The Booking.com site and the security breach of its internal messaging
Since December 2022, customers booking on the Booking.com site have found themselves the target of cybercriminals acting on behalf of the booking site.
In this blog article, we will see the modus operandi of this cyberattack.
Since December 2022, customers booking on the Booking.com site have found themselves the target of cybercriminals acting on behalf of the booking site.
In this blog article, we will see the modus operandi of this cyberattack.
Please note that we have interview a victim of this cyberattack.
The course of the attack
This passage of the article will be written in the first-person singular. In fact, it relates the victim’s experience.
It all starts on November 2, 2023. That day, I decide to spend 4 days in Rome in March 2024.
For this, I plan to book a hotel, and so I go to the Booking.com website.
So I find my happiness and complete my confirmation.
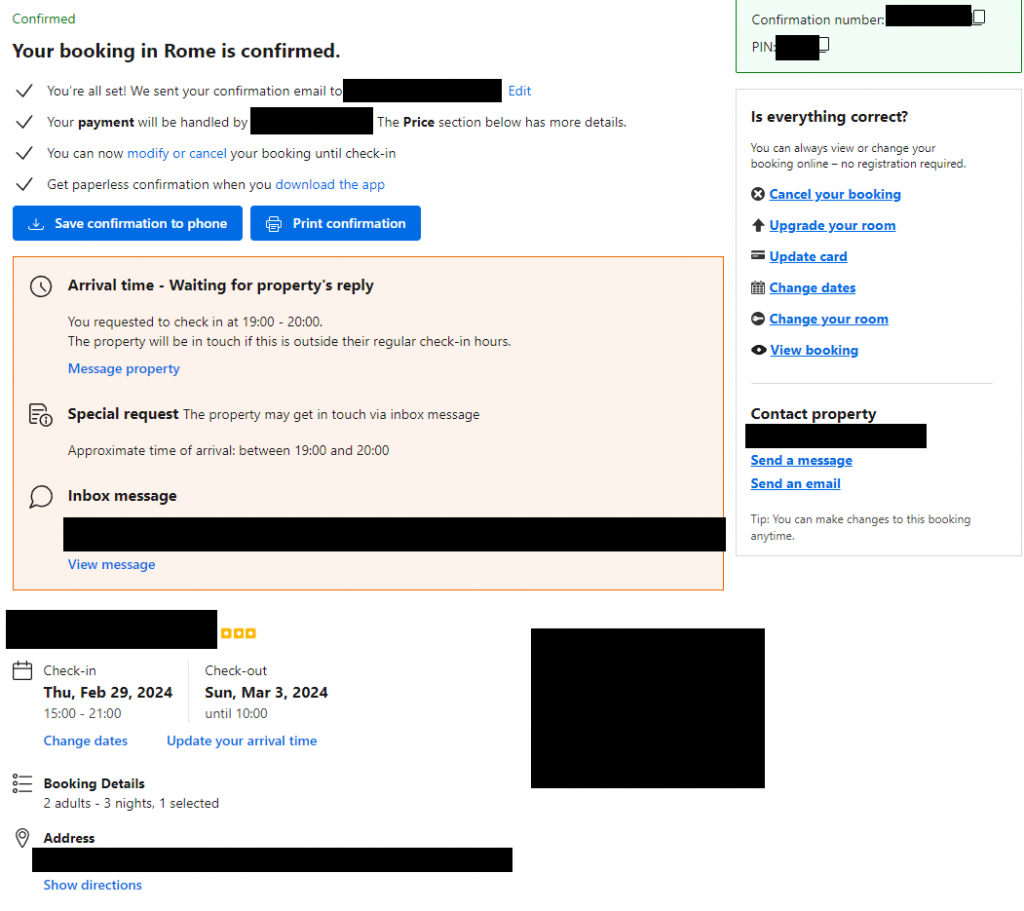
An hour later, I received a message from the hotel directly in the site’s internal messaging system.
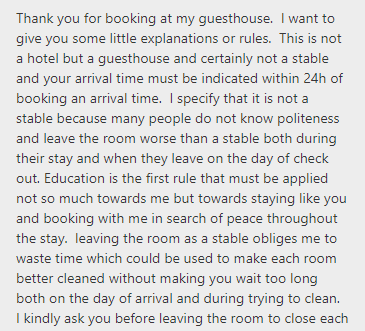
This message is nothing special and just explains that the host wants us to respect his Guest House.
Theft of bank card data
About an hour later, I received a second message.
