Cyberwar
Cyberwar is a term used to describe one or more cyberattacks carried out by one country against another, with which it is in conflict. An act of cyberwar can be carried out either by members of a country, but can also be carried out by a terrorist group or a group of hackers supporting a country.
With the expansion of the Internet and information systems containing a wealth of important data, warfare is no longer confined to the field, but now includes a significant proportion of cyberattacks.
Cyberwar is a term used to describe one or more cyberattacks carried out by one country against another, with which it is in conflict. An act of cyberwar can be carried out either by members of a country, but can also be carried out by a terrorist group or a group of hackers supporting a country.
Today, our entire society operates via information systems and the network. All our institutions, whether they concern finance, management or the army, go through digital. Thus, governmental, military or even financial institutions are attractive prey, as are essential companies in the country or the representative.
What is cyberwar?
Acts of cyberwar can be of different genres and can be quite varied.
Sabotage & damage
Sabotage is an act of cyberwarfare that can have far-reaching consequences.
The use of DDOS (Denial of Service) attacks can lead to the inaccessibility of some of a country’s crucial and important resources, such as government sites or communications networks.
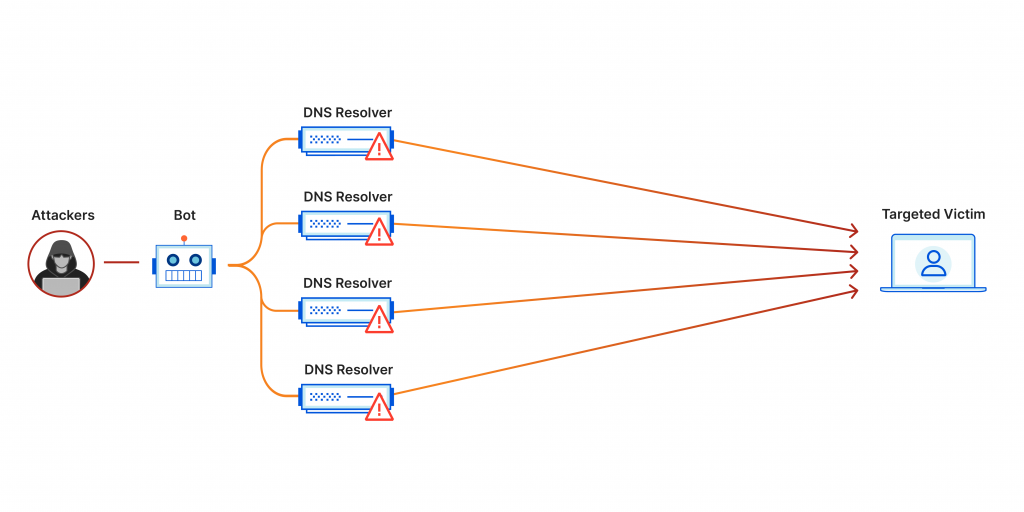
The electrical network can suffer major attacks, which can even lead to a partial power cut.
Computer viruses can wreak havoc, damaging or paralyzing important information systems and causing disruption.
Cyber espionage
Cyber espionage is an integral part of cyberwar and is very important. Indeed, here the goal is not to damage but to recover confidential, essential and crucial information.
The information retrieved can be financial data or business plans for companies.
But when it comes to data recovered from a government, we can find military plans, confidential contracts established between different partners or even private data on the state’s leaders.
Cyber espionage is mainly based on the use of spyware infiltrating the target’s information system or on phishing.
Propaganda
Cyberpropaganda has always been part of warfare, whether it’s the control of information by the enemy state’s population, or the sowing of discredit and doubt in the enemy state’s population.
This is clearly psychological warfare, designed to cast doubt on the people of the enemy state and convince them that their government is the real enemy.
For the propagation of false information to the population of the state at war, cyberpropaganda involves the massive use of social networks, consequent sending of emails or creation of sites discrediting the country.
Regarding the control of information, the state can ban certain sites, applications and networks from its territory, propagate its vision of the facts or even prohibit the possibility of using foreign sites.
