Black Friday cybersecurity: how to protect yourself from cyberattacks
Black Friday is an ideal time for cybercriminals. They take advantage of the influx of traffic to attack and steal sensitive information.
Black Friday and Cyber Monday are two major shopping events that attract millions of shoppers online and in-store.
This high volume of traffic creates an opportunity for cybercriminals to launch attacks aimed at stealing personal data, payment information and sensitive information.
Cybersecurity & Black Friday : The Risks
Be sure of one thing, cybercriminals clearly do not lack creativity. They use a variety of different techniques to target consumers during Black Friday and Cyber Monday.
Here are the most common risks and types of attacks.
Phishing
During the Black Friday period, Phishing attacks increase by 440% compared to the rest of the year.
The principle of this type of attack is very simple.
Criminals send fraudulent emails, or text messages, that appear to come from a legitimate source, such as a business or bank.
These messages often contain booby-trapped links or attachments that, when clicked, install malware or redirect the user to a fraudulent website.
Example of Phishing
A cybercriminal could send a fraudulent email claiming to come from your bank.
The email could indicate that your bank account is in danger and that you need to click on a link to secure it.
If you click on the link, you will be redirected to a fraudulent website that looks like your bank.
Once you enter your login details on this fake site, cybercriminals will be able to use them to access your real bank account.
Concrete case of a Phishing email
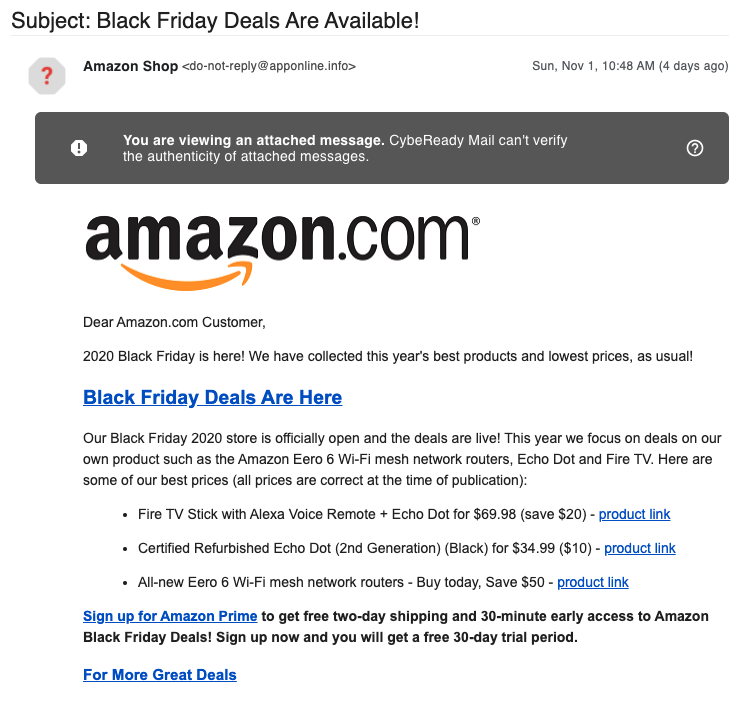
The image below shows an email phishing attack from Amazon.
The email here is quite rude.
The elements that can alert are:
- No design, too classic an email
- An email address that has nothing to do with Amazon
- The presence of questionable links
- And other rather crude details
Price fraud
Cybercriminals create fraudulent websites or applications that imitate legitimate retailer websites.
These websites often offer incredibly low prices to attract buyers, but they never deliver the promised products or services.
Example of price fraud
For example, a cybercriminal could create a website that looks like a popular retailer’s website.
The website could offer cell phones at an incredibly low price. If you buy a cell phone from the scam website, you will never receive the phone.
Instead, you risk losing your money or having your personal information compromised.
