File Integrity Monitoring
File Integrity Monitoring (FIM) is a technology that is becoming increasingly used in cybersecurity today. In this blog post, we are going to tell you everything about this tool.
File Integrity Monitoring (FIM) is a technology that is becoming increasingly used in cybersecurity today. In this blog post, we are going to tell you everything about this tool.
What is File Integrity Monitoring?
File Integrity Monitoring is a tool with the ability to monitor and detect file changes that may reveal a cyberattack.
This is to make a difference between the existing files before and after a scan and their content. If a change is detected, an alert is sent to notify the responsible person.
Computer security people cannot check each file one by one if changes have appeared. This would obviously take too long. But it is nevertheless important to check whether the files of a system or a site have not undergone unwanted and worrying modifications.
A hacker can easily modify a resource or a script and thus compromise an entire site. It is to detect this kind of modifications that File Integrity Monitoring software was created.
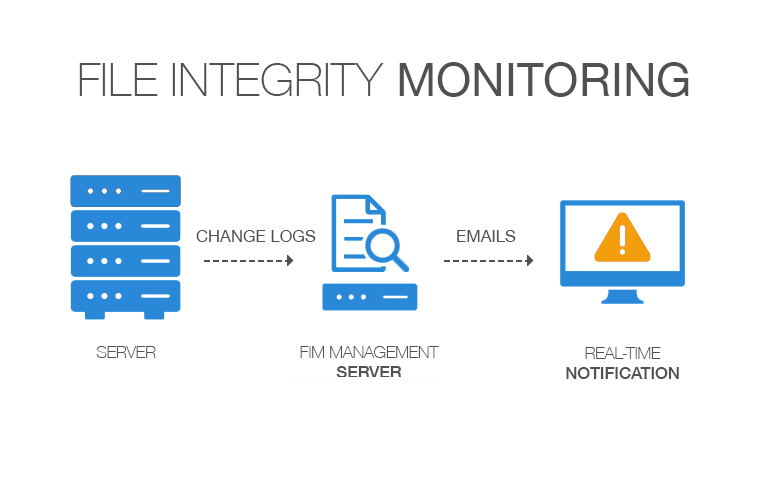
The Importance of File Integrity Monitoring
The use of a File Integrity Monitoring solution has now become essential. Whether for cybersecurity, or for compliance with standards and requirements.
The FIM at the service of Cybersecurity
In 2020, there are 1.78 billion websites. Every day, 800,000 sites are created. These data show the importance of digital today. With the explosion of the internet, computer security is becoming a real issue.
Thanks to the FIM solution, administrators and managers can be alerted when their site undergoes a modification.
So, if the modification comes from a person in charge of the site, no problem.
However, if none of the people in charge of the site is behind the change, then it is crucial to check if the site has not been attacked, or if it does not contain a security flaw exploited by a hacker (for this, you can opt for a vulnerability scanner which will detect all security flaws).
Involuntary changes
Often, file changes are inadvertently made by a company employee.
Sometimes these changes can be minimal and go unnoticed. Other times, they can create security vulnerabilities or lead to possible malfunctions.
File integrity monitoring simplifies investigation by helping you focus on the erroneous change, so it can be fixed.
The requirements of the standards
Compliance with governmental or industrial requirements is essential today in the field of computer security.
Let’s take the example of PCI DSS compliance (Payment Card Industry Data Security Standard) It is a set of security standards for bank card data. Any organization processing payment cardholder data is required to comply.
Thus, in sections 10.5.5 and 11.5 of the PCI DSS, it is required to monitor the integrity of files, hence the need to use an FIM.

How does File Integrity Monitoring work?
A File Integrity Monitoring has a fairly simple operation. It can be summarized in 6 steps :
1. Definition
For FIM software to work perfectly, it is imperative to define the environment, what should be monitored by the tool and what types of changes should be detected.
2. Establishing a baseline
Here you can find two different techniques :
- Either, we establish reference files, which will serve as a comparison thereafter.
