CyberNews January 2024
Discover the CyberNews for January 2024. This is the recap of news on Cybersecurity during the month of January 2024.
Discover the CyberNews for January 2024. This is the recap of news on Cybersecurity during the month of January 2024.
Orange Spain
Orange Spain suffered a hack on Wednesday January 3, 2024. The attacker, calling himself “Snow”, managed to access an Orange Spain administrator account on the RIPE network, which manages the allocation of IP addresses in Europe, in the Middle East and Central Asia.
The attacker then used this account to modify internet traffic routing configurations, which caused significant disruptions to the Orange Spain network.
The operator’s customers have been experiencing internet connection issues, including slowdowns, outages, and disconnections.
Orange Spain reacted quickly to the attack and managed to restore the situation in the evening of the same day. The operator said customer data had not been compromised.
Here’s how the attack unfolded:
- The hacker used “infostealer” malware to steal the credentials of an Orange Spain employee.
- The malware was installed on the employee’s computer via a malicious link sent by the attacker.
- The Orange Spain administrator account was protected by a weak password, which facilitated access for the hacker (see image below).

Tietoevry & Sweden
A cyberattack paralyzed a data center of Tietoevry, a Swedish-Finnish IT services company, on the night of January 19-20, 2024.
Hackers used Akira ransomware to encrypt virtualization infrastructure servers, preventing access to sensitive data.
To limit the spread of the attack, affected systems were quarantined.
The unavailability of Tietoevry’s services has rendered many online purchasing systems, including cinemas and stores, inoperable. Some stores were forced to temporarily lower their curtains because of this cyberattack.
More importantly, this cyberattack caused disruption in some Swedish administrative services, as well as some schools and hospitals.
The centralized human resources system used by administrations, the Statens Servicecenter, has been paralyzed, preventing employees from carrying out certain administrative tasks.
In total, there are 60,000 affected workers and 120 administrations.
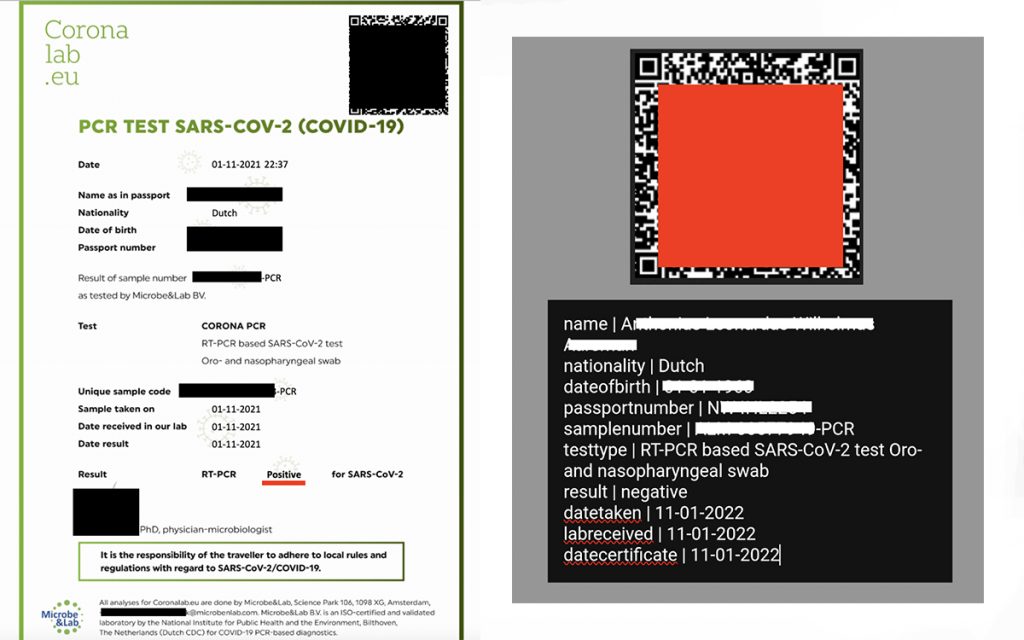
Coronalab
A major security breach has been discovered at Coronalab, a Dutch laboratory specializing in COVID-19 testing.
