CyberNews February 2024
Discover the CyberNews for February 2024. This is the recap of news on Cybersecurity during the month of February 2024.
Discover the CyberNews for February 2024. This is the recap of news on Cybersecurity during the month of February 2024.
Lockbit & Operation Cronos
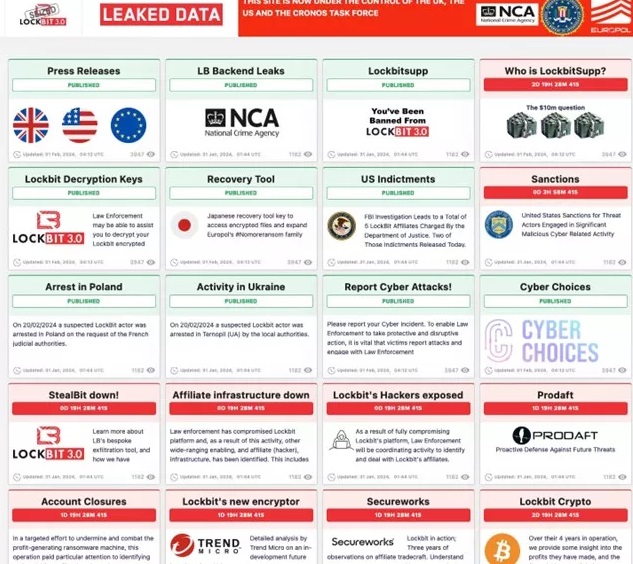
Operation Cronos
Operation Cronos, a large international operation carried out on February 20, 2024, dealt a significant blow to the LockBit ransomware group.
This collaboration, involving 10 countries including France, the United States, Japan and the United Kingdom, made it possible to dismantle a significant part of the cybercriminal group’s infrastructure.

Concretely, the operation made it possible to:
- Seize 34 LockBit servers hosted in Europe, the United Kingdom and the United States.
- Freeze 200 cryptocurrency accounts used by the group to launder its profits.
- Shut down 14,000 accounts used to launch attacks and spread LockBit ransomware.
This action is the result of a multi-year investigation carried out by prestigious investigative agencies such as the FBI, ANSSI and Europol. International collaboration was essential to identify the group’s members, locate their infrastructure and coordinate dismantling actions.
LockBit is a particularly active ransomware group in recent years. It is responsible for numerous cyberattacks against organizations of all types, including hospitals, public administrations and private companies. Notable victims of LockBit include the Corbeil-Essonne hospital in France and the electronics group Thales.
What Lockbit said about this attack on their services: “Due to my personal negligence and irresponsibility, I relaxed and did not update PHP on time. The servers had PHP version 8.1.2 installed, which was successfully tested for penetration, most likely because of this CVE https://www.cvedetails.com/cve/CVE-2023-3824/”.
Return of Lockbit
Less than a week after Operation Cronos, on February 27, 2024, the LockBit ransomware group returned to the cybercriminal scene with disconcerting speed.
This resurgence highlights the adaptability and resilience of cybercriminals in the face of repressive actions, even when they are coordinated on an international scale.
The return of LockBit is characterized by:
Provocative communication
The group published a message on the dark web, downplaying the impact of Operation Cronos and affirming its determination to continue its criminal activities.
This message is reminiscent of the arrogant posture adopted by other ransomware groups, such as Maze and REvil, after suffering similar setbacks.
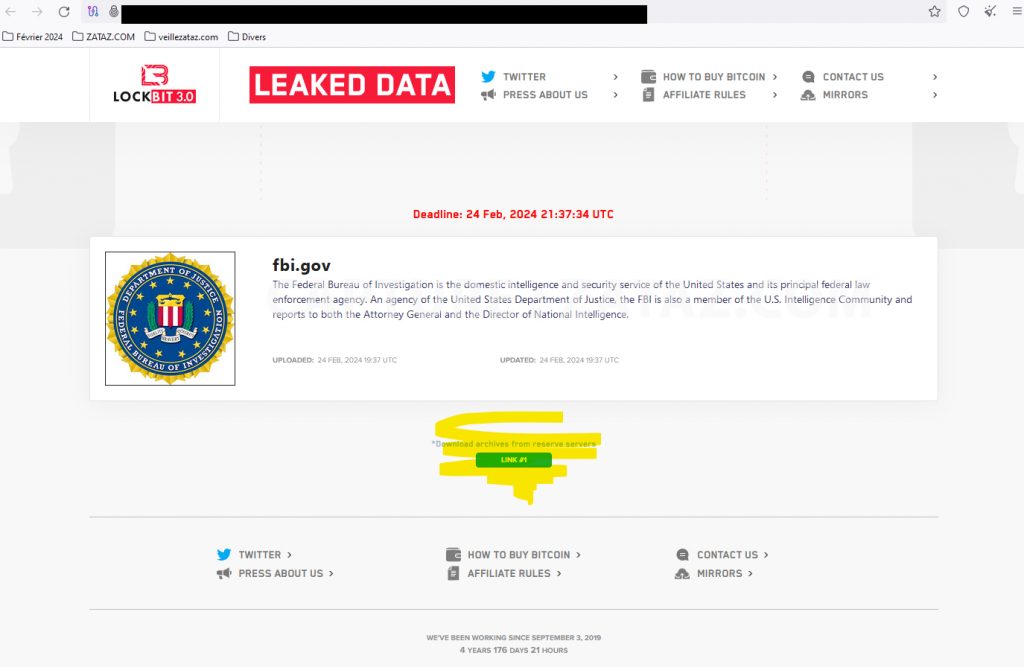
Lockbit on the FBI in Operation Cronos : “beautiful advertising from the FBI, which is that my affiliates and I earn together hundreds of millions of dollars, and that no FBI with their assistants can scare me and stop me, the stability of the service is guaranteed by years of continuous work.”
A technical evolution
LockBit quickly released a new version of its ransomware, LockBit 3.0, which includes increased functionality to evade organizations’ defenses.
This release notably includes new data obfuscation, encryption and exfiltration techniques, as well as the ability to target specific systems and exploit zero-day vulnerabilities.

