Google suffered largest DDOS attack on record via vulnerability in HTTP/2
A new record was set this year. In August 2023, a new vulnerability was discovered in the HTTP/2 protocol, a web communications protocol used by most modern websites.
This vulnerability, called “HTTP/2 Rapid Reset”, allows denial of service (DDoS) attacks on an unprecedented scale.
A new record was set this year. In August 2023, a new vulnerability was discovered in the HTTP/2 protocol, a web communications protocol used by most modern websites.
This vulnerability, called “HTTP/2 Rapid Reset”, allows denial of service (DDoS) attacks on an unprecedented scale.
Using the Rapid Reset function of the HTTP/2 protocol
The vulnerability, referenced CVE-2023-44487, exploits a weakness in the “connection cancellation” functionality of the HTTP/2 protocol.
This feature allows a client to request the cancellation of a connection before receiving a response from the server.
In an HTTP/2 Rapid Reset attack, the attacker opens a large number of HTTP/2 connections on the target.
These connections are immediately canceled, forcing the server to process requests and generate responses, even though they will never be used.
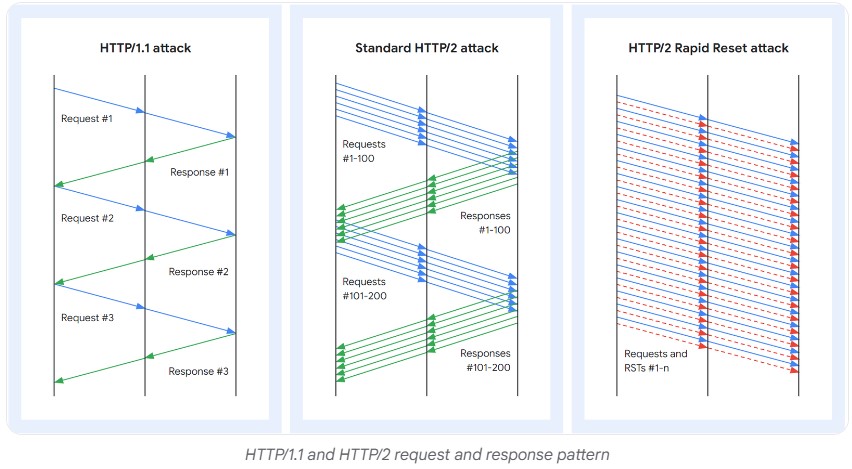
Several requests called “streams” and composed of HEADERS or DATA type frames can be sent simultaneously and out of order on a TCP connection.
DDoS attacks take advantage of the stream multiplexing capability of the HTTP/2 protocol. It is capable of sending multiple HTTP requests in parallel over the same TCP transport connection. One function is particularly targeted, the unilateral reset of flows.
This type of attack can be used to overwhelm a web server and make it inaccessible to legitimate users.
How concurrent streams and RST_STREAM frames can be used to cause a denial of service
HTTP/2 allows clients to open multiple simultaneous streams over a single TCP connection. This helps improve performance, but can also be used to cause a denial of service (DoS).
SETTINGS_MAX_CONCURRENT_STREAMS specifies the concurrent stream limit. This is a setting that allows the server to limit the number of simultaneous streams that a client can open. By default, this value is unlimited, but the protocol designers recommend setting it to 100 or higher.
RST_STREAM frames are frames that allow the client to cancel a previously opened request. This can be useful if the user left the page before the query was completed.
The problem is that when a client sends an RST_STREAM frame, the targeted stream no longer counts toward the maximum concurrent stream limit. This means that the client can immediately open a new flow after canceling a previous flow.
As a result, a malicious client can open and cancel hundreds of streams in a row. This may cause excessive consumption of server resources, potentially leading to a denial of service.
HTTP/2 Rapid Reset attacks have already been used to carry out record DDoS campaigns, reaching throughputs of several terabits per second.
HTTP/2 Attacks affecting web giants
Using this technique, attackers were able to launch DDoS attacks of unprecedented scale against servers hosted by Google, Cloudflare and AWS.
“When an HTTP/2 server is able to process RST_STREAM frames sent by clients and dismantle state quickly enough, these rapid resets are not a problem,” Cloudflare engineers explained in their report.
“Problems start to arise when there is a delay or lag in processing. The client may send so many requests that a backlog of work builds up, causing excessive resource consumption on the server.”
A new record against Google in August 2023
In 2022, the largest DDoS attack was made against Google, Google observed an attack peaking at 46 million requests per second (RPS).
