CyberNews October 2023
Discover our Cybernews October 2023 infographic. This is the recap of news on Cybersecurity during the month of October 2023.
Discover our Cybernews October 2023 infographic. This is the recap of news on Cybersecurity during the month of October 2023.
A CVE of severity 10 affects Atlassian Confluence
CVE-2023-22515 with severity 10 affects and is exploited by hackers on version 8.0.0 and above of Confluence instances.
CISA (the equivalent of Anssi in the United States), the FBI and MS-ISAC have warned of active exploitation of this breach causing an elevation of privileges without interaction on the part of the user.
Atlassian strongly recommends users migrate to secure versions.
Customers unable to migrate have been asked to shut down the affected instances and isolate them from the internet.
It is also recommended that administrators look for indicators of compromise, such as new or suspicious administrator accounts.
Urgent update for WinRAR
The popular file compression and extraction software, WinRAR, has once again been compromised by a problematic security flaw.
WinRAR strongly recommends updating its software, correcting the problem.
Google threat researchers discovered this vulnerability. It is linked to the management of temporary files by WinRAR.
When WinRAR decompresses a file, it creates a temporary file that contains the contents of the compressed file. This temporary file is then deleted, but it is possible for an attacker to modify it before it is deleted.
The latter can insert malicious code there. When the victim unzips the file, the code can be executed on their computer.
A Zero Day flaw exploited in Roundcube
Security researchers from Eset discovered a vulnerability on October 12 in the open source Roundcube messaging service.
These researchers indicate that the Winter Vivern cybercriminal group carries out cyberattacks via the exploitation of the zero day flaw.
“The group recently began exploiting a zero-day XSS vulnerability in the Roundcube webmail server. In an XSS attack, malicious scripts are injected into otherwise trustworthy websites,” Eset explained.
Webmail reacted very quickly by providing an update 2 days after the discovery, i.e. October 14.
The exploit of this XSS flaw identified as CVE-2023-5631 can be performed remotely by sending a corrupted email.
“At first glance, the email does not appear malicious, but upon reviewing the HTML source code, we were able to see a tag for SVG graphics at the end that contains a malicious payload in the code,” explained Mathieu Faou, security researcher at Eset who discovered this flaw.
“By sending a specific email, attackers are able to load arbitrary JavaScript code in the context of the Roundcube user’s browser window. No manual interaction other than displaying the message in a web browser is required. The final JavaScript payload can exfiltrate email messages to the group’s command and control server.”.
The “Looney Tunables” flaw on Linux
Researchers at Qualys have discovered a flaw allowing a cybercriminal to have administrative rights on the victim’s system as root user.
This vulnerability, named CVE-2023-4911, also known as “Looney Tunables,” uses the GNU C language standard library (glibc). Its CVSS score is 7.8, classifying it as a significant flaw.
The exploitation of this attack is done via a buffer overflow in the dynamic link ld.so, which in Linux is responsible for “finding and loading the shared libraries necessary for a program then preparing and executing said program”.
To obtain administrator rights, the hacker uses the GLIBC_TUNABLES environment variable to trigger the “buffer overflow”.
Cisco IOS XE software affected by exploited zero-day flaw
Listed as CVE-2023-20198, this vulnerability “gives an unauthenticated, remote attacker the ability to create an account on an affected system with privilege level 15 access. The attacker can then use this account to take control of the affected system,” explained CISCO.
This flaw can only be exploited if the Web UI function of the IOS XE software is activated.
To verify whether a cybercriminal is exploiting the flaw, several indicators of compromise must be checked, starting in system logs, especially if a file name does not match an expected file installation action.