Concrete case of price fraud
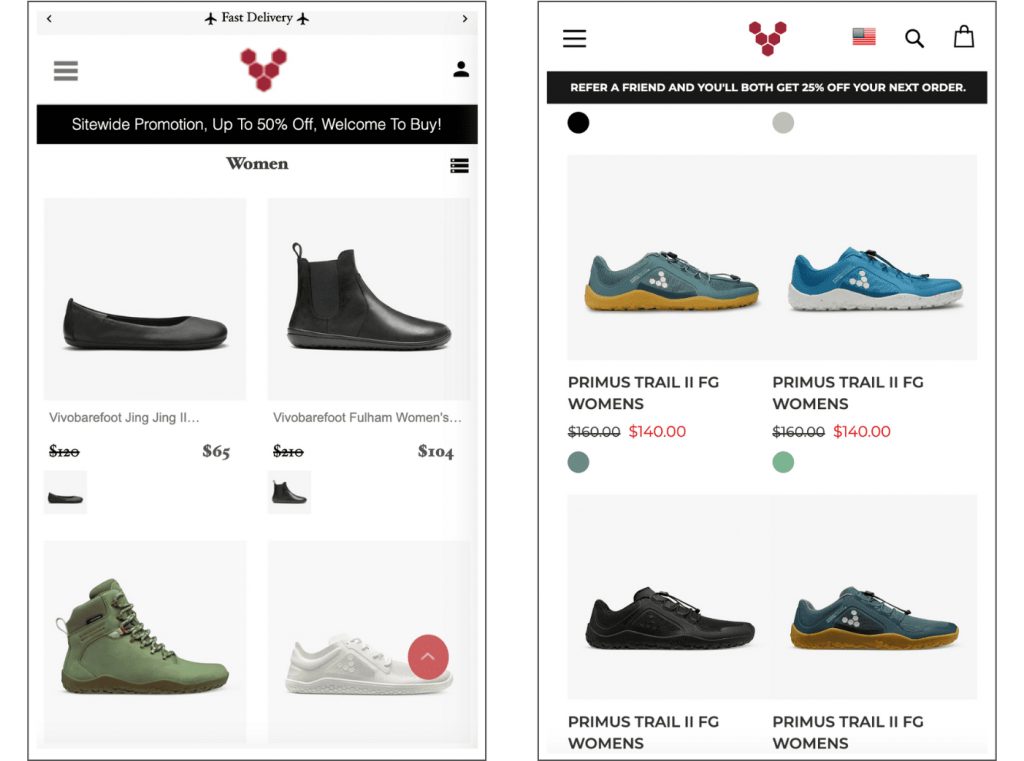
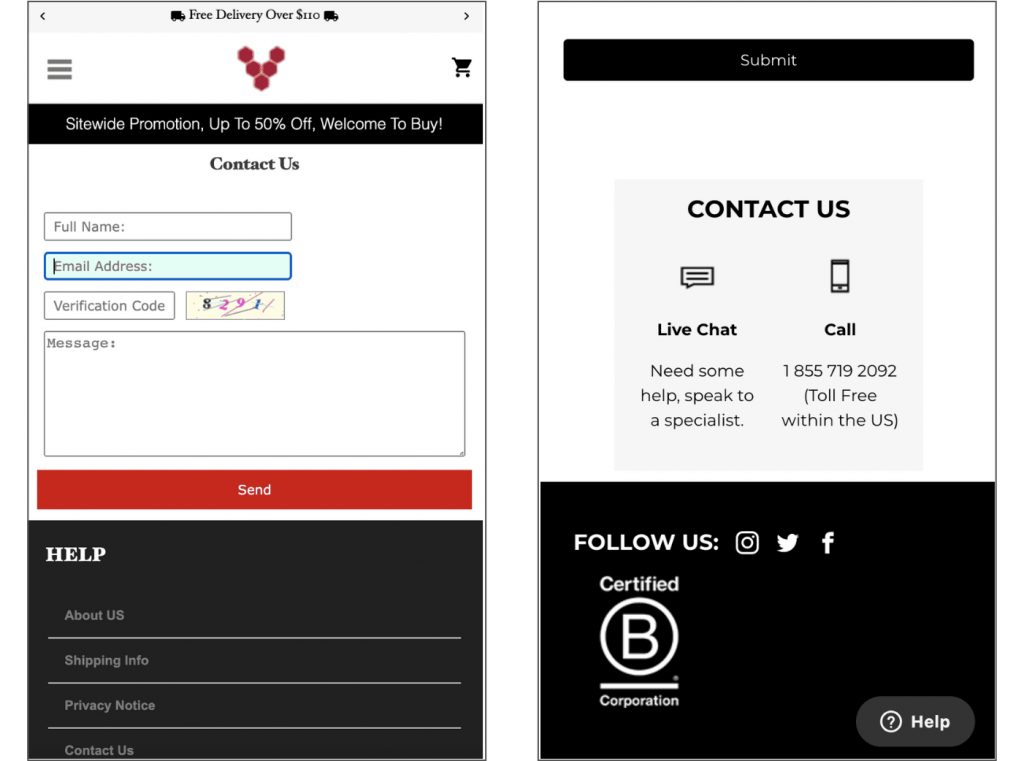
In the case below, there are two sites. They may look similar, but they are not. The second site is the official one, the first is the usurper.
