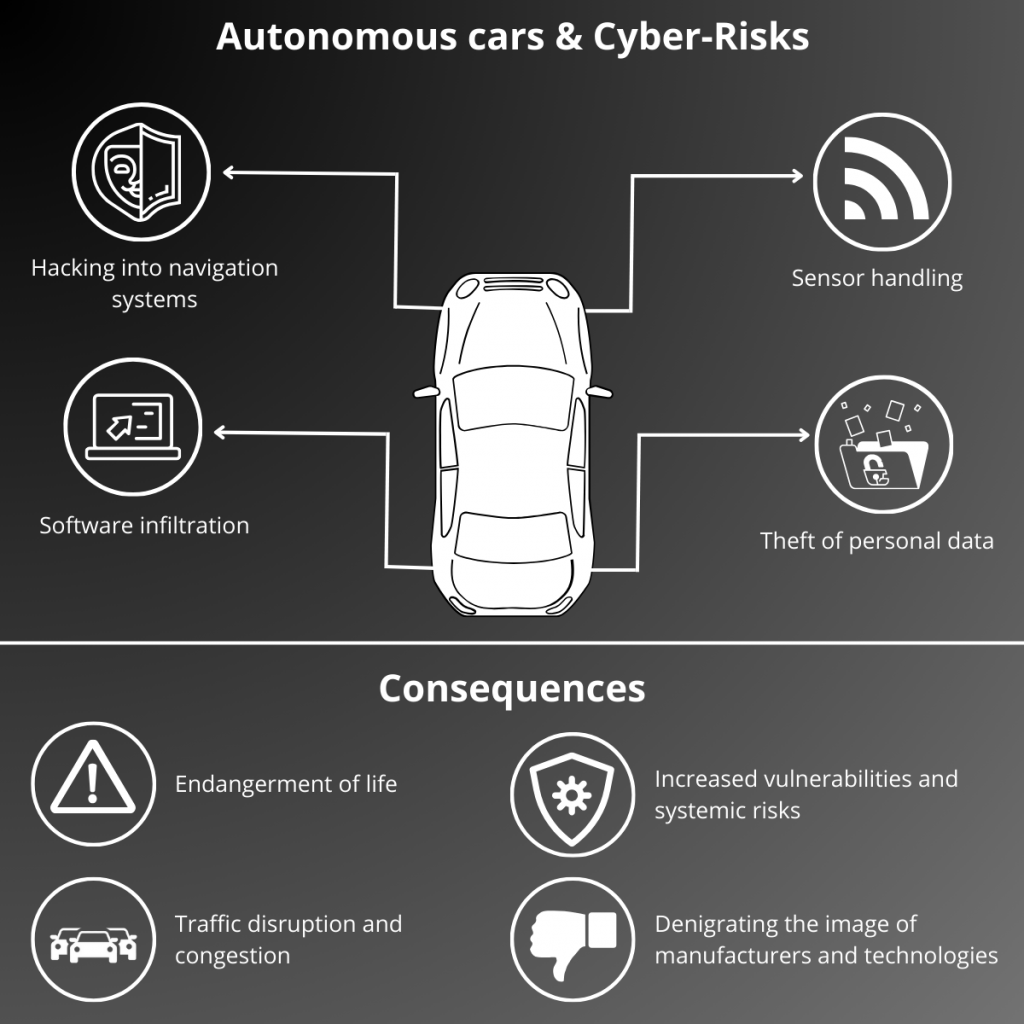
Autonomous Cars & Cyber Risks
The advent of autonomous cars, transforming the way we travel, brings with it a new reality: automotive cybercrime.
The advent of autonomous cars, which promise to transform the way we get around, is accompanied by a new reality: automobile cybercrime.
These vehicles, equipped with sophisticated artificial intelligence and permanently connected to the internet, become prime targets for hackers. The security and liability of these technologies then become central issues.
The different Cyber Risks
Hacking navigation systems
GPS spoofing
A hacker may be able to spoof GPS signals received by a self-driving car. It could mislead about the car’s true position, leading it to the wrong or dangerous destination.
Replay attacks
A hacker can intercept and rebroadcast pre-recorded GPS signals, forcing a car to follow an unwanted predefined route.
Handling sensors
Data falsification
A hacker can inject false information into your self-driving car’s sensors, disrupting its perception of the environment.
It could simulate the presence of non-existent obstacles, such as a wall or another vehicle, causing unwanted emergency braking.
It could also remove important signals, such as a red light or a pedestrian crossing the road, leading to a dangerous situation.
Deepfake attacks
Realistic images or videos can be used to fool the car’s sensors, leading it to misinterpret the environment.