This flaw allowed hackers to access the personal data of more than 1.3 million patients.
The data was exposed following a security breach in a non-password-protected Coronalab database.
This data mainly included:
- 118,441 certificates.
- 506,663 appointments.
- 660,173 test samples.
The exposed data, all branded with the name and logo of Coronalab.eu, included:
- Patient names.
- Dates of birth.
- Passport numbers.
- Test results.
MyEstatePoint Property Search
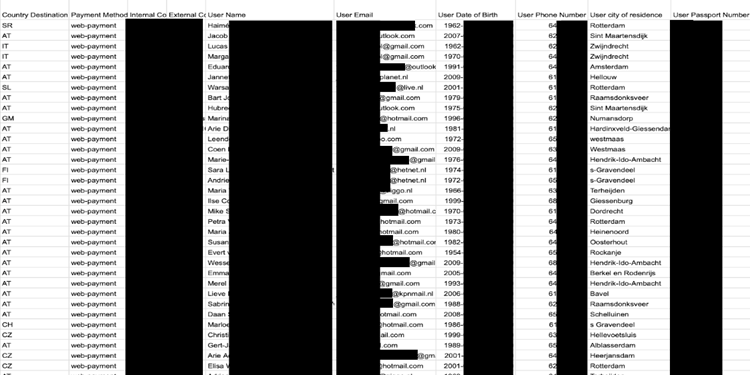
On January 5, 2024, the Cybernews Research Team revealed that a popular real estate application named MyEstatePoint Property Search left a MongoDB server containing sensitive data about its users open to the public.
The app, developed by Indian company NJ Technologies, has been downloaded more than 500,000 times, mainly by users in India.
The exposed server contained the following data on more than 497,000 users:
- Names.
- Email addresses.
- Clear passwords.
- Cell phone numbers.
- City information.
- Business descriptors.
- Registration methods.
According to the report, the research team found the server on November 6, 2023 and quickly contacted the developer about the issue. NJ Technologies never responded, but access to its server has since been closed to the public.
Ivanti Connect Secure VPN
In early January 2024, security firm Volexity released a report detailing two combined 0-days vulnerabilities that impact Ivanti Connect Secure VPN.
These vulnerabilities, which have been assigned CVE-2023-46805 and CVE-2024-21887, allow an attacker to execute arbitrary commands on a vulnerable system.
- The first vulnerability, CVE-2023-46805, is an authentication avoidance vulnerability that allows an attacker to log into a vulnerable system without the need for a password or security token.
- The second vulnerability, CVE-2024-21887, is a command injection vulnerability that allows an attacker to execute arbitrary commands on a vulnerable system.
When these two vulnerabilities are combined, they allow an attacker to access a vulnerable system without the need for a password or security token and then execute arbitrary commands on that system.
This ultimately allows the attacker to steal data, install malware or disrupt an organization’s operations.
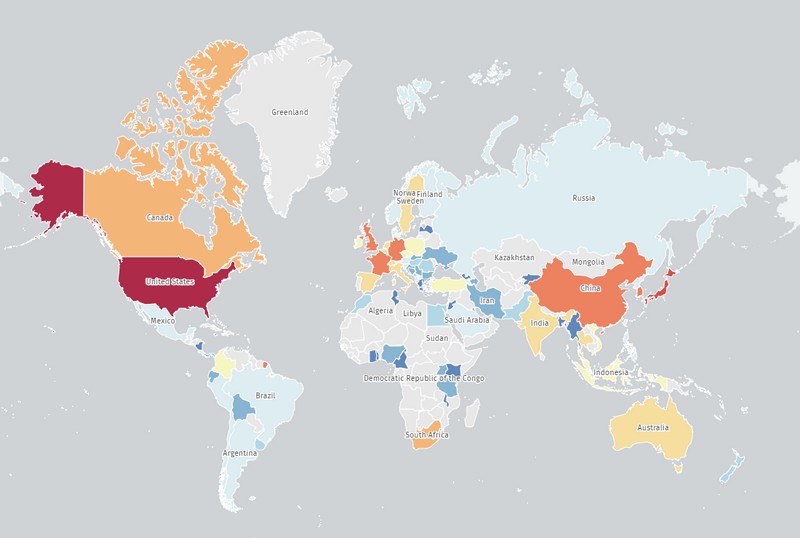
Invanti said: “Exploitation of these vulnerabilities is now widespread. Volexity was able to find evidence of over 1,700 devices worldwide being compromised. »
According to TheShadowServer’s map below listing the most affected countries, there are 289 vulnerable instances identified in France.