$1.1 billion in ransoms paid by companies in 2023
The year 2023 marked a resurgence of cybercriminals using ransomware, who received a record amount of at least $1.1 billion in ransoms.
This is the first time that $1 billion has been crossed, according to blockchain analysis company Chainalysis.
This meteoric growth shows that ransomware poses a growing threat to global IT security.
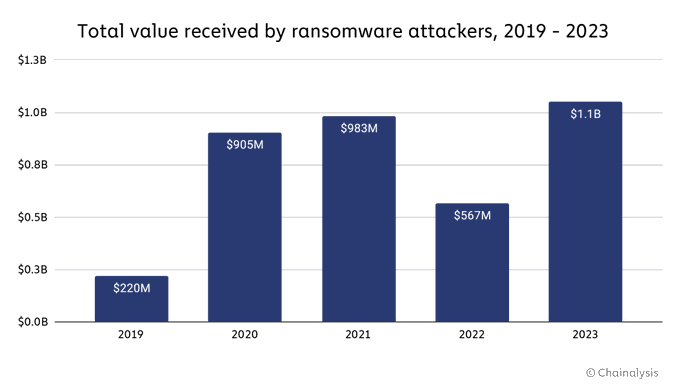
According to the company’s data, the share of ransoms of $1 million and above reached almost 80% by the end of the year.
One of the biggest trends seen in 2023 is the rise of ransomware-as-a-service (RaaS).
These services allow inexperienced cybercriminals to rent ransomware and launch sophisticated attacks without having to develop their own tools. This development has contributed to the democratization of ransomware attacks, making them accessible to a greater number of individuals.
The most active ransomware groups in 2023
- LockBit: This group is responsible for the attack on Colonial Pipeline, which caused a gasoline shortage in the eastern United States in May 2021.
- Conti: This group has been particularly active in the health care sector, where it has targeted hospitals and clinics.
- Hive: This group is known for its aggressive approach and threats to leak sensitive data if the ransom is not paid.
- BlackCat: This group is relatively new, but has quickly gained notoriety due to its attacks on high-profile organizations.
Sectors most affected by ransomware attacks in 2023
- Healthcare: Hospitals and clinics are prime targets for cybercriminals because they rely on their IT systems to provide patient care.
- Education: Schools and universities are often underfunded when it comes to IT security, making them vulnerable to attacks.
- Governments: Public administrations are prime targets because they hold sensitive data and may be forced to pay the ransom to avoid major disruptions.