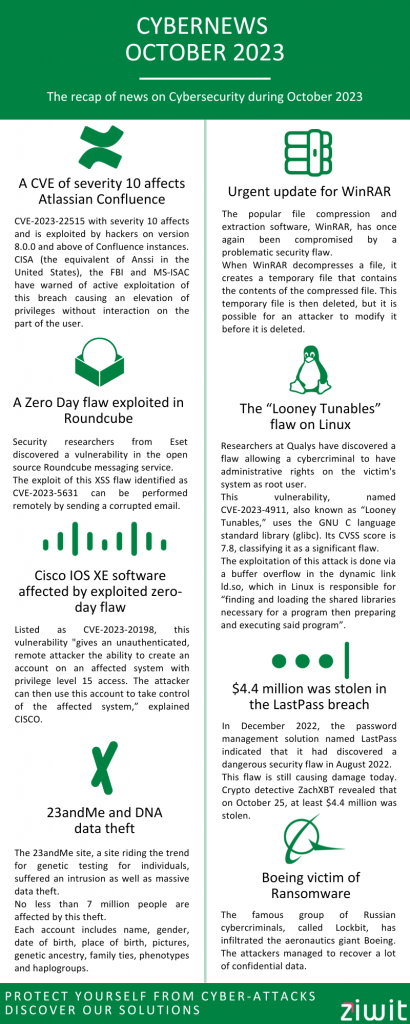
On October 25, $4.4 million was stolen in the LastPass breach
In December 2022, the password management solution named LastPass indicated that it had discovered a dangerous security flaw in August 2022.
In fact, this vulnerability allowed a cybercriminal to steal a backup of encrypted data from customers’ vaults.
This flaw is still causing damage today. Crypto detective ZachXBT revealed that on October 25, at least $4.4 million was stolen.
“On October 25, 2023 alone, more than 25 victims lost $4.4 million following the LastPass hack. »
Since January and in total, more than 150 people have been impacted by this security breach. The total amount of damage amounts to at least $35 million.
Boeing victim of Ransomware
The famous group of Russian cybercriminals, called Lockbit, has infiltrated the aeronautics giant Boeing.
The attackers managed to recover a lot of confidential data.
The media outlet The Register indicates that this data leak could have severe consequences for the company, which works in particular with the US Air Force and builds two 747-8 planes dedicated to the next American presidential transport.
DNA data theft
The 23andMe site, a site riding the trend for genetic testing for individuals, suffered an intrusion as well as massive data theft.
No less than 7 million people are affected by this theft.
The data was found on the Dark Web, on a hacker forum. The account is sold between 1 and 10 dollars.
Each account includes the following information:
- Name
- Gender
- Date of birth
- Place of birth
- Pictures
- Genetic ancestry
- Family ties
- Phenotypes: observable physical traits such as skin color
- Haplogroups: groups of genetic lineages having a common ancestor
The lack of vigilance of certain users led to this massive leak.
The attackers accessed 23andMe accounts using credentials previously stolen in other leaks.
Subsequently, the hackers used the DNA Relatives technique to find genetic parents. The data was then extracted using automated programs.
Okta’s intrusion
Last Friday, October 20, the company Okta, which manages identities and access, reported an exploited security vulnerability.
Thanks to the customer support management system, cybercriminals gained access to the confidential information of the company’s customers.
Okta’s head of IT security, David Bradbury, announced that the hackers were able to retrieve support HTTP archive (HAR) files, files downloaded by customers.
David Bradbury said: “HAR files can also contain sensitive data, including cookies and session tokens, which malicious actors can use to impersonate valid users.”
Following this disclosure, Okta revoked built-in session tokens and advised customers to sanitize credentials contained in HAR files before sharing them.
CHUs and EHPADs targeted
Health Structures are often the target of cybercriminals, especially in France, as demonstrated in our article dedicated to the subject here.
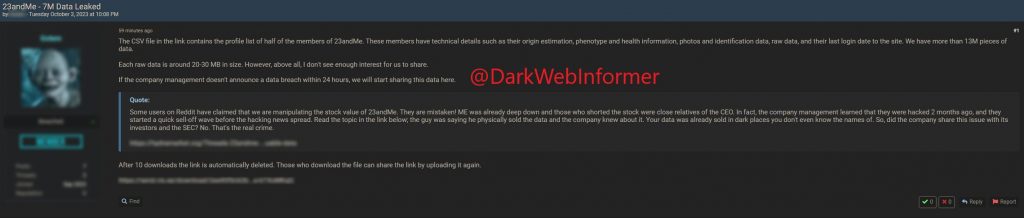
A ransom demand against a Norman EHPAD
The MEDUSA cybercriminal group claimed responsibility for an intrusion into the Marigny-le-Lozon nursing home in Normandy.
