CyberNews November 2023
Discover the CyberNews of November 2023. This is the recap of news on Cybersecurity during the month of November 2023.
Discover the CyberNews of November 2023. This is the recap of news on Cybersecurity during the month of November 2023.
48 countries commit to no longer paying ransoms
48 countries, including the United States, the United Kingdom, Canada, Australia and France, have announced that they are committed to no longer paying ransoms to hackers.
The goal of this commitment is to break the business model of ransomware cyberattacks, which relies on victims paying ransoms.
The commitment of the 48 countries is a strong signal to hackers. It shows that governments are determined to combat ransomware cyberattacks and that victims will no longer be rewarded for paying ransoms.
The commitment includes a series of measures that will be taken by signatory countries to combat ransomware cyberattacks. These measures include:
- Strengthening cybersecurity laws and regulations.
- Increased international cooperation between governments and businesses.
- Public awareness of the risks of cyberattacks.
The signatory countries hope that these measures will help reduce the number of ransomware cyberattacks and protect victims.
The TOP 10 most used passwords
According to Nordpass, here are the top 10 most used passwords in the world.
| Ranking | Password | Time needed to decipher it | Countdown |
| 1 | 123456 | < 1 second | 4 524 867 |
| 2 | admin | < 1 second | 4 008 850 |
| 3 | 12345678 | < 1 second | 1 371 152 |
| 4 | 123456789 | < 1 second | 1 213 047 |
| 5 | 1234 | < 1 second | 969 811 |
| 6 | 12345 | < 1 second | 728 414 |
| 7 | password | < 1 second | 710 321 |
| 8 | 123 | < 1 second | 528 006 |
| 9 | Aa123456 | < 1 second | 319 725 |
| 10 | 1234567890 | < 1 second | 302 709 |
Australia’s ports paralyzed by ransomware
On November 11, 2023, a cyber incident affected Australian ports, disrupting operations at several major ports, including the ports of Sydney, Melbourne and Brisbane.
The incident was caused by a ransomware attack, which crippled the ports’ IT systems. The hackers demanded a $20 million ransom in exchange for restoring the data, the ports refused to pay the ransom.
Ports were forced to temporarily close operations, leading to significant supply chain disruptions. Ships were blocked in ports and goods were delayed.
The Australian government said the attack was an act of cyberwarfare and condemned the hackers. The government also announced it would provide assistance to ports to help them recover from the attack.
Poloniex: $125 million in cryptocurrencies stolen
On November 10, 2023, cryptocurrency exchange Poloniex confirmed that it had been hacked. The hackers managed to steal cryptocurrencies worth an estimated $125 million.
According to Poloniex, the hackers exploited a flaw in the exchange’s security system to access the company’s hot wallets. Hot wallets are wallets that contain cryptocurrencies that are accessible online.
Hackers managed to steal ETH, BTC and TRX. Poloniex said it was working with authorities to investigate the attack.
China’s largest bank hit by ransomware
On November 22, 2023, China’s largest bank, Industrial and Commercial Bank of China (ICBC), fell victim to a ransomware attack. The attack crippled the bank’s IT systems, disrupting its operations and services.
The attack was claimed by a group of hackers calling themselves “LockBit”. The group demanded a $200 million ransom in exchange for restoring the bank’s data.
ICBC said it had not paid the ransom and was in the process of restoring its computer systems. The bank also said it had taken steps to strengthen its cyber defenses.
BLUFFS: a serious threat to the security of Bluetooth devices
In November 2023, researchers from the computer security research institute Eurecom published a report on a series of vulnerabilities in the Bluetooth standard. These vulnerabilities, called BLUFFS, could allow attackers to compromise billions of Bluetooth devices.