The Data of 33 Million French People Exposed by the Viamedis & Almerys Attack
In January 2024, two third-party payment management companies, Viamedis and Almerys, were victims of a large-scale cyberattack.
This attack had major consequences, exposing the personal data of more than 33 million people in France, or almost half of the French population.
Compromised data
The attack allowed hackers to access a wide range of sensitive information, including:
- First and last names.
- Dates of birth.
- Social Security Numbers.
- Postal addresses.
- Health and supplementary insurance details.
Investigations and measurements
Viamedis and Almerys
- Deployment of additional security measures to limit damage and prevent further attacks.
- Setting up a monitoring platform for affected people, allowing them to find out about the steps to follow and benefit from assistance.
- Regular communication on the evolution of the situation and the measures taken to protect customer data.
CNIL
- Opening of an investigation to determine the circumstances of the cyber attack and possible breaches of regulations on the protection of personal data.
- Publication of recommendations for those affected, telling them how to protect themselves against the risks of fraud and identity theft.
French government
- Creation of an interministerial crisis unit to coordinate response actions to the attack and provide support to victims.
- Strengthening means to combat cybercrime and raising public awareness of digital risks.

Sidaction victim of a cyber attack
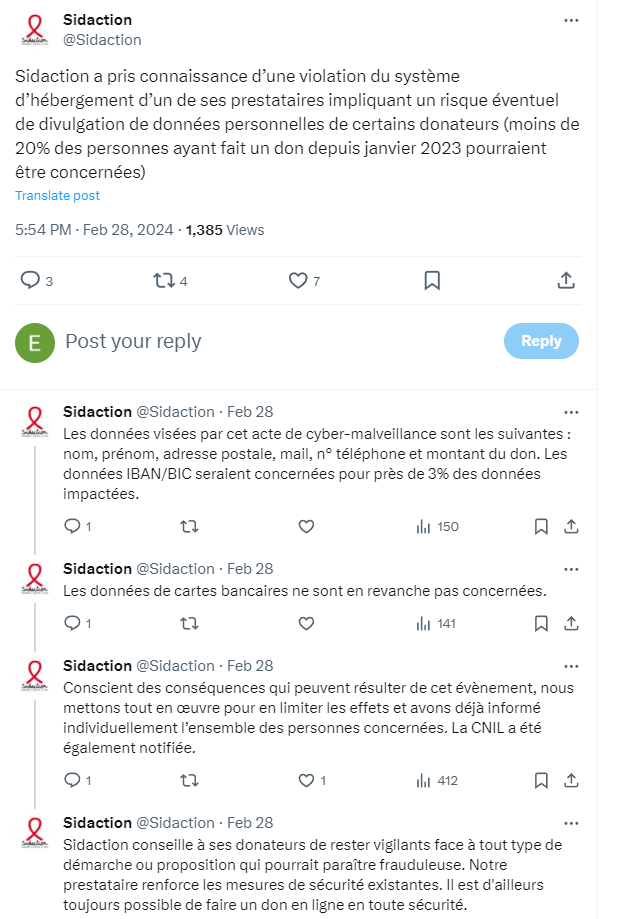
The Sidaction association revealed on February 28, 2024 that it had suffered a cyberattack that potentially exposed the personal data of certain donors.
Data impacted and scale of the attack
- Less than 20% of donors who have made a donation since January 2023 are potentially affected by the cyberattack.
- Compromised data includes first and last names, postal addresses, telephone numbers, email addresses and donation amounts.
- For around 3% of donors, banking information (IBAN and BIC) could also be exposed.
- Bank card data is not affected according to Sidaction.
Reaction of the association
- Sidaction contacted donors potentially affected by the email attack and recommended that they monitor their bank accounts.
- A toll-free number (0 800 840 800) has been set up to answer donors’ questions.
- The association also filed a complaint with the police.
- The CNIL was also informed of this cyberattack.
- An investigation is underway to determine the origin and scale of the attack.