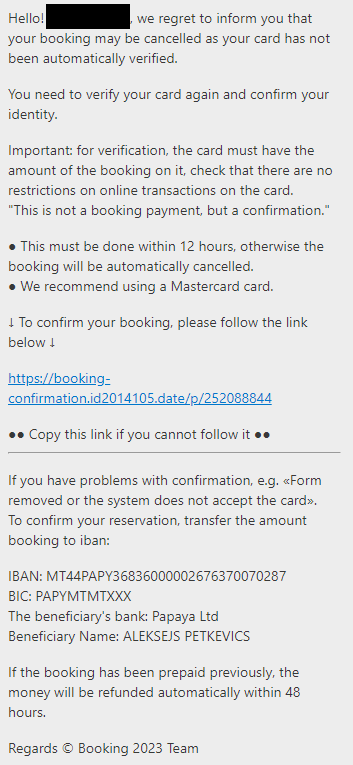
This message roughly explains that I must prepay my reservation within 48 hours or my reservation will be canceled.
Once you click on the link, you end up on this page:
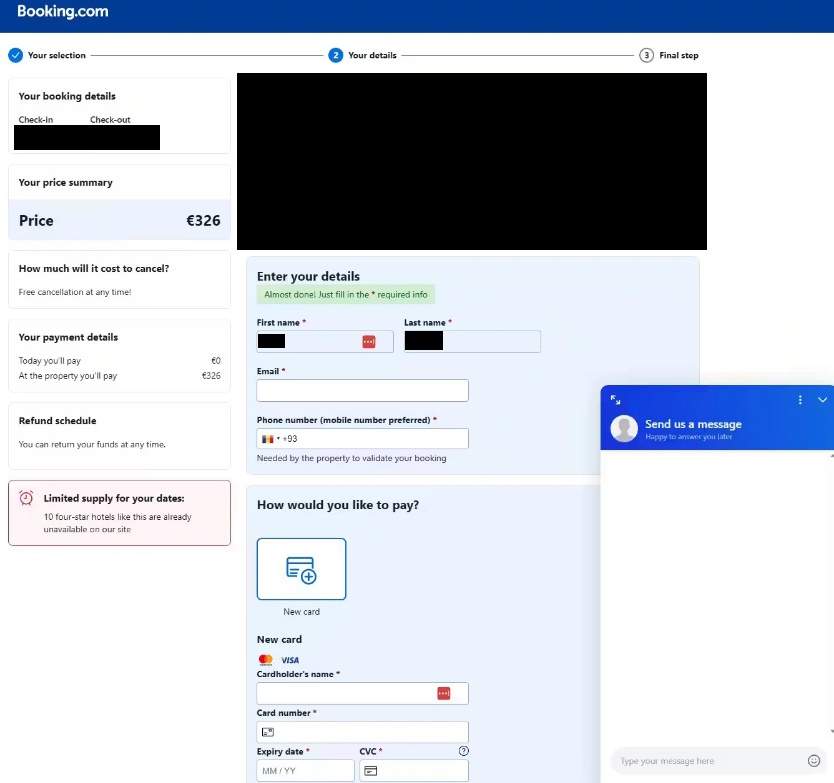
On this page, a lot of information from my confirmation is included, including the price, the name of the hotel, my first and last name, the reservation dates and also the reservation number.
On this page, we are asked to enter the first and last name information, which is already pre-filled, then the email address, the telephone number and finally the bank card information.
Once all these fields are filled, a page with loading appears, and this loading is actually infinite.
Since it was loading endlessly, I sent a message in voice chat saying it’s not working.
The response I got back was “try with another card”.
Not a hello, nor a thank you, that’s when I understood that it was a fake payment page that was there to hack my banking and personal details.
So I had to directly oppose my card. Fortunately, no fraudulent charges were observed, and I have since changed my bank card.
Following this incident, I decided to contact the hotel and inform them of the incident.
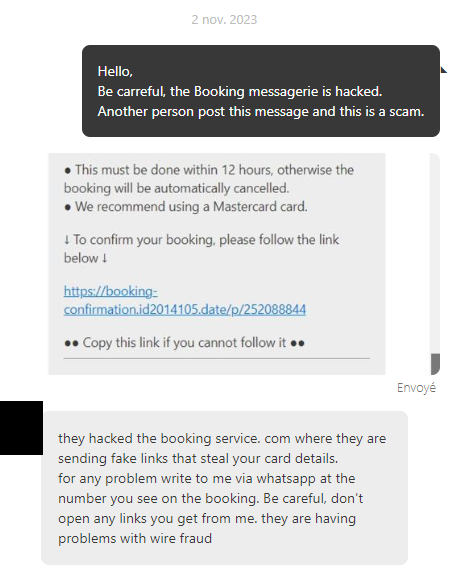
As said previously, the hotel told me that it was the booking.com messaging service that had been hacked.
We will see in the rest of this article how cybercriminals managed to infiltrate Booking’s internal messaging.
Elements that can alert
For someone unfamiliar with cybersecurity, it is quite easy to fall into the trap.
