DDoS amplified via Memcached exposed or when a problem is hiding another one
Have already heard you about GitHub? One of the most popular victims of the denial of service attack. This one aims at returning your unavailable computer server. Nowadays, we consider that there are 100.000 servers allowing to realize this type of attack.
Last week the web experienced its biggest denial of service attack. The most popular of its victims is GitHub, , whose logs show an increase in load equivalent to 1.3Tbps (1300 Gbps).
This attack uses IP spoofing technique by forging packets whose origin IP was modified to match the victim’s one.
It is also combined with a query amplification related to Memcached’s operation , which is able to return 50,000 times more as an answer when the cache is filled, by a simple request of a few bytes.
Indeed Memcached is a cache system that improves the response speed of websites by caching database content. In order to allow IP spoofing, attackers used the UDP protocol.
Study led by HTTPCS :
HTTPCS has conducted a study to determine:
- 1- An estimation of the number of Memcached servers impacted.
- 2- The different contents used to fill the cache..
Methodology :
- 1- Gather IP of Memcached servers via Shodan.
- 2- Extraction of keys and values contained in the cache.
- 3- Detailed analysis of cache content.
Here are the results on more than 5000 Memcached servers :
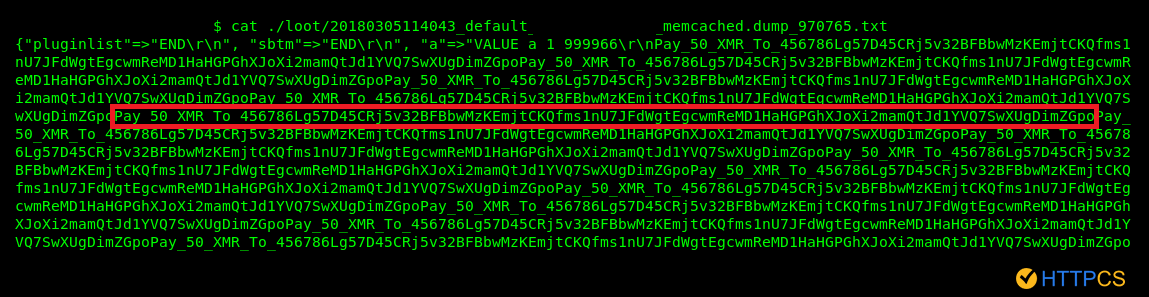
34% contain a ransom note of 50 XMR (~15 000€).
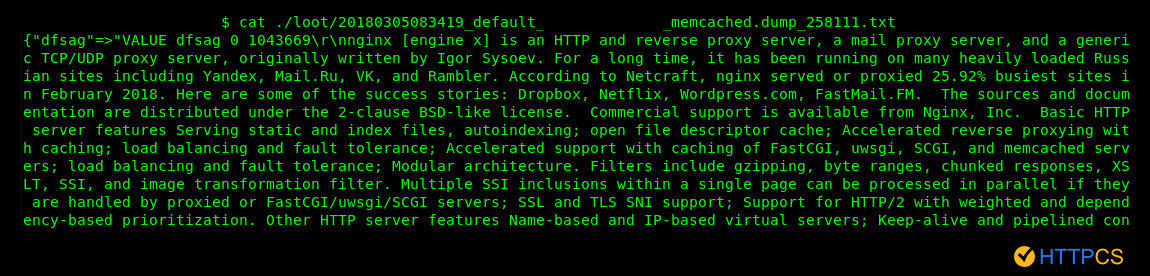
10% contain the full description of Nginx (available here :https://nginx.org/en/).