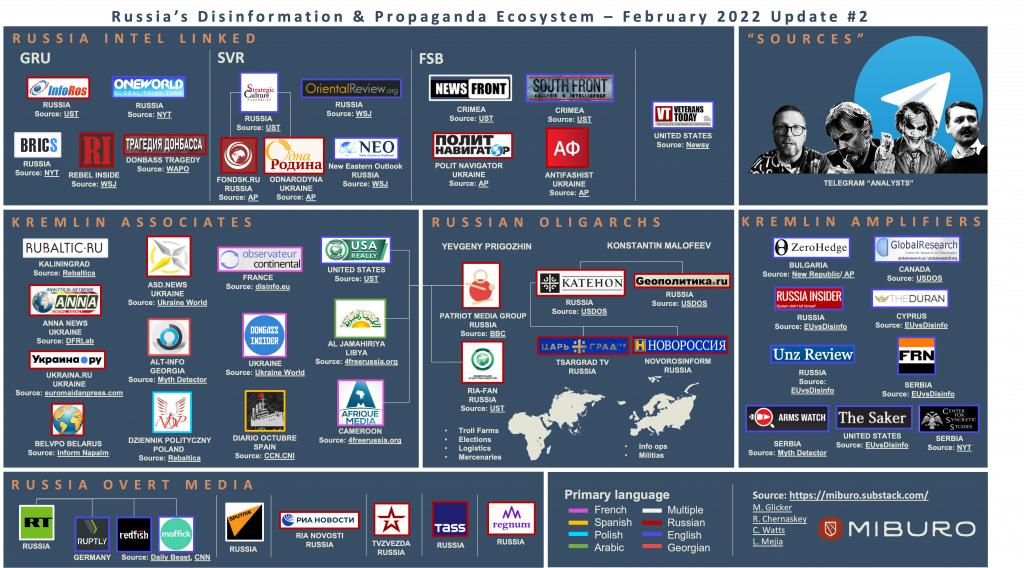
Outstanding examples of acts of cyberwar
Acts of cyberwar are not recent, the advent of digital has led to this kind of process, and this will continue for the next few decades. We will see here different examples of acts considered as “cyberwar”.
2007 – Estonia & Russia
In downtown Tallin, the capital of Estonia, stands a Soviet monument called the “Bronze Soldier”.

The city decided to decentralize this statue and move it out of the city center, as it evoked the suffering of the Second World War for many Estonians.
In 2007, following this decision by the city, a massive cyberattack carried out by DDOS has paralyzed the country. Indeed, the use of more than a million computers, via massive waves of spam and requests through bots, has led to a massive paralysis of the country’s parliamentary, banking, media and government services.
For Estonia, this massive cyberattack caused several tens of millions of euros in economic damage.
In 2008, a Russian-Estonian hacker was arrested and charged with carrying out these attacks on behalf of Russia.
2007 – Israel & Syria
In October 2007, a malware, coming from Israel, paralyzed and rendered inoperative the air defenses of Syria.
2010 – Iran, Israel & USA
In 2010, a virus named Stuxnet, originating in Israel and the USA, attacked Iran’s SCADA systems, a large-scale remote management system for real-time processing of a large number of telemetry readings and remote control of technical installations, and infected the systems of the Natanz and Bouchehr nuclear power plants.
2011 – Afghanistan & USA
In 2011, Nevada Air Force Base was attacked by malware and managed to infect affected drone checkpoints in Afghanistan.
2021 – China & USA
Thanks to a group of Volt Typhoon hackers, Beijing was able to infiltrate “critical infrastructure”. This “affected critical infrastructure networks in the United States” with techniques applicable “worldwide”.
The war in Ukraine: the perfect example
The cyberwar between Russia and Ukraine began long before the start of the armed conflict on the ground.
For example, in 2016, the Fancy Bear hacker group, affiliated with the intelligence service of Russia, used a spyware named X-Agent which attacked Ukrainian artillery and caused the destruction of more than 80% of the Howtizers D-30 from Ukraine.
Everything has escalated since the start of hostilities between the two countries. Many techniques are employed, and land warfare has become hybrid warfare.
The Russians use many cyberwar techniques such as the hacking of the Ka-Sat communication satellite, the distribution of malware which aims to destroy all the data of their targets, or even massive propaganda and disinformation operations.
