Criteria for choosing a web vulnerability scanner
Many factors are paramount for choosing a vulnerability scanner for a site and a web application. Between security, reliability towards the general public and, compliance with applicable laws, monitoring its website is a major issue.
Security of your website: would you be ready to play your business as with a shot of poker?

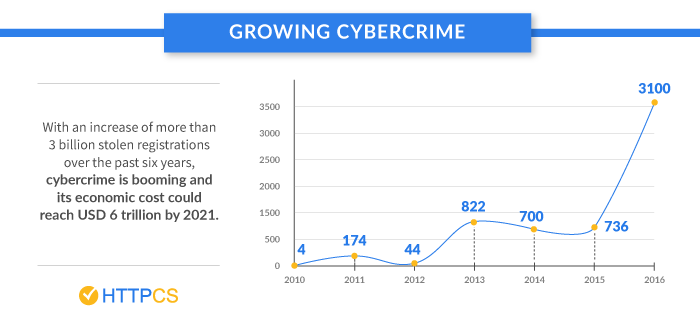
In the France of 2017, did you know that:
-
- companies have identified 4550 incidents equivalent to about 12 a day, which is an increase of 9% compared to 2016?
-
- only 3 out of 4 French companies have defined a cybersecurity strategy.
- 53% of French companies do not train or educate their employees.
(Source : Axess OnLine)
Thanks to the vulnerability scanner, you can identify the flaws of your website or web application to correct them and protect you from possible risks.
Vulnerability scanner: real-time monitoring
At the speed with which technology advances – and with it, hackers – monitoring its website 24/7 is essential for the sustainability of a web-based company.
Using a vulnerability scanner will help you to:
- Measure in real time the security of your website;
- Anticipate any possible attacks by taking the necessary measures.
12 criteria have been identified to guide you in choosing your future vulnerability scanner:
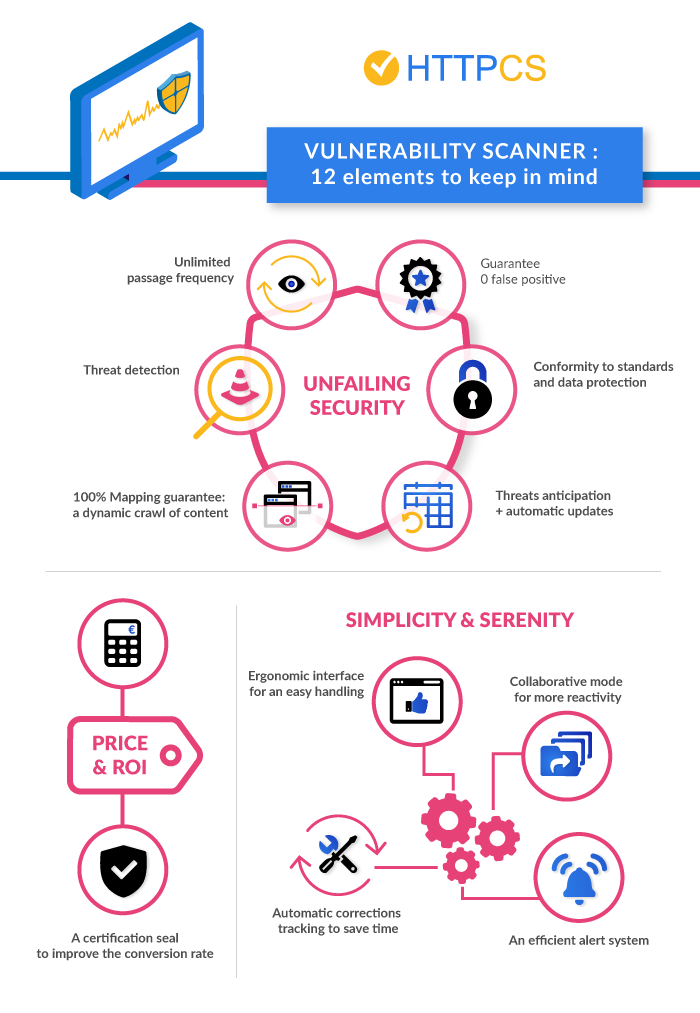
- Machine Learning
- High-performance threat detection
- 100% Mapping: ability to audit all your services without exception!
- Anticipation of threats and update of the tool
- Compliance with standards
- A quick and easy to use interface
- Automatic correction tracking to save time
- A collaborative mode for more responsiveness
- Detailed Reports for Immediate Corrective Action
4. HTTPCS: a complete and reliable SCANNER from €55/month
1. Seamless security
False positive management:
A false positive is a threat that is not yet real at the time of the scan. Some scanners show them as flaws when they are not. As a result, you waste valuable time dealing unnecessarily with these false alerts.