This reminds us of the exploit posted on Exploit-DB on 05/03 using the content of the Google page
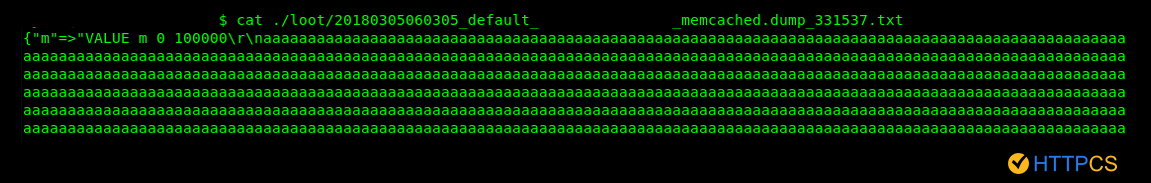
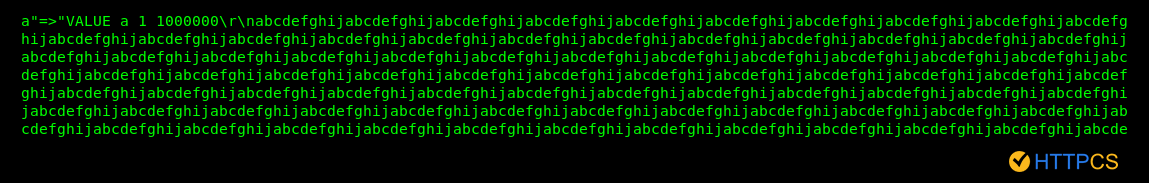
It is estimated that there are nearly 100,000 Memcached servers exposed on the web that can perform this type of attack.
After the attack was highlighted, tips to protect against it were provided by the hosting companies especially to limit the listening of the UDP to the localhost.
Memcached also patched the software so that the UDP only listens to localhost by default.
(https://github.com/Memcachedd/Memcachedd/wiki/ReleaseNotes156).
But the security of Memcached is not limited to this attack. Indeed during the study we highlighted that caches can be not only corrupted and used as a vector of amplified DDOS , but also compromised when they contain sensitive information (which is far from rare.
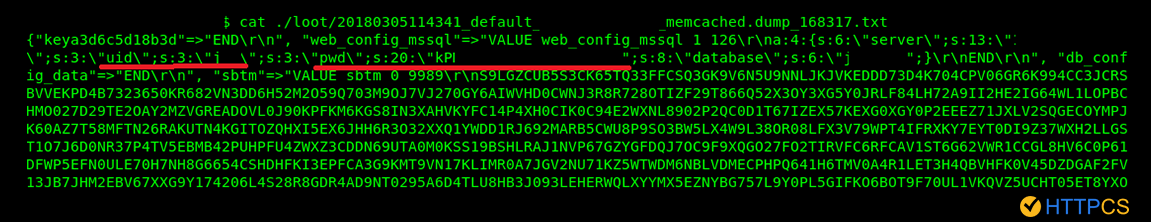
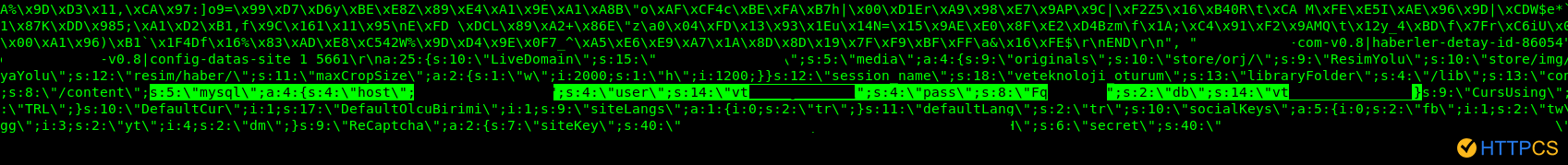
The recommendations of HTTPCS :
The recommendations of HTTPCS are not to expose your Memcached server to the public, neither the UDP nor the TCP. .Because it’s probably not necessary and, if there is a need to share the cache with different servers, this must be done within an infrastructure that is not exposed, and not directly via the Internet
And, without waiting for a patch from the editor or the hosting compagnies’ advice, two simple IPTABLES rules make it possible to limit exposure and thus protect against this type of attacks.
As a result of this study, HTTPCS reminds that the HTTPCS scanner is able of auditing Memcached servers.