Ransomware at Armentières hospital
On February 11, 2024, the Armentières hospital center was the target of a ransomware cyberattack. This attack had a major impact on the operation of the hospital, disrupting access to patient data and forcing the closure of the emergency room for 24 hours.
Timeline of the attack
- February 11: Start of the attack. The hospital’s computer system is infected with ransomware, blocking access to patient data and disrupting the operation of services. This ransomware was sent by the BlackOut hacker group.
- February 12: Emergency closure for 24 hours. The hospital is forced to take this measure in order to limit the impact of the attack and protect sensitive data.
- February 13: Establishment of a crisis unit. The hospital is setting up a crisis unit to manage the situation and communicate with patients and staff.
- February 25: Data leak. Hospital computer files, potentially containing sensitive data of 300,000 patients, are released online.
- In progress: Investigation in progress. The national gendarmerie and the ANSSI (National Agency for Information Systems Security) are carrying out an investigation to identify those responsible for the attack and find the stolen data.
Consequences of the attack
- Disruption of hospital operations: The attack disrupted the operation of the hospital, in particular access to patient data and the operation of services.
- Emergency closure: The hospital was forced to close the emergency room for 24 hours to limit the impact of the attack and protect sensitive data.
- Data leak: The leak of sensitive data of 300,000 patients is a serious event which can have significant consequences for the people concerned.
Reactions and measures taken
- Complaint filed: The hospital filed a complaint with the national gendarmerie.
- Crisis unit: The hospital has set up a crisis unit to manage the situation and communicate with patients and staff.
- Support from ANSSI: ANSSI provides support to the hospital to help it restore its computer system and secure its data.
Press release from CH Armantiers:

France Identity launches a Bug Bounty
France Identity is a French application allowing you to group your identity documents on your phone and thus provide proof of identity.
The France Identity application, until then in Beta in certain departments of France, opened to all of France in February 2024.
On February 28, 2024, the France Identity application launched a “bug bounty” program to encourage hackers to find security vulnerabilities in its system. This program is a welcome initiative that will help improve the security of the application and build user trust.
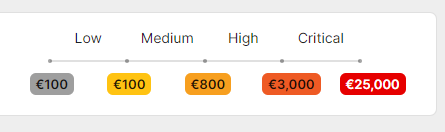
The program is open to everyone and offers rewards ranging from 100 euros for a minor flaw to 25,000 euros for a critical flaw.
Types of vulnerabilities looked for include:
- SQL code injection: This flaw allows an attacker to execute arbitrary SQL code on the application database server.
- Cross-site scripting (XSS): This flaw allows an attacker to inject JavaScript code into a web page that the user is viewing. This code can then be used to steal cookies, session information or to redirect the user to a malicious website.
- Cross-site request forgery (CSRF): This flaw allows an attacker to force the user to perform an unwanted action on a web application.
- Remote Code Execution (RCE): This flaw allows an attacker to execute arbitrary code on the application server.
- Elevation of privileges: This flaw allows an attacker to obtain higher privileges on the application system.
To participate in the program, hackers must register on the YesWeHack platform. They can then submit vulnerability reports through the platform. All reports will be reviewed by a security team and bounties will be paid to hackers who find valid vulnerabilities.