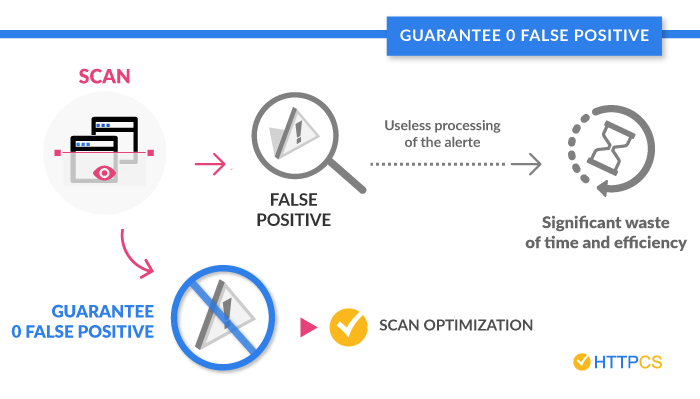
A good vulnerability scanner must be able to provide a zero false positive rate.
Machine Learning:
The essential thing to know about the concept of Machine Learning:
Machine Learning is a set of methods that allows “computers” to learn and detect anomalies without being explicitly programmed for it.
In other words, it’s an automatic learning algorithm that will discover and formalize the data it sees to conclude whether there is a failure or not.
High-performance threat detection:
A good site vulnerability scanner should not distinguish or categorize threats according to their nature, but only according to their reality (no false positives) and their severity (its consequences on the entire system).
So, whether it’s hacking sites, using a password that has been encrypted or violating a database – every threat must be treated the same.
This is the only way to ensure full detection of threats. Although the OWASP Top 10 is the international reference for most common threats, it is important that the scanner goes beyond that.
HTTPCS offers two formulas for managing threat detection:
- The Gray Box offer, meanwhile, consists of trying to get into the information system by having a limited amount of information on the organization and its system. This case makes it possible to check the flaws of a system by positioning itself either as a collaborator of the company having access internally to some information, or as the starting point of a hacker who would have managed to have access to a user account within the organization;
- The Black Box offer, aims to get into a system (the box) without having any information, such as a hacker discovering this system for the first time. The pentester then has no knowledge of the environment and tests blindly. So, from the outside, his goal is to find out how to get into the target system as an outside attacker could do.

100% Mapping: ability to audit all your services without exception!
-
Browse the web like a real hacker!
The effectiveness of a scanner is also gauged by its ability to cover the entire tree structure of a site and therefore to make of it a total mapping: intranet, extranet, commercial sites,…
The crawl (or indexing) must be sufficiently active so that the navigation of the robot is free of any limit and that it browses inside the site as an Internet user would do. The analysis should therefore be able to extend to the most dynamic pages (like Javascript). This ability is essential because a hacker will go to the trouble of exploring all its possibilities and the robot will have to be able to compete with it.
-
Test all applications
The scanner should also allow you to scan all your applications even those in production.
Anticipating threats and updating the tool
- Would not it be ideal to have a scanner that could predict an attack even though it has not started? This is feasible if your robot can browse the dark web, on hacker forums and all their gathering points. The goal is to be able to acquire strategic information. The great attacks are often prepared there, are the subject of some publicity. It becomes possible to spot them.
- An anticipation of the threats which is accompanied by an automatic and regular update of your tool. This update must incorporate recent advances in technology.
HTTPCS places cyber-vigilance among its priorities, especially its presence and infiltration with hackers. Discover CYBER VIGILANCE, a complementary product to the vulnerability scanner to enhance the security of your website.
Compliance with standards
The standards are there to indicate a qualitative minimum. The scanner must therefore reach at least these minima and more ideally, it must offer more.
- In the area of vulnerability of a site, the General Regulations on Data Protection (GDPR) mentions that its non-compliance puts your website in a hackable and criminal position vis-à-vis the Public Administration. The GDPR imposes a data protection for people browsing on your site as soon as there is collection, processing, sharing and storage on your part. Thus, by opting for a specialized provider – in accordance with this new regulation – you are assured of the security of the processing of your registers.
- ISO standards are also of paramount importance, even if they are voluntary. They define the reference either on the architecture of the site or on its environment (examples: ISO 27001 and 27002). By collaborating with a provider already holding an ISO recognition, you will be sure that the scans performed are up to standard.
 HTTPCS helps companies comply with the RGPD and ISO standards.
HTTPCS helps companies comply with the RGPD and ISO standards.
2. Ease and serenity
A quick and easy to use interface
In the face of a cyberattack, responsiveness prevails. With a vulnerability scanner that is responsive to any flaw or attempted attack, you’ll have a head start in taking immediate corrective action.
- The scanner will have to allow a simple and fast handling, ergonomic, without need for the user, to have advanced computer skills.
It is up to the vulnerability scanner to adapt to the context and people, and not the other way around. No technical skills need to be necessary.
- Do you have multiple websites to manage? A vulnerability scanner with a single interface to manage them all will facilitate monitoring and management.
- The choice of a responsive scanner, that is to say available on mobile and tablet, will work where and when you want.
At HTTPCS we have developed a vulnerability scanner that combines intuitive and ergonomic features. Our goal is to simplify, while remaining effective, the management of security alerts.
Automatic correction tracking to save time
- A good vulnerability scanner detects vulnerabilities in your system and offers fixes to apply.