Ivanti has released a security update to address these vulnerabilities.
DeFi Gamma Strategies
In early January 2024, the DeFi Gamma Strategies protocol was the victim of a hack resulting in the loss of 1,500 ETH or approximately $3.4 million. The attacker exploited a flaw in the protocol’s accounting mechanism to withdraw an excessive amount of tokens.
Gamma Strategies is a DeFi protocol that allows users to generate returns by depositing their funds into liquidity pools. The protocol uses a complex accounting mechanism to track deposits and withdrawals of funds.
The attacker exploited a flaw in this mechanism to withdraw an excessive amount of tokens. The flaw was identified by PeckShield and BlockSec, two blockchain security companies.
Pwn2Own Automotive
Pwn2Own Automotive is a hacking competition dedicated to discovering and fixing vulnerabilities in connected vehicle technologies. It is organized by VicOne, a global leader in automotive cybersecurity, and Trend Micro’s Zero Day Initiative (ZDI), a leading bug bounty program.
The event challenges top security researchers to find and exploit vulnerabilities in real-world automotive systems. The goal is to identify and fix these vulnerabilities before they can be exploited by malicious actors.
The 2024 edition of Pwn2Own Automotive, held in Tokyo on January 27, was a resounding success. Researchers discovered and successfully exploited 49 vulnerabilities in the systems of 11 automobile manufacturers, including BMW, Ford, Honda, Hyundai, Kia, Mercedes-Benz, Nissan, Tesla, Toyota and Volkswagen.
The vulnerabilities discovered varied in severity, ranging from simple programming errors to critical vulnerabilities that could allow an attacker to take complete control of a vehicle. Among the most notable vulnerabilities, we can cite:
- A vulnerability in BMW’s infotainment system allowed an attacker to take control of the air conditioning system, lock the doors and activate the hazard lights.
- A vulnerability in Ford’s telematics system allowed an attacker to track the vehicle remotely.
- A vulnerability in Tesla’s charging system allowed an attacker to take control of the charger and cause a fire.
Forex UTIP
At the end of January, the website of Forex broker UTIP was hacked. The data of more than 700,000 customers was stolen, including:
- Names.
- Email addresses.
- Telephone numbers.
- IP addresses.
- Transaction information.
The attack was carried out by a group of hackers known as “ShinyHunters.” Hackers used a vulnerability in the MetaTrader 4 trading platform to gain access to UTIP’s computer system.
UTIP said it is investigating the attack and taking steps to protect customer data. The company also offered affected customers a free consultation with a cybersecurity expert.

Toronto Zoo
The Toronto Zoo is home to over 5,000 animals from over 460 species. Its mission is to connect humans, animals and conservation science to fight species extinction.
On January 5, 2024, the Toronto Zoo’s computer system suffered a cyberattack.
The attackers managed to gain access to the zoo’s computer system and steal sensitive data, including information about animals, employees and visitors.
The attackers used ransomware malware to encrypt the zoo’s data. They then demanded a ransom of $1 million in bitcoin to decrypt them.
The Toronto Zoo refused to pay the ransom and was able to recover the data using a backup. However, the attack caused significant disruption to the zoo’s operations, including the shutdown of its website and mobile app.
Here’s how the attack unfolded:
- The attackers used a ransomware malware called “Conti”.
- The malware was installed on the zoo’s computer system by an employee who clicked on a malicious link.
The Toronto Zoo has taken steps to strengthen its IT security, including strengthening access controls on administrator accounts and making employees aware of the risks of cyberattacks.