Several clues can tell us that the first is a fake site:
- The site logo is blurry in the first version
- The promotions are quite exaggerated, with 50% off
- The phrase “Reinsurance” at the top pushes too much towards purchasing and highlights low prices too much
- If you explore the site further, you will have other worrying points such as spelling mistakes, or the contact page which looks very amateurish and which makes no mention of a telephone number.
Account takeover fraud
Cybercriminals use techniques such as phishing or identity theft to take control of users’ online accounts.
Once they take control of an account, they can use the user’s personal information to make fraudulent purchases, access bank accounts, or steal sensitive information.
Example of account takeover fraud
For example, a cybercriminal could use phishing techniques to steal your email account login information.
Once they have access to your email account, they can use your information to access other online accounts, such as your bank accounts or social media accounts.
Distributed denial of service (DDoS) attacks
Cybercriminals use networks of infected machines (botnets) to send a massive amount of traffic to a website or application.
This can overwhelm the site’s servers and make it inaccessible to legitimate users.
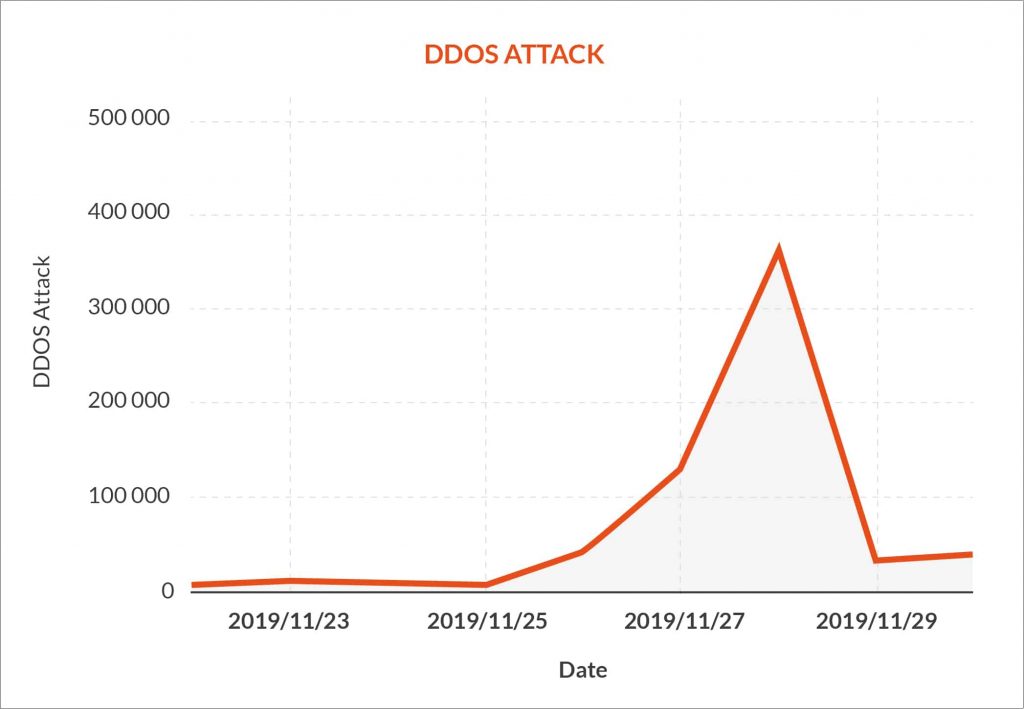
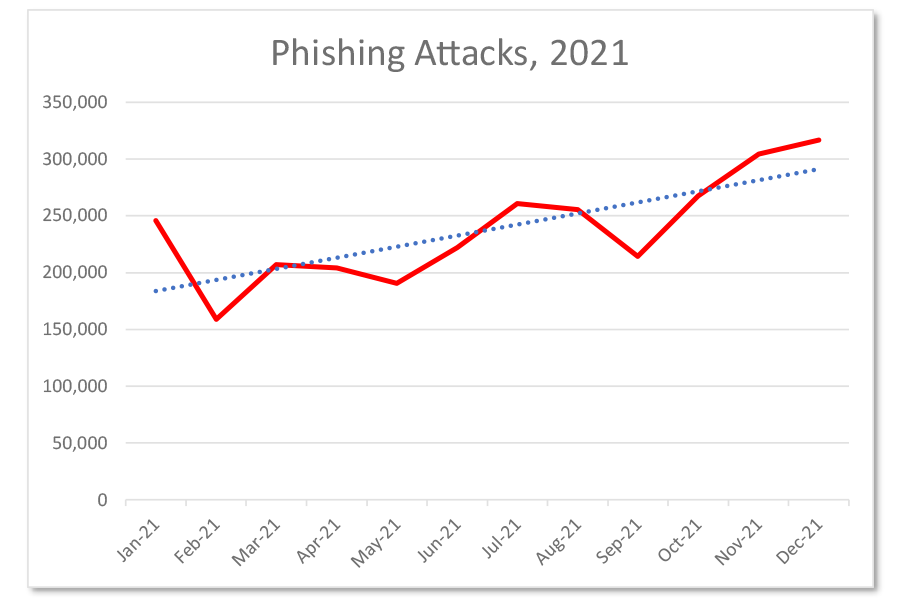
As the graph below shows, in 2019, during Black Friday, there were over 350,000 DDoS attacks.
DDoS attack example
For example, a cybercriminal could launch a DDoS attack against a popular retailer’s website.
If the DDoS attack is successful, the retailer’s website could be inaccessible for several hours or even days.
This could prevent consumers from purchasing products or services during Black Friday or Cyber Monday.
Protect yourself against Cybersecurity risks during Black Friday
Whether you are a simple customer or a merchant, cyberattacks are very present during the Black Friday period.
It is therefore essential to take measures to protect yourself against the cybersecurity risks linked to Black Friday and Cyber Monday.
Cybersecurity advice for consumers
Be careful with emails and text messages
Never click on a link or open an attachment in an email or text message that you weren’t expecting.
If you receive an email or text message from a company you know, check the sender’s email address or phone number before opening the email or clicking the link.
Use strong, unique passwords
Never reuse the same password for multiple accounts. We strongly recommend using a password manager to generate and store strong, unique passwords for all your accounts.