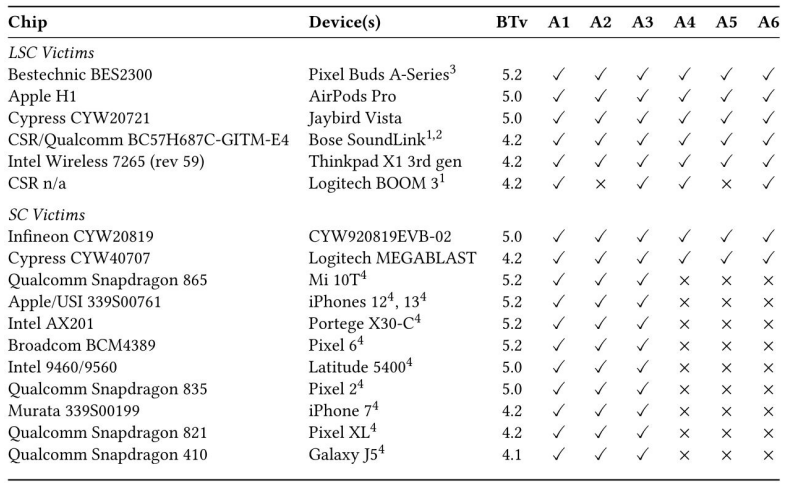
Grouped under the identifier CVE-2023-24023, these vulnerabilities affect all versions of Bluetooth from 4.2 to 5.4.
BLUFFS vulnerabilities exploit two flaws in the Bluetooth protocol:
1st flaw
The first flaw allows an attacker to generate compromised Bluetooth session keys.
These keys are used to encrypt communications between two Bluetooth devices. If an attacker manages to generate a compromised session key, they can intercept and decrypt communications between these two devices.
2nd flaw
The second flaw allows an attacker to send unauthorized commands to a Bluetooth device. These commands can be used to take control of the device or to steal data.
Eurecom researchers demonstrated that they could exploit BLUFFS vulnerabilities to compromise a variety of Bluetooth devices, including smartphones, laptops, smartwatches, and connected vehicles.
Computer vulnerability in the Kivu Security Barometer System of the Democratic Republic of Congo
On November 9, 2023, the partner organizations in charge of the Kivu Security Barometer (KST) project were informed of a security breach in its database.
This flaw allowed an attacker to compromise the database and access sensitive data, including information on incidents of violence in the eastern Democratic Republic of Congo.
The flaw was discovered by the computer security research group at Ghent University, Belgium. The group said the flaw was caused by a configuration error in the database.
KST partner organizations immediately took steps to fix the flaw and secure the database. They also launched an investigation to determine whether the flaw had been exploited by hackers.
The flaw could have had serious consequences if it had been exploited by hackers. The hackers could have accessed sensitive data, including information on incidents of violence in the eastern Democratic Republic of Congo.
This information could have been used to target individuals or groups, or to sow confusion and fear.
The French National Assembly victim of a cyberattack
On November 18, 2023, a group of hackers calling themselves “KromSec” claimed responsibility for a cyberattack against the French National Assembly.
The hackers said they managed to access sensitive data, including personal information about MPs and staff members, as well as information about parliamentary proceedings.
The National Assembly confirmed the attack, saying it was detected on November 17 and immediately responded to by security services.
The National Assembly also said that sensitive data had been protected and that there was no sign that hackers had succeeded in stealing it.
A security flaw in Google Calendar
A security flaw in Google Calendar was discovered in November 2023. This flaw allowed an attacker to take control of a computer remotely by inserting secret commands into the description of a calendar event.