To learn more about the Toronto Zoo cyberattack, here is their official statement on their website.
GitLab
GitLab is an open source software development platform built on top of Git version management software. It allows development teams to collaborate on software projects, manage versions of their code, and deploy their applications.
On January 12, 2024, GitLab released urgent security updates to fix two critical vulnerabilities. These flaws, rated at a score of 9.6 and 10 on the CVSS scale, affect all versions of GitLab, since version 16.1.0.
- The first flaw, CVE-2023-7028, allows an attacker to send password reset emails to unverified email addresses. This allows the attacker to take control of an account, even if two-factor authentication is enabled.
- The second flaw, CVE-2023-7029, allows an attacker to bypass two-factor authentication by impersonating a user. This allows the attacker to access an account without needing to know the password or two-factor authentication code.
GitLab recommends that all users update their installations to versions 16.5.6, 16.6.4, or 16.7.2 as soon as possible. Users of earlier versions should also update their installations to versions 16.1.6, 16.2.9, 16.3.7, or 16.4.5.
BitLocker
The Security Feature Bypass Vulnerability in BitLocker is a critical vulnerability that was discovered in January 2024.
This vulnerability, named CVE-2024-20666, allows an attacker with physical access to a device encrypted with BitLocker to bypass encryption and access data.
The vulnerability exploits a flaw in the way BitLocker handles recovery keys. Recovery keys are 48-character codes that can be used to unlock a BitLocker device if the master key is lost or misplaced.
The attacker can exploit this vulnerability by using a debugging tool to access device memory. The tool can then be used to read recovery keys from memory.
Microsoft released a fix for this vulnerability as part of the January 2024 security update. BitLocker users are advised to install this fix as soon as possible.
CAN 2024
The CAN 2024, or African Cup of Nations, is a football competition bringing together 24 teams from Africa.
The CAN 2024 ticketing website was the victim of a computer security breach. This flaw allowed hackers to massively purchase tickets at a ridiculous price, i.e. 1 euro cent.
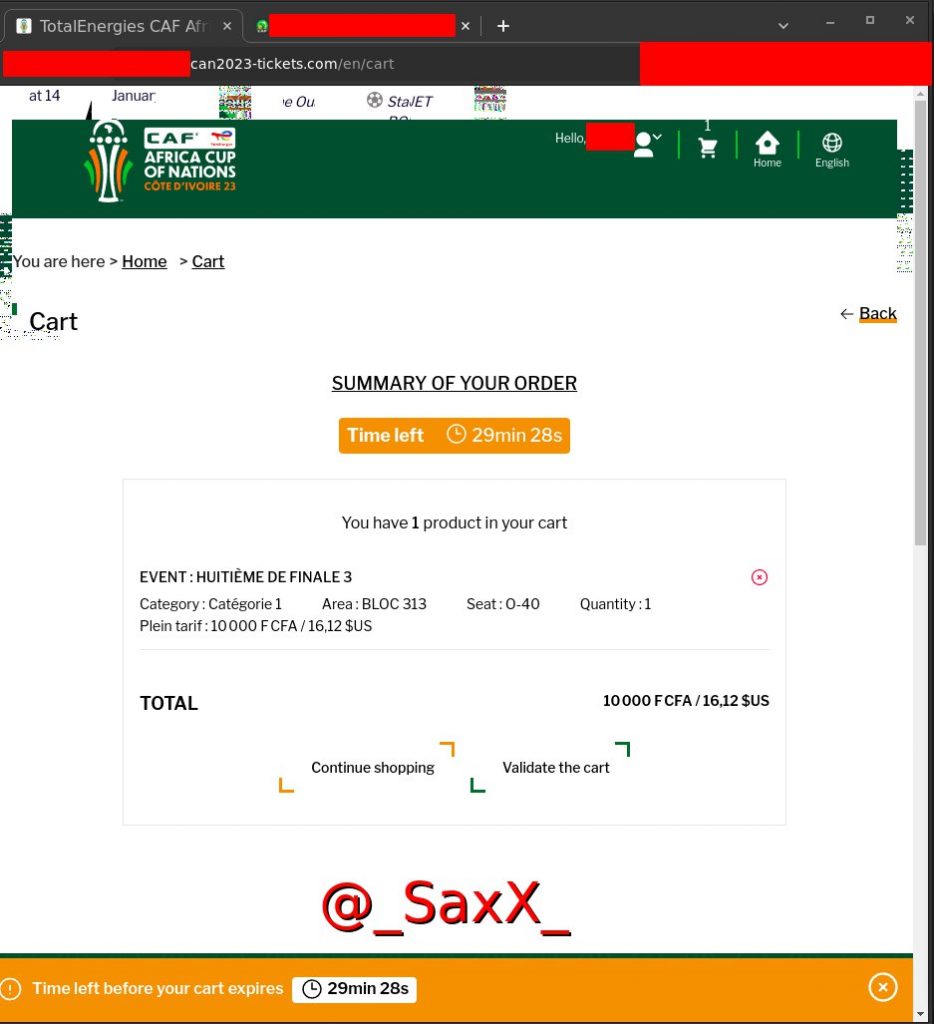
According to cybersecurity experts, the breach was caused by a vulnerability in the ticket management system. This vulnerability allowed hackers to change ticket prices as they wished. Thousands of tickets were sold at very low prices.