- Either every day, a robot scans and considers that the scan of the day is the new reference
3. Hashing Files
During the operation of the software, the files will be hashed.
Any modification made to the files, whether authorized or not, will also modify the hash value of the file, which will make it easier to detect updates and changes to the files.
4. File monitoring and comparison
Thanks to file hashing, it is quick and easy to compare files to detect “anomalous” changes.
5. Alerts
Simply and effectively, users configured to receive alerts will be notified of changes.
Good File Integrity Monitoring software has the ability to only send alerts of certain types, such as script changes, internal errors, or unsecured resources.
6. Reports and results
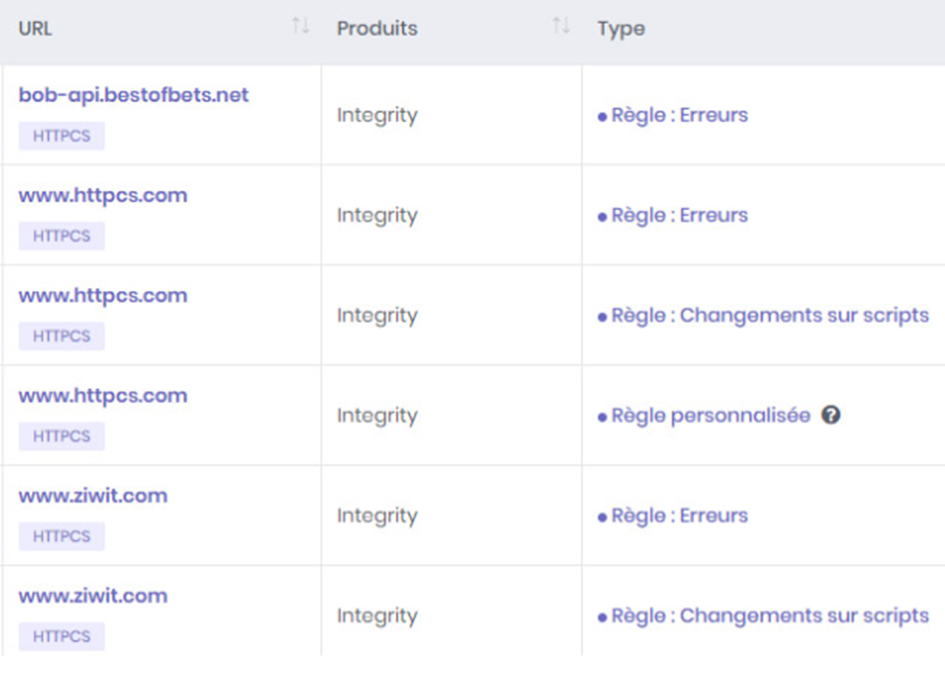
Users can find in their FIM software, the results of the analyzes with the possibility of sorting according to the types, as seen previously.
Add to this also the possibility of exporting the analyzes in the form of a report.
Choose a Good File Integrity Monitoring
As you will have understood, this tool is very important for the cybersecurity of a site. This is why it is essential to choose a quality service provider offering a complete and efficient solution.
A quality File Integrity Monitoring must meet certain requirements, these obviously depend on the needs of the company, but generally we find :
- The possibility of integration with APIs.
- Effectiveness of analysis and detection of software changes.
- The reduction of “noise”, thus avoiding the pollution of “false” changes in the results. This avoids a waste of time and money for employees within the company.
- The means of alert in the event of changes.
- The possibility of exporting the results.
- The possibility of filtering the results to better navigate.
- A qualitative after-sales service available in case of problems.
- The existence of other tools such as a vulnerability scanner, a complementary solution to File Integrity Monitoring.
ZIWIT, via its HTTPCS Integrity product, has implemented File Integrity Monitoring software that meets the needs of companies.
In addition to performing advanced file monitoring, this solution allows you to :
- Check the web reputation of your site’s internal or external resources.
- Detect the technologies used, including those with a deprecated version or having a new version available.
- Check page load times.
- Detect expired SSL certificates and DNS domains.

