL Cheker:
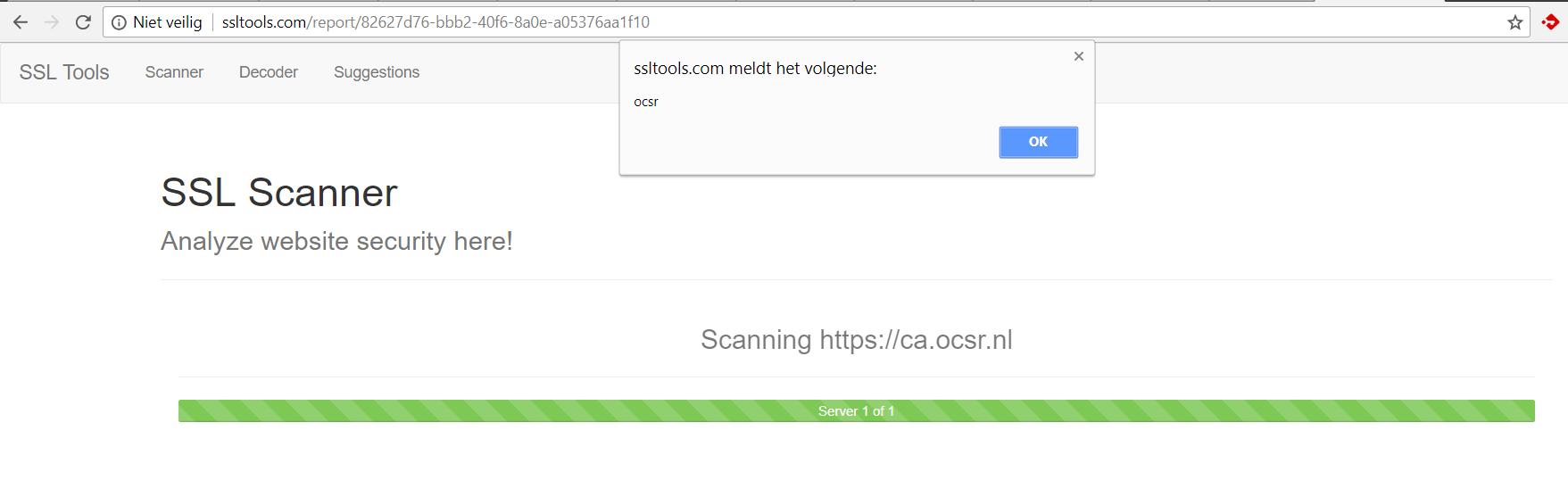
2. SSL Tools :
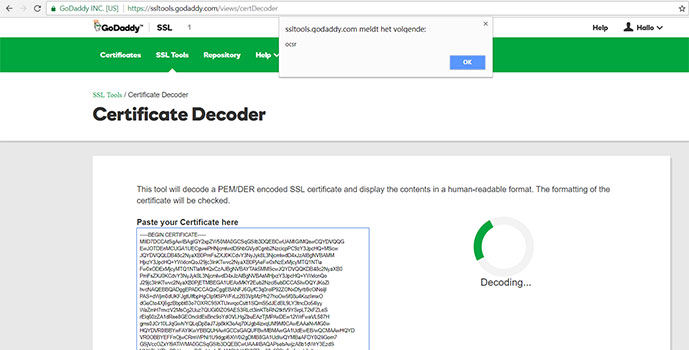
3. SSL Tools Go Daddy :
4. Go Get SSL:
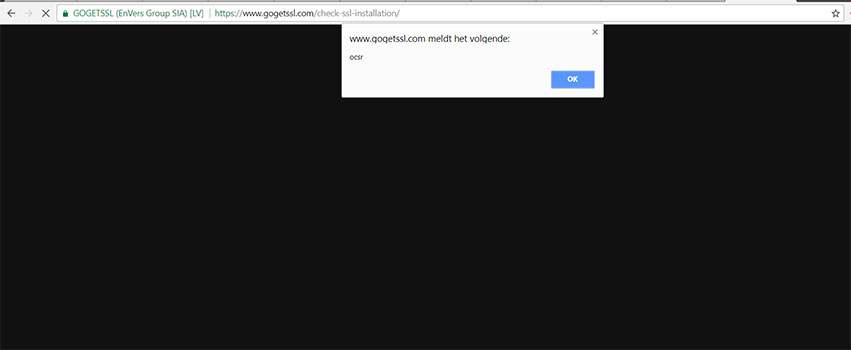
5. SSL 2 Buy :
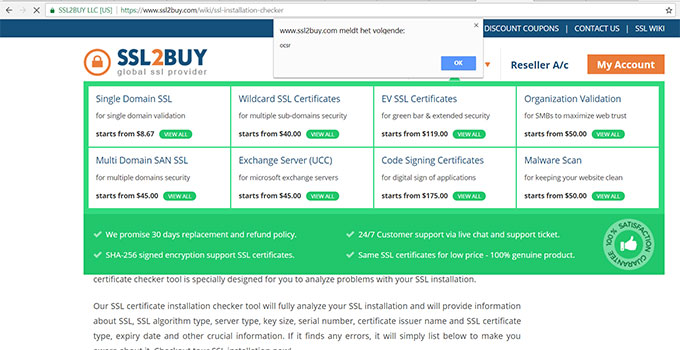
6. UK Fast :
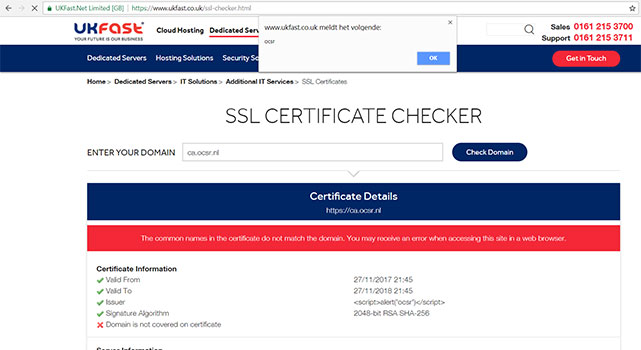
7. Trust Ico :
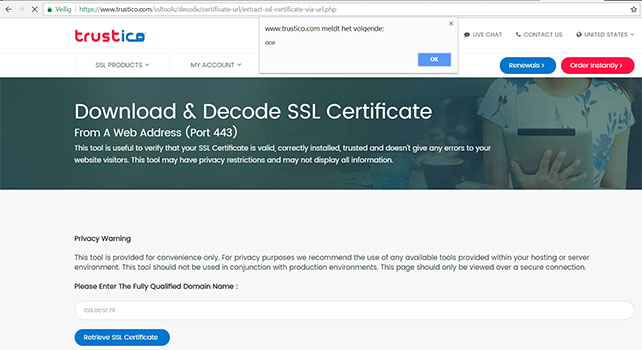
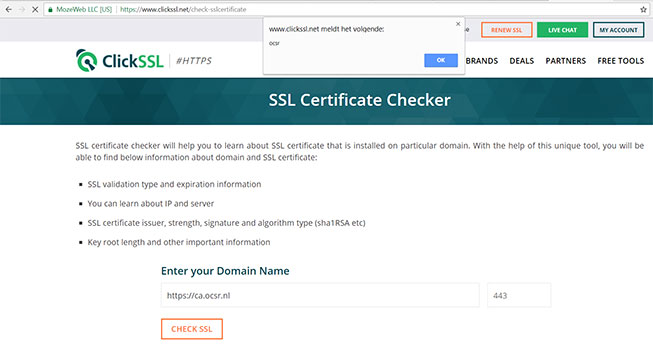
8. Click SSL :
9. Comodo SSL Store :
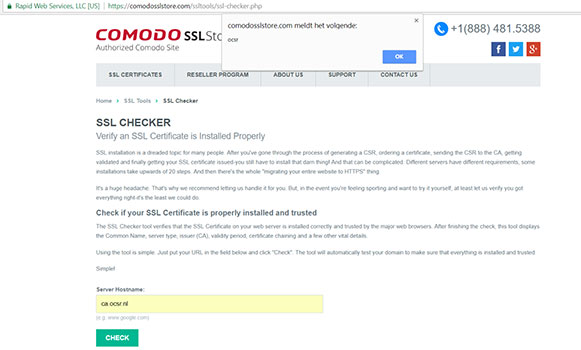
These tools, which trust data present in certificates issued by SSL authorities, were vulnerable to XSS attacks with a self-signed certificate. They were quickly patched or set into maintenance.
HTTPCS SSL Checker
HTTPCS also offers an online SSL checker (https://www.httpcs.com/en/test-ssl-certificate) but this one is not vulnerable to this type of attack.
In the end, this example is a perfect illustration of the adage well known by web developers : « Do not trust user data ». For more details about XSS flaws, please have a look at our briefing note : https://www.httpcs.com/en/cross-site-scripting-xss-vulnerability