Software infiltration
Malware and viruses
Malware can infect the system of a self-driving car, disrupting its operation and causing critical malfunctions.
For example, a virus that attacks a car’s braking system, rendering it inoperable. This could put the driver’s life and the lives of others in danger in an emergency situation.
Compromised software updates
Hackers can release fake software updates containing malware, taking control of a car.
Imagine a software update that appears to come from the car manufacturer, but is actually corrupted. Once installed, it could allow hackers to lock doors, disable brakes, or even take complete control of the steering, endangering your life and that of other road users.

DDoS attacks: Denial of Service
Saturation of the communication system
A hacker can overwhelm your self-driving car with fake messages, preventing it from receiving vital driving information.
Disabling critical features
Attacks can target specific systems in a car, such as automatic emergency braking or power steering, rendering them inoperable.
Theft of personal data
Collection and storage of sensitive data
Self-driving cars collect a large amount of data about passengers, their journeys and the environment, attracting hackers looking for sensitive information.
This data may include personal information such as:
- Nouns.
- Addresses.
- Telephone numbers.
- Driving habits.
- Private conversations captured inside the vehicle.
Cyber espionage and profiling
The stolen data can be used to spy on users, track them without their knowledge, or serve them targeted advertisements. Driver profiling can also be used to manipulate or discriminate against them based on their driving habits or location.
These typologies of cyber risks highlight the need to develop robust security measures to protect self-driving cars and their users.
Potential consequences of cyber risks from autonomous vehicles
Cyber risks related to autonomous vehicles can have serious and varied consequences, impacting not only passengers and other road users, but also the automotive industry and society as a whole.
Endangering life
Serious accidents, injuries and deaths
Hacking an autonomous vehicle can cause serious accidents, injuring or killing passengers, drivers of other vehicles, and pedestrians.
Vehicle hijackings and thefts
Hackers can hijack autonomous vehicles to use them for illegal purposes, such as transporting drugs or weapons, or to carry out attacks.
The theft of autonomous vehicles could also become a major problem, with significant economic and security implications.
Traffic disruptions and traffic jams
Coordinated attacks on transportation infrastructure and communications systems could cause massive traffic jams and paralyze traffic in cities.
Traffic disruptions and congestion caused by cyberattacks can have a significant economic impact, reducing productivity, increasing transportation costs and disrupting the supply chain.
Additionally, the social impact can be significant, limiting people’s freedom of movement and creating a feeling of insecurity.
Denigration of the image of automobile manufacturers and autonomous technologies
Loss of consumer confidence
If cyber risks are not addressed, consumers could lose confidence in autonomous vehicles and slow adoption of this technology.
Imagine a series of serious accidents caused by self-driving car hacks. Public trust in this technology and/or brand linked to these cyber-attacks would then be seriously compromised.
Barrier to innovation and development
Fear of cyberattacks could curb investment in autonomous technologies and slow the development of this promising industry.
Automakers may be reluctant to invest in technologies that are not perceived as safe by the public.
Increased vulnerabilities and systemic risks
Autonomous vehicles are increasingly connected to each other and to road infrastructure, creating an interdependence that can be exploited by hackers.
Additionally, the cyber nature of autonomous vehicles makes them vulnerable to large-scale attacks, which could affect large numbers of vehicles simultaneously.
Examples of cyber incidents on self-driving cars
Remote hacking of a Jeep Cherokee
In July 2015, Miller and Valasek demonstrated the ability to remotely hack a 2014 Jeep Cherokee via the Internet.
They exploited software vulnerabilities in the car’s Uconnect infotainment system to take control of several critical functions, including:
- The air conditioning system : They were able to change the temperature and ventilation inside the car.
- The audio system : They were able to change the radio station and broadcast music as they wished.
- Braking : They were able to slow down and even stop the car remotely.
The stages of hacking
- Fiat Chrysler Automobiles (FCA) Internal Network Infiltration: Researchers first hacked into FCA’s internal network to obtain sensitive information about the vehicles’ computer systems.
- Exploitation of a vulnerability in the Uconnect system: They then exploited a software vulnerability in the Uconnect system to infiltrate the Jeep’s internal network.
- Taking control of critical functions: Once connected to the internal network, they were able to take control of several critical functions of the car via CAN (Controller Area Network) messages.

Hacking of Tesla’s navigation systems
In June 2019, experts from Regulus Cyber managed to hack the GPS navigation system of a Tesla Model 3, demonstrating the vulnerability of these technologies.
The hack in question allowed researchers to:
- Hijack the car’s navigation system: By sending false GPS signals, they were able to force the car to head to a different destination than the one chosen by the driver.
- Track vehicle location in real time: This capability raises concerns about driver privacy and safety.