- The important function here is automation. The scanner must repeat the tests as many times as necessary to see if the patches have been correctly applied. This repetition is the only guarantee of the real effectiveness of a proposed patch. Automatically, he notes the flaws as corrected.
A collaborative mode for more responsiveness
- At HTTPCS, the software offers the provision of a scan report. A document that mentions the faults identified, their level of criticality and a list of corrective measures to apply. Reports that can be archived and shared with the relevant officials, for simplified management.
- Another interesting option for the immediate management of alerts: the management of access rights. By setting up custom access rights settings, it is possible to allow remote access to the robot. An access which will allow the company of intervention in charge of the security of your web site, to simulate the attacks related to the detected faults, and to quickly apply the patches.
Detailed reports for immediate corrective action.
At the end of each scan done on your entire site, you will need to be able to retrieve a detailed report. The latter is sent by email to the manager of the site concerned, who will be able to access the list of detected faults and take the necessary corrective measures.
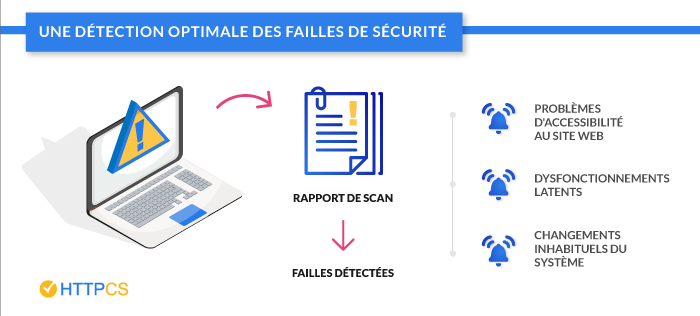
3. The return on investment:
The financial risks and the return on investment of a scanner:
- A vunerable site can lead to financial losses but also moral consequences. It is essential to choose a tool in which you can have full confidence, according to the criteria that we will present you in the rest of this article.
![The financial risks and the return on investment of a scanner-httpcs]()
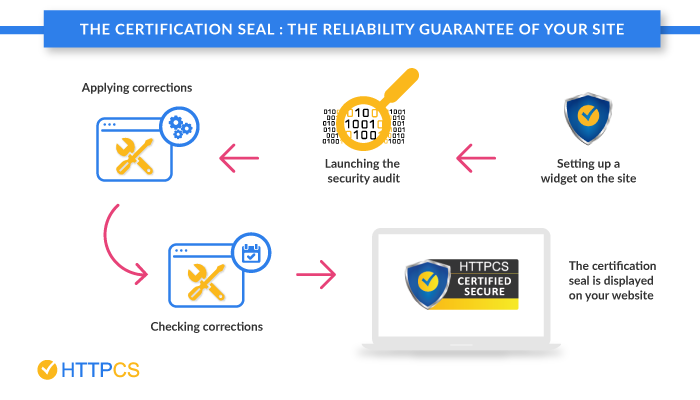
- Your scanner tool must offer you a certification seal – a sign from the provider certifying that no breach is found in your system and is therefore insured. A specialized service provider must be able to provide you with this service to sufficiently inspire confidence.
This seal, a true element of reassurance, will allow you to stand out from your competitors, increase your conversion rate and gain market share.
The price
Apart from the technical criteria, the question of price must not be neglected either because a vulnerability scanner must be usable 24/7. An exorbitant cost would not allow companies – especially SMEs – to be able to protect themselves from cyberattacks.

In choosing your future vulnerability scanner, you will need to consider all direct and indirect expenses that the scanner could generate:
- Cost of monthly or annual subscriptions;
- Cost of training (if needed);
- Cost of the installation itself (if a trip from the service provider is required) …
- Incidental costs such as the price of SMS alerts (if they are not directly included in the main offer) or if some services are provided with extras may also be required.
Finally, at the price level, it will be necessary to see if the offer includes a mandatory commitment clause or if the renewal of the contract implies a renewal.
The Gray Box, meanwhile, costs €240 monthly and the premium offer “Full” €399 per month. The whole is not subject to any prior commitment.
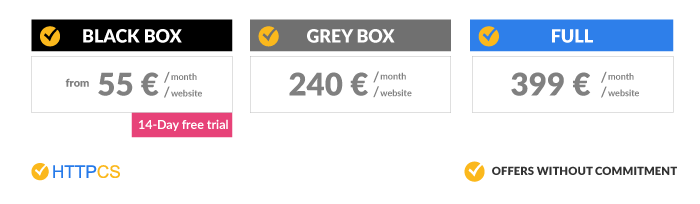
4. HTTPCS: a complete and reliable SCANNER from €55/month
HTTPCS is a known reference in the cybersecurity world. His certification seal is affixed to his clients’ sites whenever all the flaws have been corrected.
To ensure the security of its site, demonstrate its reliability vis-à-vis the public and compliance with applicable laws, choosing a good vulnerability scanner is therefore essential.
These twelve cumulative criteria must be studied, evaluated and verified. In this way, the relationship between the quality and price of this investment will be justified.
With HTTPCS by Ziwit, adopt the Secure Attitude and do not be afraid of being hacked.