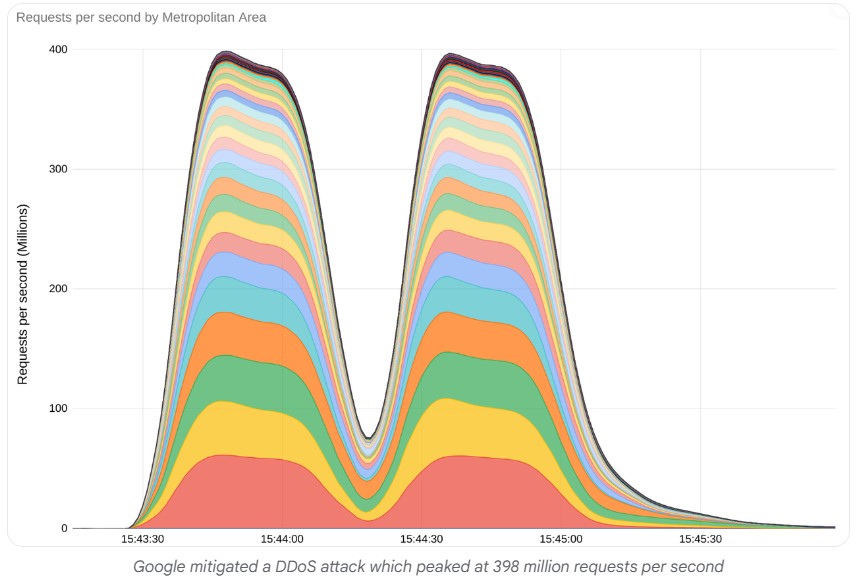
Last August, a new record was broken. Indeed, Google says it has blocked the largest attack ever recorded.
The American firm said it had suffered attack peaks of up to 398 million requests per second.
Google said: “To give an order of magnitude, this two-minute attack generated more queries than the total number of article views Wikipedia reported for the entire month of September 2023.”
At the same time as this attack, two other giants were affected, Cloudflare and Amazon.
On the side of Cloudflare, the latter indicated that it had prevented an attack of 201 million RPS.
While Amazon, with AWS, resisted a 155 million RPS attack.
Protection and remediation against Rapid Reset HTTP/2 DDoS attacks
There are several ways to protect against DDoS attacks coming from HTTP/2 Rapid Reset.
Updating web servers
Web servers are essential elements of a website’s infrastructure. They are responsible for processing user requests and providing them with the requested resources. It is therefore important to keep web servers up to date in order to guarantee their security and performance.
Web server updates are important for several reasons:
To fix vulnerabilities
Web servers are often the target of attacks by hackers. Software updates can fix vulnerabilities, helping to strengthen server security.
To improve performance
Software updates can also improve the performance of web servers. This could be due to code optimization, adding new features, or improving compatibility with new web browsers.
To add new features
Software updates can also add new features to web servers. This can be useful to meet user needs or to comply with new industry standards.
Reduction measures
It is possible to implement mitigation measures to limit the impact of these attacks. These measures include:
Limiting the number of HTTP/2 connections allowed per client
This measure consists of limiting the number of HTTP/2 connections that a client can open on a target. This can be done by configuring the web server or using an application firewall (WAF).
Using an Application Firewall (WAF)
A WAF can be used to block malicious HTTP/2 requests. A WAF can be configured to identify HTTP/2 requests that are opened and then immediately canceled.
For this, we recommend using CloudFilt.
CloudFilt protects against DDoS using a combination of techniques, including:
- IP reputation: CloudFilt maintains the reputation of IP addresses and blocks those known to be associated with DDoS attacks.
- Traffic cleaning: CloudFilt scans traffic for malicious patterns and blocks those that match.
- Rate limiting: CloudFilt limits the amount of traffic that can be sent from a single IP address or subnet.
Implementation of an incident detection and response system (SIEM)
A SIEM can be used to identify Rapid Reset HTTP/2 DDoS attacks. A SIEM can collect data about network traffic and identify patterns of behavior that indicate an attack.
You can use SOC by Ziwit for this.
In fact, the latter is composed of:
- SIEM: Analysis of logs made by the IT structure, applications and other cybersecurity tools.
- EDR (Endpoint Detection and Response): Captures changes to systems, local connections, process execution, memory activities and other operations performed on endpoints.
- NDR (Network Detection and Response): Analyzes network traffic and secures network data internally and externally.
