The evolution of the quantum computer
In a world in constant digital evolution, where the rules of the game change daily, computers are gaining in power and importance, opening up new technological horizons.
In a world in constant digital evolution, where the rules of the game change daily, computers are gaining in power and importance, opening up new technological horizons. Quantum computing, in particular, is evolving because of its super-power, enabling it to solve extremely complex problems much faster than conventional computers.
What is a quantum computer?
Quantum computing complements classical computing, but its calculations are based on the laws of quantum physics, using “qubits” that can be both 0 and 1, thanks to quantum superposition.
In fact, a quantum computer is able to explore all paths at the same time, enabling it to perform calculations much faster than a classical computer.
A quantum computer operates according to the following quantum principles:
- Superposition, qubits can be in several states at the same time.
- Entanglement, when two qubits are strongly linked or correlated, knowing one gives immediate knowledge of the other, no matter how far apart they are.
- Decoherence is the loss of a quantum qubit due to environmental factors.
The differences between a quantum computer and a classical computer
| Classic computer | Quantum computer | |
| Base unit | Bits (0 or 1) | Qubits (0, 1, or superposition) |
| Information processing | Sequential (one bit at a time) | Parallel (overlay) |
| Measurement | Deterministic: To measure a bit in a conventional computer, the answer is always either 0 or 1. | Uncertainty (perturbation): The measurement of a qubit in a quantum computer determines its probabilistic state after existing in a superposition of 0 and 1. |
| Adaptability | Classic program | Adapting the Quantum Algorithm |
The benefits of quantum computing
Inputs in general
The quantum computer can be effective in a number of fields, since it can solve complex problems that would be impossible for a traditional computer.
The aim is to perform certain calculations in a matter of days, which would take tens, even millions or billions of years with a conventional computer.
This research is leading to advances in many scientific and industrial sectors:
Finance
The quantum computer is capable of performing massive calculations to better understand certain economic phenomena. What’s more, it can make complex predictions and classifications that are not possible today.
Health
The quantum computer will enable us to manufacture unknown drugs thanks to its ability to simulate increasingly complex molecules.
In addition, it can assist clinicians in identifying appropriate treatment protocols for patients by analyzing data. It also provides a detailed understanding of the reasons for the success or failure of medical protocols.
Meteorology
Weather forecasts rely on a large number of variables, such as atmospheric pressure, temperature and air density, making conventional simulations long and forecasts difficult beyond a few days.
However, many sectors such as agriculture, energy production, livestock farming, etc. base their activities on this information, particularly in geographical areas prone to natural disasters.
The quantum computer will make weather forecasts more reliable over time, helping to optimize activities in a variety of fields.
Contributions to IT security
Quantum computing is an asset for CISOs (Corporate Information Systems Security Managers). It offers better cybersecurity protection than conventional computers.
Taking the Quantum Origin platform as an example, we see that it uses quantum computing principles to create more flexible encryption keys based on the laws of quantum physics.
To understand this technology in depth, we need to look at a few concepts:
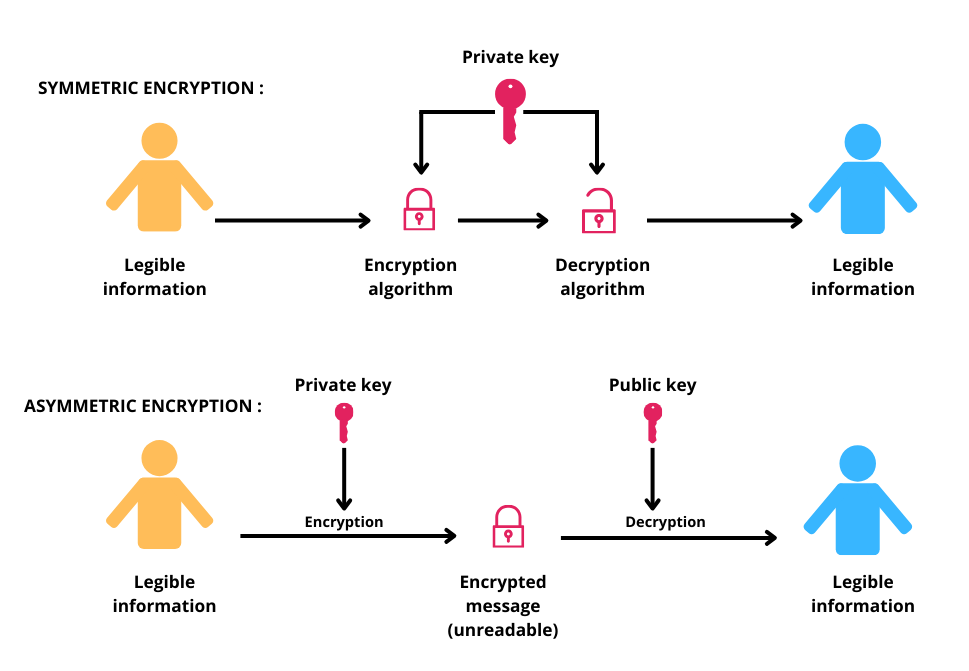
An encryption key and an encryption key are two related notions, as they are both needed to protect and access sensitive data.
The encryption key is used to transform the original data and information into ciphertext, while an encryption key is used to decrypt and recover the data as it was originally.
The classical encryption system uses highly complex mathematical algorithms. In quantum computing, classical bits are replaced by qubits, which can exist in several states thanks to quantum superposition. This creates keys that are potentially more resistant to cyber-attacks.
By using this quantum technology, companies can prevent cybercriminals from exploiting their encryption keys.
Threats from quantum computing
The main threat posed by quantum computers is that, if they reach a sufficiently high level of power, they could compromise the security of current cryptographic systems.