Wyze: 13,000 customers exposed to private images
A security flaw in Wyze cameras allowed around 13,000 users to view live feeds and potentially recordings from other users’ cameras.
This breach allowed strangers to unwittingly access images of other people’s homes, potentially exposing their privacy to serious violations.
Incident details
- Fault: A bug in a third-party cache library used by Wyze allowed users to access other users’ camera feeds without authorization.
- Impact: The breach allowed users to view live footage from other people’s cameras, and in some cases, download stored recordings.
Response from Wyze
- Wyze expressed its regrets to customers affected by the security breach.
- The company updated the firmware of its cameras to fix the vulnerability.
- Wyze also notified users affected by the breach and advised them to change their passwords.
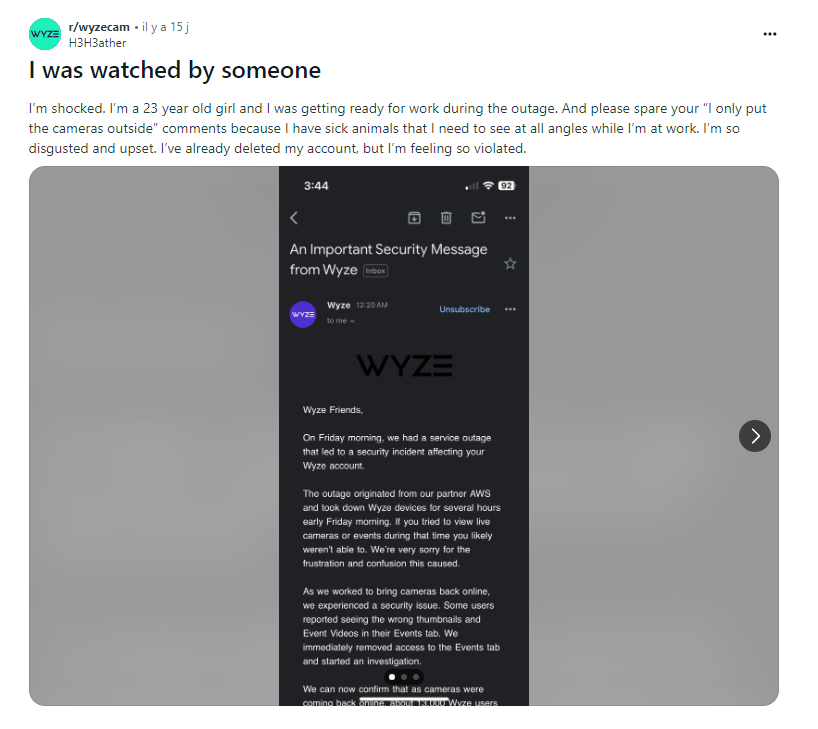
Part of the Wyze email sent to customers
“On Friday morning we had a service outage which resulted in a security incident. […] The outage originated from our partner AWS and knocked out Wyze devices for several hours early Friday morning. If you tried to view live cameras or events during this time, you probably weren’t successful. We are truly sorry for the frustration and confusion this has caused.
As we worked to get the cameras back online, we encountered a security issue. Some users have reported seeing incorrect event thumbnails and videos in their Events tab. We immediately removed access to the Events tab and launched an investigation.
We can now confirm that as cameras came back online, around 13,000 Wyze users received camera thumbnails that weren’t theirs and 1,504 users tapped on them. Most clicks enlarged the thumbnail, but in some cases an event video could be viewed. All affected users have been informed. […] The incident was caused by a third-party caching client library that was recently integrated into our system. This client library experienced unprecedented load conditions caused by devices coming back online simultaneously. Due to increased demand, it mixed up the mapping of device IDs and user IDs and connected some data to incorrect accounts. […]
The Wyze team”

Critical security flaw in Microsoft Outlook
On February 26, 2024, a critical security vulnerability was discovered in Microsoft Outlook for Windows. This flaw, named CVE-2024-21413, allows hackers to remotely take control of user computers.
Exploitation of the flaw
- A hacker sends a malicious email to an Outlook user.
- The email may come from a legitimate source (bank, telephone operator, administration) or from a friend/colleague whose account has been hacked.
- If the user opens the email, clicks on a link or opens an infected attachment, the hacker can: Execute code on the computer, Steal sensitive data (personal information, passwords, banking data) , Install malware (ransomware, keyloggers) or even take control of the company’s computer network (if the computer is connected to the network).
The CVE-2024-21413 flaw is a serious threat to the security of Outlook users. It is important to take the necessary steps to protect yourself against this vulnerability.
The flaw has since been resolved by Microsoft. If the Outlook application has not been updated, “cybercriminals could very soon exploit this vulnerability to carry out massive attacks against vulnerable systems,” explains the Cybermalveillance.gouv.fr platform.