For propaganda operations, hackers can use defacement attacks, this kind of cyberattack consists of hacking a website in order to modify pages, most often the home page.
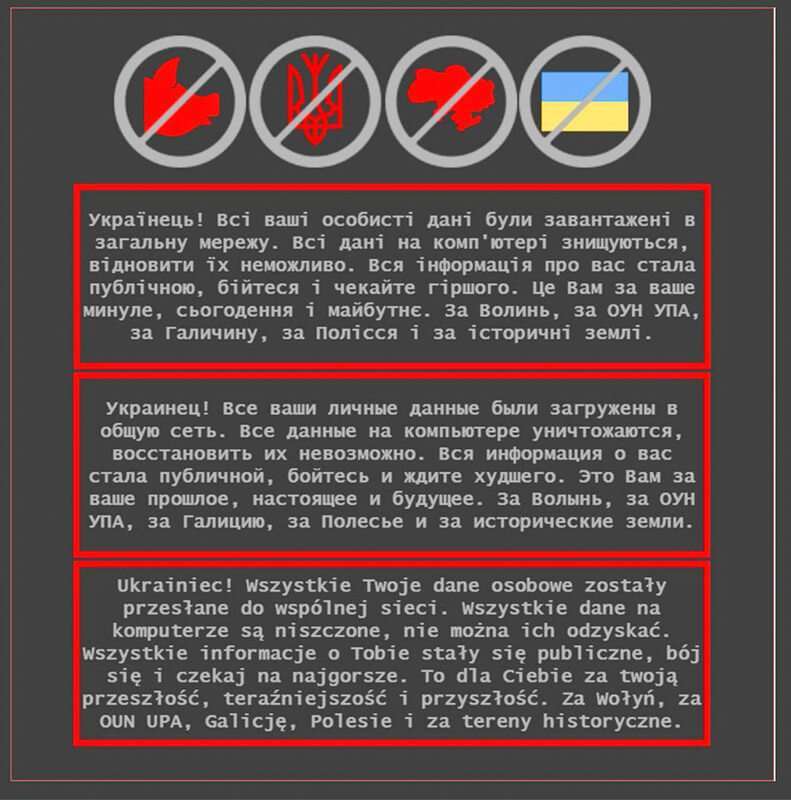
The same applies to Ukraine. An American combatant in Ukraine, a communications specialist, intercepts sensitive Russian communications.
“We use many techniques to intercept exchanges, sometimes using cyber tools on computers and smartphones. We look for targets and we manage to trap them, to infiltrate their network. We trap Russian phones. Some people have been monitored for months, then we analyze their movements to identify strategic points.
We also use StingRay (an IMSI-catcher), a kind of surveillance box that mimics a cell tower to force phones to connect to it. Sometimes military radio communications are intercepted simply by picking up the frequency.”
Numerama
How should countries or organizations protect themselves against cyberwar ?
There are more acts of cyberwar than we think. Indeed, these remain confidential and are only very rarely revealed to the general public.
The use of new technologies offers growing opportunities for hackers to attack governments and state services.
Therefore, it is crucial to have means of cyber defense. There are several ways to do this :
- The need to train employees to fight and protect themselves against cyber threats in order to avoid risks as much as possible.
- Against phishing attacks : carry out a personalized phishing campaign to raise awareness and highlight weak points.
- Organize “life-size” exercises, called “cyber wargame” exercises. They make it possible, in the face of a major cyberattack, to test the reactions of governments. These exercises identify possible points for improvement, flaws in the defense of information systems, boost cooperation between stakeholders and learn how to quickly and effectively protect critical infrastructure for the proper functioning of the state.
- Perform pentest. Indeed, the pentest is a computer security assessment method that simulates a computer attack to identify the vulnerabilities and weak points of a computer system, a web application or a network.
- The importance of using a firewall, but also a vulnerability scanner, an essential solution for detecting all the flaws in an information system.
- Recruit hackers to initiate and train employees, but also to improve IS defense.
Today, all states are training in cyberwarfare and cyberdefense. Governments have discovered the importance of maximizing the security of information systems and infrastructures to protect confidential and classified data, to secure services vital to the smooth running of the state and to protect the population.