SNATCH vs USA
On January 23, 2024, the hacker known as Snatch released a series of sensitive data on leaders of the CIA, Secret Service and the US government.
The data includes:
- Names.
- Email addresses.
- Telephone numbers.
- IP addresses.
- Information on secret communications.
Snatch said he obtained the data by hacking into the computer systems of the CIA and Secret Service. He threatened to release more data if he didn’t get a $100 million ransom.
The US government condemned the attack and said it was working to investigate the incident and identify those responsible.
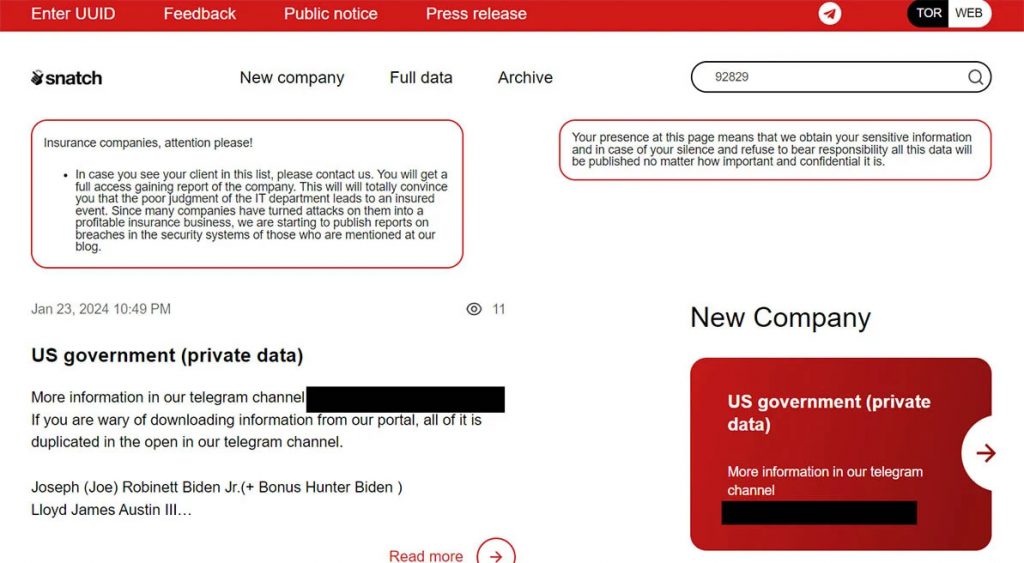
The data disclosed
The data disclosed by Snatch includes information on the following:
- CIA leaders: CIA Director William Burns and several of his deputies.
- Secret Service Leaders: Secret Service Director James Murray and several of his deputies.
- Important members of the US government: President Joe Biden, Vice President Kamala Harris and several cabinet members.
The data also includes information about secret communications between these people. This information could be used by adversaries to spy on the United States or to harm U.S. interests.