The compromise of several thousand CAF accounts
On February 12, 2024, a group of hackers called “LulzSec” published a message on Twitter, followed by a publication on the RaidForums forum, claiming to have hacked the Family Allowance Fund (CAF) and exfiltrated the personal data of 600,000 beneficiaries.
They also uploaded a sample of 10,000 accounts to support their claims, containing:
- Nouns.
- Addresses.
- Social security numbers.
- Banking information.
CAF immediately reacted by issuing a press release denying the scale of the hack. The organization affirmed that an internal investigation had revealed no major intrusion into its systems, but rather the compromise of 4 accounts following a technique of “credential stuffing” (use of hacked passwords on other platforms).
On February 29, 2024, CAF confirmed the data leak of several tens of thousands of accounts.
The data concerned includes:
- First and last names.
- Postal addresses.
- Telephone numbers.
- Social security numbers.
- Banking information (RIB).
- Amounts of allowances paid.
- Payment dates.
CAF said the leak affected 0.08% of its beneficiaries, or around 60,000 accounts.
The organization also indicated that the data was not stolen, but that it was accessible to unauthorized persons due to a security breach in an external provider.

Two critical flaws in Fortinet’s FortiSIEM
Two critical security vulnerabilities have been discovered in FortiSIEM, a Security Information & Event Management (SIEM) solution from Fortinet.
These flaws, named CVE-2024-23108 and CVE-2024-23109, allow hackers to execute prohibited commands remotely and access sensitive data.
Exploitation of vulnerabilities
Technical operation
The flaws lie in the processing of API requests by FortiSIEM. A hacker can exploit these flaws by sending specially crafted counterfeit API requests to trick the system.
Examples of exploitation
- Command Execution: An attacker can send a malicious API request to execute arbitrary commands on the FortiSIEM system. This could allow it to install malware, delete files or change configurations.
- Data Access: A hacker can send a malicious API request to access sensitive data stored in FortiSIEM. This could include event logs, user credentials, and network configuration data.
Impact of vulnerabilities
Scope
Millions of FortiSIEM users around the world are potentially affected. This vulnerability affects both individuals and businesses, including government organizations and large critical infrastructures.
Possible consequences
- Compromise of Sensitive Data: Hackers can steal sensitive information such as usernames, passwords, financial data, and trade secrets.
- Disruption of Operations: Hackers can disrupt operations by disabling services or corrupting data.
- Significant financial damage: Businesses can suffer significant financial losses due to data theft, ransomware, and business disruption.
- Reputational damage: Loss of sensitive data can harm a company’s reputation and customer trust.
It is crucial to update FortiSIEM to version 6.2.3 or later as soon as possible. Fortinet has released fixes for versions 6.0.0 to 6.2.2.

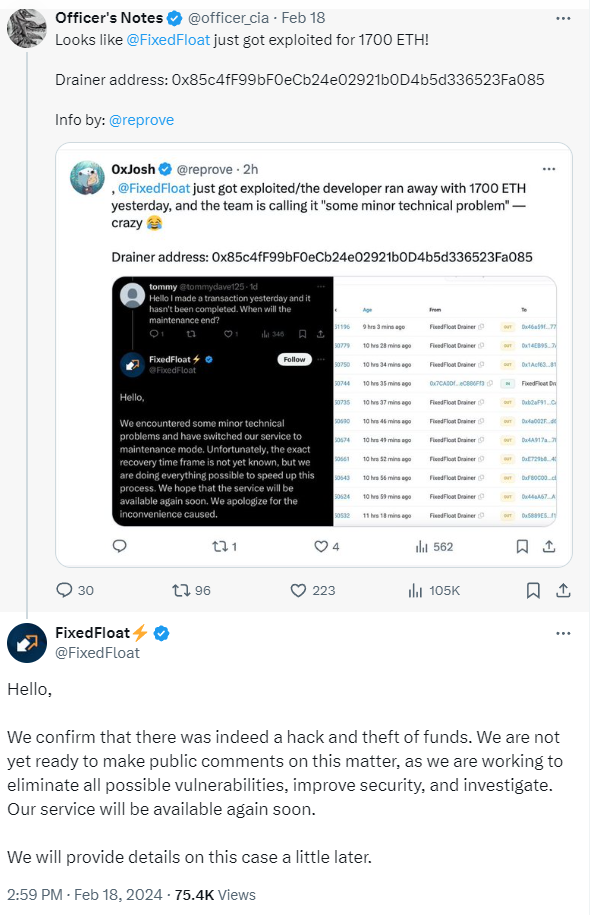
FixedFloat exchange platform victim of €26M hack
Cryptocurrency exchange FixedFloat suffered a major hack, resulting in the theft of €26 million in cryptoassets.
This cyberattack, far from being an isolated case, has affected the crypto community and raises crucial questions about the security of exchange platforms and the responsibility of the actors involved.
Hacking process
The hackers exploited a security flaw in FixedFloat’s system, likely a software vulnerability or human error.
This flaw allowed them to access the platform’s wallets and steal 1,728 ETH (approximately 18 million euros) and 409.3 BTC (approximately 8 million euros) at the time of the theft.
Consequences of hacking
- Financial Losses: FixedFloat users who had funds stored on the platform suffered significant losses. Some have lost their entire savings in cryptocurrencies.
- Suspension of Services: Following the hack, FixedFloat has suspended its trading and deposit/withdrawal services indefinitely. This decision caused frustration and uncertainty among users.
- Breach of trust: The cyberattack has shaken trust in the platform and the entire cryptocurrency industry. The security of exchange platforms and the protection of user funds are now in question.