Enable two-factor authentication
Two-factor authentication adds an extra layer of security to your accounts by requiring an additional code during login.
Be careful where you buy
Research retailers before shopping online. Read customer reviews and check that the retailer has a clear and generous returns policy.
Beware of deals that seem too good to be true
If a deal seems too good to be true, it probably is. Cybercriminals often use tempting offers to lure consumers to fraudulent websites or fraudulent applications.
Check your bank statements carefully
Report any fraudulent transactions to your bank or credit card company immediately.
Be careful when sharing personal information online
Never share your personal information, such as your Social Security number or bank account information, on a website you are not sure you know and trust.
Use antivirus and firewall
Antivirus and firewall can help protect your computer from malware and hackers.
Be careful when using public Wi-Fi networks
Public Wi-Fi networks are not secure and can be used by cybercriminals to steal your data.
Avoid making financial transactions or accessing sensitive information over public Wi-Fi.
Cybersecurity advice for businesses
Educate your employees on cybersecurity risks
Make sure your employees are aware of cybersecurity risks and know how to protect themselves. Raise awareness among all your employees of the issues, threats and risks of IT security. Provide them with all the protection methods that make the difference in the event of a cyber attack.
Implement strict security policies
Make sure your employees follow strict security policies, such as using strong passwords and enabling two-factor authentication.
Check your IT systems for vulnerabilities
Have your IT systems regularly checked by security experts to identify and fix vulnerabilities.
To do this, we recommend that you carry out a pentest, or intrusion test, once a year. A penetration test makes it possible to identify the vulnerabilities of a computer system as hackers would do.
We also strongly recommend having a vulnerability scanner, it can automatically detect security vulnerabilities on websites and web applications.
Have an incident response plan in place
Have a plan in place to respond to cybersecurity incidents. We recommend that you get help from an Incident Response team who will support you on this journey.
From threat detection to remediation, the Ziwit Incident Response Team supports you throughout the process to guarantee maximum and prolonged security.