- Change vehicle route as they wish: Imagine the malicious implications of this capability, such as redirecting a vehicle into a dangerous area.
- Disable Autopilot: While this can be seen as a security measure to counter a hack in progress, it also highlights the growing reliance on automated systems and the potential risks associated with their failure.
Hacking of Tesla’s Autopilot system
In late 2023 (CyberNews December 2023), three German researchers published an article in the German newspaper Der Spiegel detailing how they managed to hack Tesla’s Autopilot driver assistance system. The researchers said they were able to access the system using a “voltage glitch” tool, which involves applying a large voltage variation to a processor for a short period of time. This failure causes a vulnerability allowing entry into the protected system and thus access to its innards.
Researchers were able to confirm the existence of an unbridled Autopilot mode, called “Executive Mode”, which allows Tesla vehicles to exceed the speed and range limits imposed by the standard mode. Unbridled mode is reserved for Elon Musk and his guests, and it is not available to ordinary Tesla owners.
The researchers said they discovered jailbreak mode by examining data retrieved from the Autopilot system. They found references to the mode in the system’s source code, as well as instructions on how to enable it.
The researchers’ discovery raises questions about the security of the Autopilot system. If an attacker can gain access to the system, they could potentially activate jailbreak mode on a regular Tesla vehicle, which could lead to security risks.

Fighting the cyber risks of self-driving cars
Standards and Regulations
Establishing mandatory cybersecurity standards for automakers
- Definition of minimum safety requirements for autonomous vehicles in terms of design, development and production.
- Inclusion of mandatory cybersecurity tests in vehicle certification processes.
- Harmonization of international standards to ensure vehicle safety globally.
Certification of embedded software and computer systems
- Implementation of certification programs for critical software and systems for autonomous vehicles.
- Assessment of the safety and reliability of components by independent organizations.
- Assignment of safety labels to certified products to inform consumers.
International cooperation between governments and automotive industry players
- Sharing information and best practices in automotive cybersecurity.
- Establishment of international collaborations for the research and development of innovative security solutions.
- Coordination of efforts to combat transnational cyber threats.
Liability and sanctions of manufacturers in the event of piracy
- Implementation of laws and regulations that define the liability of manufacturers in the event of a cyber attack.
- Application of dissuasive sanctions in the event of failure to comply with security obligations.
- Encourage manufacturers to invest in cybersecurity to minimize risks.
User awareness and education
Driver training on risks and good practices
- Provision of training and information materials on cyber risks linked to autonomous vehicles.
- Organization of awareness sessions for drivers and automotive professionals.
- Integration of cybersecurity training modules into road education programs.
Dissemination of clear and publicly accessible information
- Transparent communication from manufacturers on the safety measures implemented.
- Publication of regular reports and analyzes on cyber risks and security incidents.
- Use of communication channels accessible and understandable by the general public.
Promotion of a collective cybersecurity culture
- Encouraging users to report suspicious activities to manufacturers and authorities.
- Creation of an active community of researchers and experts in automotive cybersecurity.
- Organization of awareness campaigns to promote good digital security practices.
Strengthening security
Data encryption and secure communication protocols
- Implementation of robust encryption technologies to protect sensitive data transmitted between vehicles, infrastructure and servers.
- Use of secure communication protocols such as HTTPS and TLS to guarantee the confidentiality and integrity of exchanges.
- Adoption of international security standards like ISO/IEC 27001 and NIST.
Strong authentication and access control to IT systems
- Implementation of multi-factor authentication for users and devices that access critical systems.
- Use of biometric solutions such as facial recognition or fingerprint to strengthen access security.
- Application of the principle of least privilege to limit access rights to systems and data based on the needs of each user.
Regular updating of software and operating systems
- Rapid deployment of security patches for known vulnerabilities.
- Regular updating of software and operating systems to maintain an optimal level of security.
- Automation of update processes to ensure rapid and efficient patch deployment.
Séparation of on-board networks
- Setting up separate virtual networks for the different vehicle components (driving systems, infotainment, communication, etc.).
- Isolation of critical systems to limit the impact of an attack on a single network.
- Use of firewalls and network segmentation technologies to enhance security.
Development of defensive artificial intelligence
- Integration of machine learning algorithms to detect anomalies and suspicious behavior.
- Using AI to analyze real-time data and identify potential threats.
- Implementation of automatic incident response systems to limit the damage caused by an attack.
Penetration tests and IT security audits
- Regular performance of penetration tests (or Pentest) by cybersecurity experts to identify system vulnerabilities.
- Conducting IT security audits to assess compliance with security standards and best practices.
- Correction of identified vulnerabilities as a priority to minimize exploitation risks.
- Correction of identified vulnerabilities as a priority to minimize exploitation risks.