MEDUSA has collected a lot of information including:
- Identity cards for residents of the EHPAD
- Internal letters
- Schedules
- The specificities of each resident
This is therefore a major and important leak for this health establishment.
The group demanded a ransom of no less than $100,000, approximately €93,000, in exchange for the information.
The Western Vosges Hospital Center, victim of a cyberattack
On Saturday October 7, 2023, CHOV, Hospital Center of the West Vosges, bringing together the hospitals of Neufchâteau and Vittel, was the victim of a computer intrusion.
On its Facebook account, the CH specifies that “Emergencies are normally received on the Neufchâteau site. Scheduled activities, consultations, surgical interventions are suspended until Tuesday October 10 inclusive. Chemotherapy will be provided. Patients whose hospitalization was scheduled, such as consultants, will be called by the hospital. “.

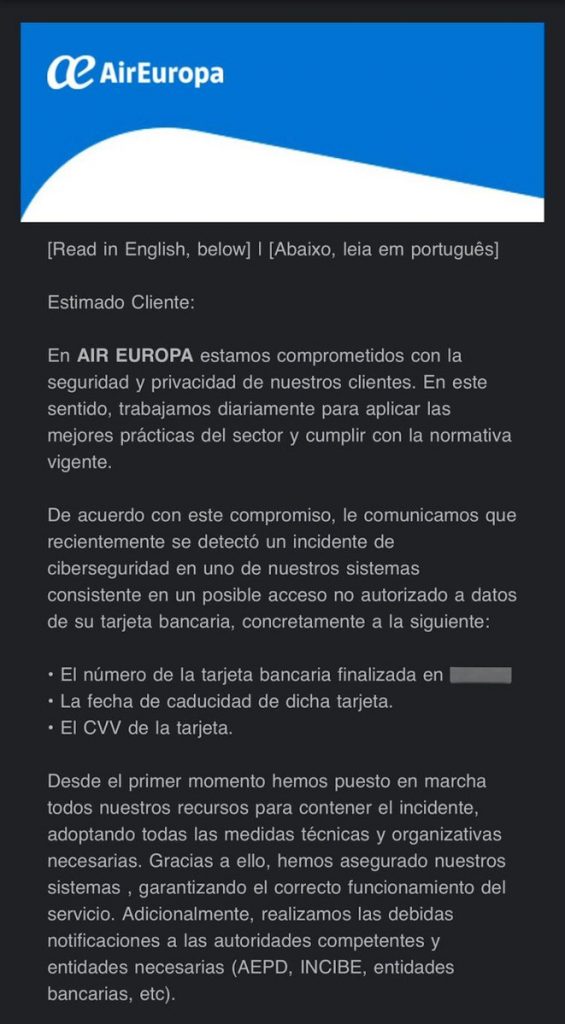
Theft of banking data for the airline Air Europa
The Spanish airline, called Air Europa suffered a computer intrusion.
The incident resulted in data theft for a number of customers (number not mentioned).
The airline clarified that only banking data was stolen, and not personal or confidential data.
“Red Alert Israel” app hacked by pro-Palestinian hacktivists
On October 9, a cybersecurity company revealed the hacking of an application intended to report and warn Israelis of attacks such as rocket attacks.
It was the pro-Palestinian hacktivist group, named AnonGhost, which orchestrated this attack on the “Red Alert Israel” application.
AnonGhost exploited a security flaw in the application, allowing it to intercept requests and send false information.
Hackers triggered an alert via the app on October 8, 2023 for an imminent nuclear attack on Israel, with the aim of panicking the population.
“Red Alert: Israel” was immediately removed from the stores.
According to Cloudfare, on October 12, 2023, a fraudulent website impersonated a similar application, “Red Alert: Rocket Alerts”.
The site offered visitors to download the “Red Alert: Rocket Alerts” application on Android, which obviously led to a malicious version of the application.
The latter made it possible to steal data from the impacted phone.