Two-Factor Authentication (2FA) Codes Leaked at YX International
Millions of Facebook, Google, WhatsApp and TikTok users have had the security of their accounts compromised after an SMS routing company left one of its internal databases exposed to the internet without a password and leaked two-factor authentication (2FA) codes that were supposed to be private.
The company in question is YX International, which provides SMS routing services to a number of large technology companies. YX International claims to send 5 million SMS messages daily.
The exposed database contained information on several million accounts, including phone numbers, email addresses and 2FA codes.
2FA codes are used to add an extra layer of security to online accounts. In addition to a password, users are asked to enter a 2FA code which is usually sent to their phone via SMS.
This ensures that even if a hacker manages to obtain a user’s password, they will not be able to access their account without the 2FA code.

Deepfake scam – $25M stolen
In early February, an employee of a Hong Kong-based multinational was the victim of a sophisticated scam using “deepfake” technology.

The employee received an email from his manager asking him to participate in a video conference.
During the videoconference, which appeared to involve his superior and other colleagues, he was instructed to transfer $25 million to foreign bank accounts.
However, video conferencing was actually a deepfake, a technology that allows you to create very realistic fake videos. The scammers had used images and voices of the employee’s superiors and colleagues to deceive him.
“During this multi-person video conference, it turned out that all the people except him were fake, but seemed larger than life,” a senior police official, Baron Chan Shun-ching, told the public broadcaster RTHK.
It was only later that he realized he had been scammed.
This type of scam, called the “president scam”, is becoming more and more widespread. Scammers are using increasingly sophisticated techniques to deceive their victims.
It is important to remain vigilant against this type of scam. Here are a few tips :
- Never make a money transfer based on a single instruction, even if it comes from a superior.
- Check the authenticity of the email and the sender.
- Contact your supervisor directly by another means to confirm their instructions.
- If in doubt, do not hesitate to contact the police.
The company said it will take all necessary steps to recover the money and prevent such scams from happening again.
This incident highlights the need to educate businesses and employees about the risks of online scams.

IA ACT – EU Member States give the green light
On February 2, 2024, the ambassadors of the 27 member states of the European Union unanimously approved the AI Act, a comprehensive regulatory framework on artificial intelligence.
It is the world’s first artificial intelligence law, and aims to ensure that AI is developed and used ethically and responsibly.
The AI Act classifies AI systems based on their level of risk. High-risk systems, such as those used in critical infrastructure, education, law enforcement and credit rating, will be subject to strict requirements.
These requirements include:
- Human control over decision making.
- Complete technical documentation.
- A risk management system.
- A conformity assessment by an independent body.
Prohibited AI systems include those that:
- Manipulate people.
- Exploit vulnerabilities.
- Cause physical or psychological harm.
The adoption of the AI Act is an important step for the European Union. It shows that the EU is committed to playing a leading role in the development and use of AI in an ethical and responsible manner.