Indeed, the fact that all this happens directly via Booking’s internal messaging system induces a reduction in vigilance on the part of customers and targets.
However, many elements can alert us and give us doubts.
The initial message
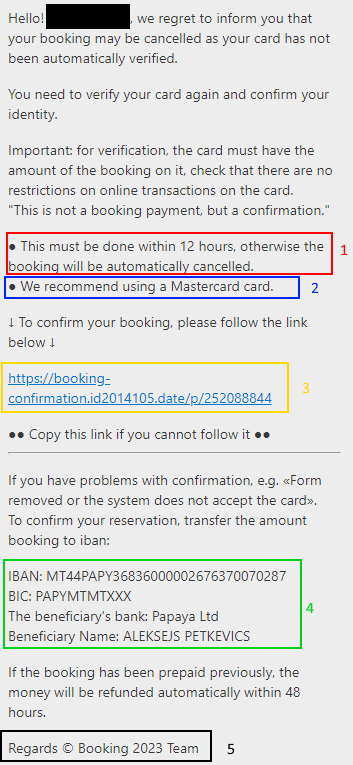
1. « This must be done within 12 hours, otherwise the booking will be automatically cancelled. »
Here, first red flag. In the world of cybercrime, we seek to pressure the victim, with the goal that they act quickly and not ask too many questions or questions.
In reality, 12 hours is far too short a period, and we can legitimately ask questions about the veracity of the message.
2. « We recommand using a Mastercard »
Today, the three leaders in the field of bank cards are VISA, MasterCard and American Express.
As much in Europe the latter is very little used, having to use a MasterCard and not a VISA is very suspect. This is due to the protection of each system being different.
We are therefore here at another point of vigilance.
3. The link
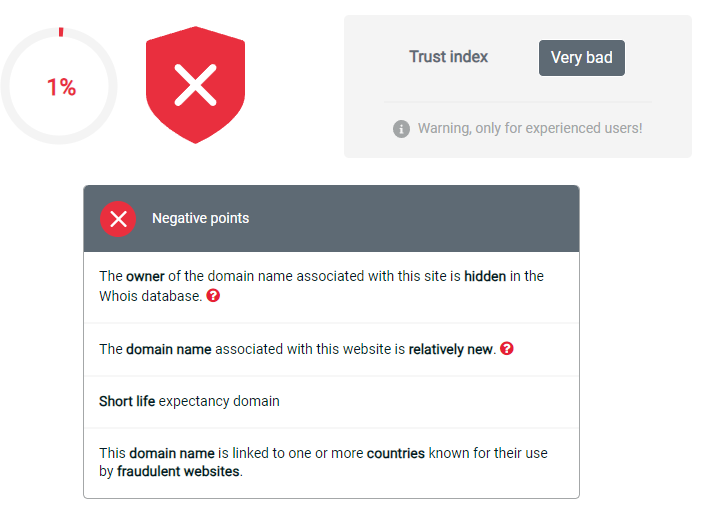
The link “https://booking-confirmation.id2014105.date/p/252088844” today leads to an error, the domain name has been banned by CloudFlare, the host of the domain name.
This link is, for a person not paying attention or not knowing about it, quite close to those of booking.
However, just search the internet for booking-confirmation.id and go to sites like scamdoc to confirm that it is a malicious link.
4. IBAN
This IBAN is more than suspicious, in fact it is clearly the biggest Red Flag of this message.
The hotel will not ask you to make a transfer of the amount you have reserved.
Additionally, if you book in a country, such as England or Spain, the name of the IBAN owner is even more suspicious: ALEKSEJS PETKEVICS.
If we look at the bank attached to the IBAN, Papaya LTD, we realize that it is based in Malta, a tax haven that cannot be extradited in the event of a problem.
This is an electronic money establishment (description coming from their site), it is mainly used by scammers, i.e. people wishing to steal your money.
5. « Regards © Booking 2023 Team »
Remember that it is the hotel that is supposed to send us this message, and we have the Booking.com team as our message signature.
This is therefore an inconsistency, albeit minor, but which confirms suspicions.