There are two types of quantum algorithm with distinct threats:
- Public-key cryptography, vulnerable to the Shor algorithm.
- Symmetric cryptography, vulnerable to Grover’s algorithm.
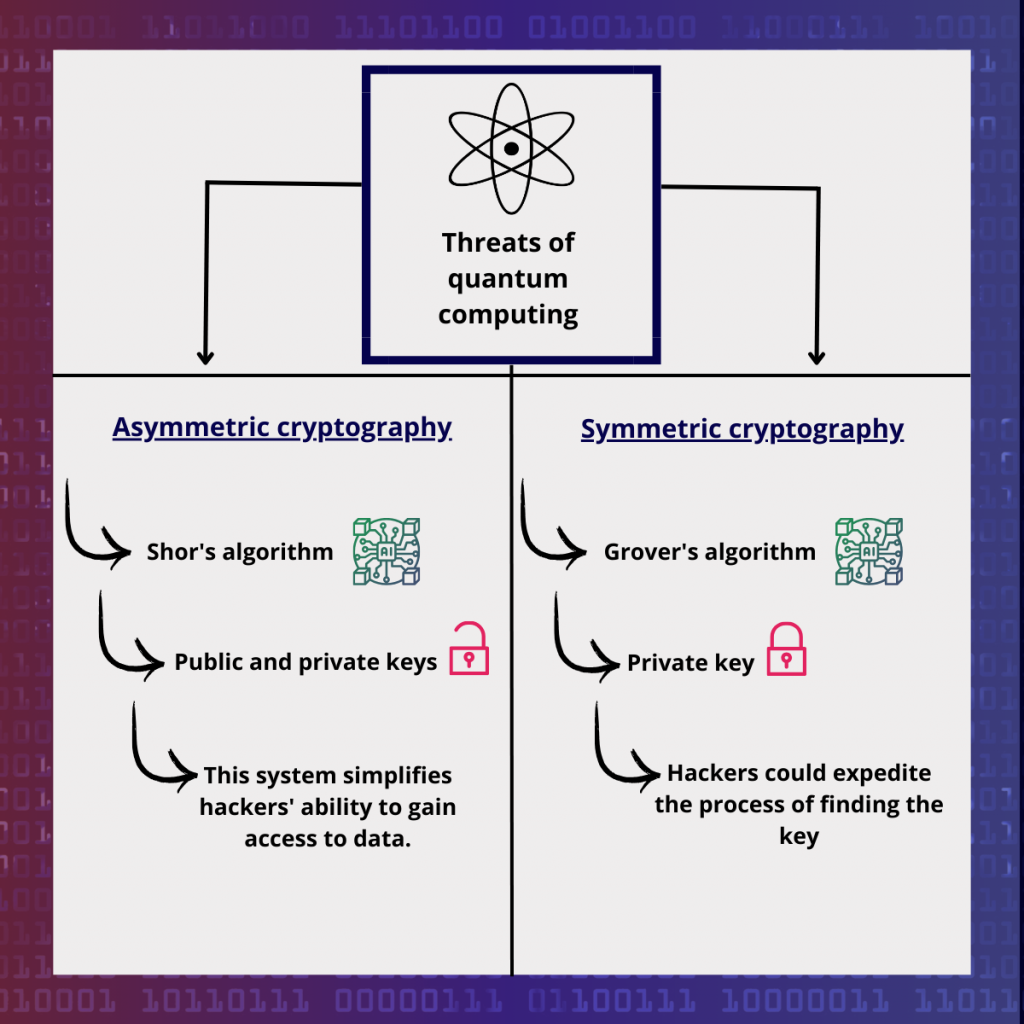
Threat to asymmetric cryptography
The quantum computer, using algorithms such as Shor’s algorithm, is specially designed to rapidly solve the integer factorization problem.
This feature could pose a serious threat to asymmetric encryption systems such as public key cryptography (PKC).
The latter is a cryptographic system using a distinct pair of keys, public and private, to facilitate secure communications between parties.
The public key is used to encrypt information, while the private key is used to decrypt it.
These quantum computers could rapidly decrypt keys considered secure today.
This would make it easier for hackers to access secure payment systems, forge the authenticity of electronic signatures, mine cryptocurrency, breach the confidentiality of digital envelope protocols, and more.
Security researchers are conducting ongoing research to develop post-quantum cryptography solutions to resist attacks from quantum computers.
Threat to symmetric cryptography
Symmetrical cryptography is a data encryption method in which a single key is used for both encryption and decryption.
Unlike the asymmetric cryptography explained above, the communicating parties share the same secret key to guarantee the confidentiality of the information exchanged.
Grover’s algorithm, developed in 1998, speeds up exhaustive key searches by exploring different key combinations in parallel until the right key is found.
In comparison, conventional methods require a considerable amount of time due to the large number of possible combinations.
However, this acceleration in key search represents a serious threat to the security of symmetric keys.
Hackers could find the key much more quickly than with traditional methods, thereby jeopardizing system security. This threat can be reduced by opting for longer keys.
Global solutions
Hybrid cryptography, currently seen as a promising approach to countering these threats, combines both classical and post-quantum cryptography, aiming to develop security methods capable of withstanding potential attacks from quantum computers.
France’s ANSSI (Agence Nationale de la Sécurité des Systèmes d’Information) is actively involved in post-quantum cryptography research, with a dual role:
Consultative
ANSSI often publishes European recommendations concerning the selection of post-quantum cryptography.
Regulatory
It establishes technical criteria for evaluating the security of products, then verifies that these products meet these standards by awarding them a security “visa”.
Finally, further research into post-quantum cryptography methods is needed to make attacks on quantum computers more complex.