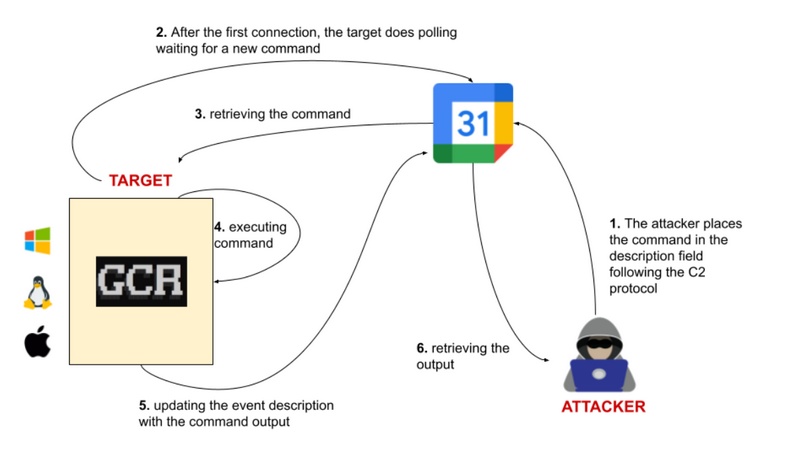
To exploit this flaw, the attacker first had to obtain the victim’s email address and permission to create an event in their calendar. Once the event was created, the attacker could insert secret commands into the event description. When the victim opened the event, the commands were executed by the victim’s web browser.
The commands could be used to install malware, steal data, or take control of the computer.
Google fixed this flaw on November 15, 2023. Google Calendar users are advised to update their apps and web browsers to benefit from this fix.
General Electric opens investigation into security breach involving military data
On November 29, 2023, General Electric (GE) confirmed the opening of an investigation into a security breach that allowed a hacker to take control of a GE Aviation development network.
The hacker then gained access to sensitive data, including information relating to military projects.
GE said the flaw was caused by a configuration error in the development network. The company also said it had taken steps to fix the flaw and secure the network.
The hacker, who calls himself IntelBroker, claimed to have obtained sensitive data on US military projects, including information on fighter jet engines and drones.
IntelBroker also claimed to have obtained information on European military projects, including information on missiles and air defense systems.
GE said it was working with U.S. authorities to investigate the attack. The company also said it would take steps to strengthen the security of its networks.
Agreement in principle on the Cyber Resilience Act
On 23 November 2023, the Council of the European Union and the European Parliament reached a political agreement on the Cyber Resilience Act (CRA). The CRA is new legislation that aims to strengthen the cybersecurity of digital products in the European Union.
The agreement in principle provides that the CRA will apply to all digital products presenting a direct or indirect connection to a machine or a network. Affected products include computers, smartphones, tablets, connected devices, operating systems and software.
The CRA is expected to come into force in 2024.
$588,000 in BTC stolen from fake Ledger Live app
On November 5, 2023, a Twitter analyst, ZachXBT, discovered a fake Ledger Live app on the Microsoft Store. This app, which was called “Ledger Live Web3”, was designed to look like the official Ledger Live app.
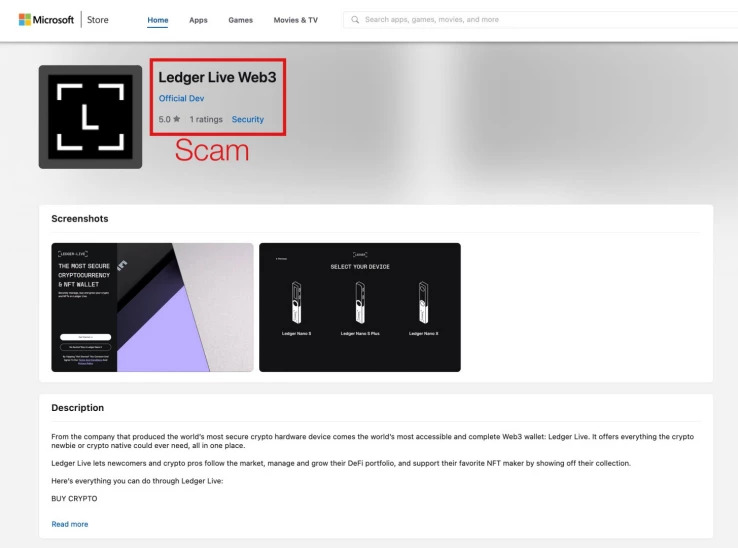
Users who downloaded the app were asked to provide their Ledger login information. This information was then used by the hackers to access users’ cryptocurrency wallets and steal bitcoins.
In total, the hackers managed to steal $588,000 in bitcoins. The victims of the attack were Ledger Live users from around the world.