The payment page
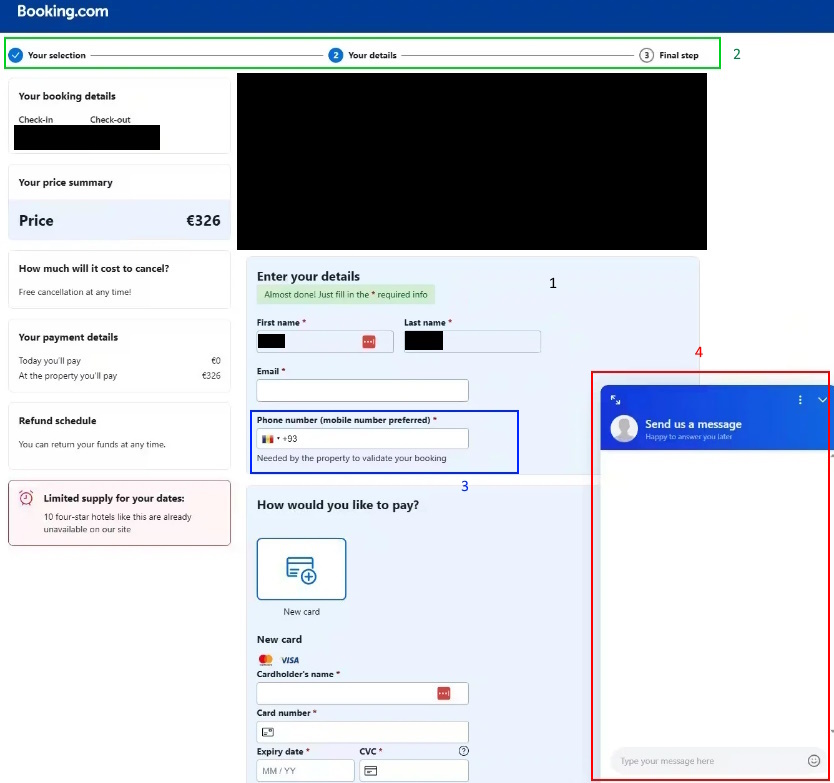
Before pointing out the problem areas of this page, let’s focus on the aspects that may make us think the page is credible.
1. Credible points
If you’re not careful, the page seems quite credible. In fact, it includes many elements provided during our reservation:
- The price is quoted exactly
- Reservation dates
- The name and first name of the person who booked
- The hotel booked
- And the reservation number
2. Language
We remind you that booking.com is a multinational company.
So having a page available only in English is suspect.
3. The “Phone number” field
When you choose France’s +33, know that a foreign flag replaces and is therefore not the tricolor.
You can imagine that a site of the magnitude of Booking cannot afford this error.
4. Chat
We talked about it in the section above, but the chat is certainly an element that reassures, but is also, if poorly managed, an element that can alarm victims.
So, previously, a message was sent saying that it didn’t work.
Five minutes later a person replied to me saying “try with another card”.
In no case will someone from Booking’s after-sales service respond like that, and that’s a huge red flag for me.
How did the cybercriminals succeed?
The modus operandi of this cyberattack is based on Phishing and the installation of Malware.
Hackers target hotels by pretending to make a new reservation or by attacking an existing reservation. They then send a link to the targeted establishments.
This link is actually a fake one, which is used to collect data. The hackers give a plausible reason to justify sending the link, for example a request for additional confirmation of the reservation or a medical justification.
Targeted companies, thinking they are dealing with a legitimate customer, click on the trapped link. But behind this harmless link lies malware that discreetly steals sensitive data.
But it doesn’t stop there, hackers will start a discussion with hotel guests asking them to check their credit cards, and this urgently.
And you know the rest, once the link is clicked, the victims enter their bank details and that’s it for the cybercriminals who will be able to debit money with the victims’ card.
How did Booking.com react?
Booking.com has categorically denied that its system was hacked and instead blamed the messages on flaws in the messaging systems of its partner hotels.
But the hotels concerned complain that this could not have happened on their side.
When a customer realized she had been charged twice, she contacted Booking.com, but was told by call center staff that what she was saying was “simply impossible,” she says.
“I felt hysterical: the call center refused to believe that scammers had sent an email using the Booking.com system. But after two days, I finally received a message from the hotel, again via Booking.com, saying that the system had been hacked, that they knew about it, but that they were not informing their clients.“
“I was told to contact my bank. Eventually, I was refunded by the bank, but only after spending four hours on the phone and having my card digitally replaced. To say I’m unhappy is an understatement,” she says.
On the Booking.com partners hub – an information site for operators using the site – hoteliers are complaining about the problem.
“Booking.com claims someone got our login credentials, but that’s not possible because we have two-factor authentication, and we didn’t receive any text messages.“
“So someone logged into our account, on a new computer, but we received neither the SMS code nor the email ‘Booking.com – new connection to your account’,” complains ‘Hotel de Colegio.
How to protect yourself from this attack when you are a professional?
This attack is based on the principle of phishing/phishing.
An effective method to prevent these types of problems is awareness through a personalized phishing campaign.
A personalized phishing campaign is a cybersecurity awareness method that involves sending simulated phishing emails to a company’s employees.
These emails are designed to look like real phishing emails, to test employees’ ability to identify and report them.
Ziwit creates personalized phishing campaigns that mimic real attacks, based on your business, the applications you use and your employees. These campaigns help educate your employees about phishing risks and prepare them to identify and report potential attacks.