Ledger, the maker of the Ledger Live app, quickly responded by removing the fraudulent app from the Microsoft Store. The company also posted a warning on its website to inform users of the threat.
Microsoft fixes 5 zero-day vulnerabilities
As part of its Patch Tuesday on November 2, 2023, Microsoft released fixes for 5 zero-day flaws, i.e. security flaws unknown to the public and software publishers. These flaws have been exploited by hackers in real-world attacks.
Here are the 5 zero-day vulnerabilities:
- CVE-2023-36036 – Windows – Pilote “Cloud Files Mini Filter”
- CVE-2023-36033 – Windows – Librairie “DWM Core”
- CVE-2023-36025 – Windows – Bypass de la fonction SmartScreen
- CVE-2023-36413 – Microsoft Office
- CVE-2023-36038 – ASP.NET Core
SysAid zero-day exploit exploited in Clop ransomware attacks
A zero-day flaw in IT service management (ITSM) software SysAid was exploited by hackers to deploy Clop ransomware.
The flaw, which has been named CVE-2023-47246, allows an attacker to execute malicious code on a SysAid server.
Hackers used the flaw to upload a webshell to the SysAid server. A webshell is a program that allows an attacker to control a server remotely.
With the webshell in place, hackers were able to run PowerShell scripts to load multiple malware strains and various tools, including GraceWire and Cobalt Strike.
GraceWire is a remote access tool that allows hackers to take control of a computer. Cobalt Strike is an exploit kit that allows hackers to exploit security vulnerabilities on a computer.
The hackers then used these tools to deploy Clop ransomware on infected systems.
SysAid released a patch for the flaw on November 2, 2023. SysAid users are advised to install the patch as soon as possible.
A critical flaw fixed in Google Agenda
On November 29, 2023, Google released a new security update for Chrome that fixes a critical security flaw.
This flaw, which has been named CVE-2023-22007, allows an attacker to take control of a computer by executing malicious code.
The flaw is due to a serialization error in Chrome’s V8 JavaScript engine. This error allows an attacker to create malicious web content that can be used to exploit the flaw.
Google recommends Chrome users to download and install the update as soon as possible.
Security vulnerability discovered in Synology routers
In November 2023, Synology issued a security advisory to address a critical vulnerability in its Synology Router Manager (SRM) software. The vulnerability, CVE-2023-11966, allows a remote attacker to execute malicious code on the router.
The vulnerability is due to a configuration error in the SRM software. This error allows an attacker to send special requests to the router that can be used to exploit the flaw.
Synology released a patch for the flaw on November 20, 2023. Synology router users are advised to install the patch as soon as possible.
Boeing data released following Lockbit cyberattack
On November 10, 2023, the Lockbit ransomware group released a 43 GB archive of data stolen from Boeing. The data included information about Boeing employees, customers, projects and products.
Among the data released were:
- Personal information about employees, including names, email addresses, phone numbers and dates of birth.
- Customer information, including names, addresses, telephone numbers and financial information.
- Information about Boeing projects, including plans, specifications and technical data.
- Information about Boeing products, including manuals, repair guides and safety data.
Boeing confirmed the attack and said it was working to restore the stolen data. The company also said it had taken steps to strengthen its cyber defenses.
Win up to €20,000 if you manage to hack FranceConnect
The French Interministerial Digital Directorate (Dinum) has launched a bug bounty program aimed at finding and correcting security vulnerabilities on the FranceConnect platform.
The program offers rewards of up to €20,000 for people who manage to find critical flaws.
FranceConnect is an electronic identification and authentication platform that allows French citizens to access many public services online. It is used by more than 20 million people.
The Dinum bug bounty program is open to people of all ages and backgrounds. Participants simply need to register on the program’s website and submit their vulnerability reports.
Vulnerabilities are assessed by IT security experts. Critical flaws are those that can be exploited by hackers to take control of a FranceConnect account or to access sensitive data.
Participants are rewarded based on the severity of the vulnerability they found. Critical flaws are rewarded up to €20,000.
