File sharing and transfer software: the new target of hackers
File sharing software, which has become essential in the life of a company today, represents a prime target. In this article, we will see why and which software suffered attacks.
With the continuous improvement of Internet connections, the explosion of the digital age and the need to share documents and other files – files that are becoming increasingly large – it was necessary to create software and websites that would enable the transfer of large, heavy files, which could not be shared by e-mail because they were too large.
Today, it has become natural to use this kind of software and sites to share our files. We can cite, as examples WeTransfer, Download.gg, Dropbox or even GrosFichiers, these softwares are used by many Internet users, individuals and companies.
Professionals, who need to transfer confidential files with sensitive data, use different software.
They don’t use WeTransfer or Dropbox, but rather software that encrypts files and uses secure transfer protocols, with automation or analysis options.
There are many such programs on the Internet, including MOVEit, Fortra’s GoAnywhere MFT, CyberDuck, FileZilla and GlobalScape Managed File Transfer. Today, such software represents an indispensable need for businesses.
Why are hackers so interested in file-sharing software?
Malicious hackers often seek to make money from vulnerable companies by using and exploiting loopholes, or exploits.
Hackers do not keep information to themselves, two scenarios can generally happen :
- The 1st case involves a ransom demand, an exchange between money and stolen data.
- The 2nd case is more damaging for the customers of companies that have been hacked, this is the case of the resale of confidential or personal information on the Dark Web.
So why hack file sharing software rather than normal software ?
Simply for information !
Simply put, the more confidential and personal information you hold, the more money hackers can make.
So it’s only logical that file-sharing software, which has become an essential part of corporate life, should be a prime target.
And as this type of software proliferates, hackers use every possible means to extract as much information and documents as possible.
File-sharing hacks and data theft increasingly common
In recent months, more and more file-sharing software has suffered intrusions and data theft by malicious parties.
Each of these hacks has varying financial consequences, as well as concerns about data confidentiality.
We are going to see some of these cases, including the most recent which took place at the beginning of June 2023, and which concerned the MOVEit transfer software.
Dropbox

Do you know Dropbox ? One of the largest storage sites but also an online file sharing tool via the Cloud, a competitor to Google Drive (we will come to this shortly after).
Well, in October 2022, Dropbox was the target of a simple phishing campaign that resulted in the leak of 130 GitHub repositories. Thanks to this phishing campaign, the hackers were able to gain access to GitHub repositories.
These repositories included copies of third-party libraries, internal prototypes and various configuration files used by the security team. Dropbox also mentions API keys used by its developers, among the items accessed by the malicious individuals.
The leak includes several thousand names and e-mail addresses of current and former Dropbox employees and customers.
Dropbox was able to react very quickly and then expressed itself on the networks : “We are sorry to have failed and we apologize for any inconvenience.”
How could this have been avoided? Well, simply by raising employee awareness of phishing campaigns.
Google Drive

Let’s continue with the giant ofcloud storage and file sharing, Google Drive.
In August 2020, a flaw in the Californian giant’s sharing service has been discovered.
The problem in our case was file versioning. Let’s explain the vulnerability with a live example.
- Let’s say I put a photo of a cat on Google Drive, with the extension .jpg, i.e. “cat.jpg” – so far so good.
- Now I decide to share it with you through Google Drive, so you receive this photo of a cat, with a preview of a photo of a cat.
- After sharing it with you, I decide to change the file and replace it with an executable .exe file, but I keep the same name, so we have “cat.jpg.exe”.
- But you don’t know it, because on your side, you still have a thumbnail of a cat and a file called “cat.jpg”.
- And if you decide to download this file, you’ll be downloading the executable and not the original photo.
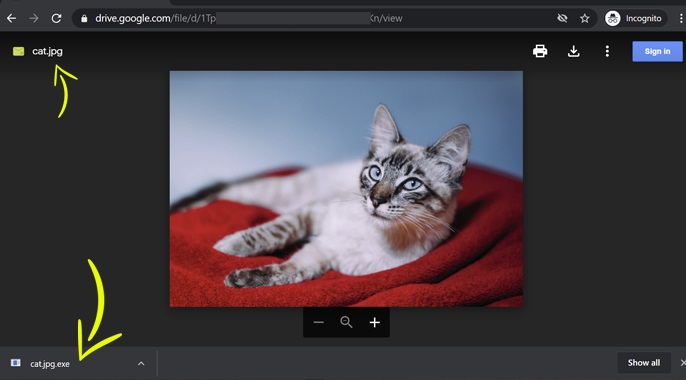
We can therefore, thanks to this method, transform any innocent file into a possible virus. Google Drive does not check for new file versions or if the extension has changed.
This vulnerability, which was brought to everyone’s attention, has since been corrected.
Accellion

Accellion, now known as Kiteworks, specializes in the communication of confidential and sensitive content. It offers a range of solutions, including e-mail services, forms and file sharing and transfer.
In December 2020, Accellion’s file transfer product, File Transfer Appliance FTA, fell victim to a 0-Day exploit; this flaw was patched on December 23 of the same year.
In January 2021, 3 further vulnerabilities were detected and patched during February 2021, including an SQL injection enabling a Web Shell to be used to execute commands and extract data.
On February 16, 2021, the 4 vulnerabilities were assigned Common Vulnerabilities and Exposures (CVE) codes ranging from 2021-27101 to 2021-27104.
Of the 300 large customers using the FTA solution, 25 of them were reached, including Qualys, Stanford Medicine, Shell Oil Company, the Australian Securities and Investments Commission, and the Reserve Bank of New Zealand.
A lot of data was stolen including :
- Social security numbers
- Identification numbers
- Passport images
- Confidential financial informations
- Driving license data
- Emails
In January 2022, Accellion offered to pay $8.1 million in connection with these data thefts. The proposed settlement will resolve all legal actions against Accellion only. It does not take into account legal actions against customers affected by the data thefts.
Accellion was an aging solution with 20 years of age and being replaced from April 2021 by Kiteworks, the company should have equipped itself with a vulnerability scanner, this would probably have avoided these data thefts.
GoAnywhere MFT

Fortra’s GoAnywhere MFT is an encrypted file transfer solution for exchanging data between systems, employees, customers, and partners, it is one of the largest destination file transfer solutions for professionals.
It provides a single point of control with security settings, detailed audit trails and reports.
Data transfers are secured by using protocols for FTP servers (FTPS, SFTP and SCP) and Web servers (HTTPS and AS2). It supports popular encryption protocols and offers a NIST-certified FIPS 140-2 validated encryption module.
In February 2023, a “0-Day” vulnerability was exploited. Fortra explained that the flaw was a remote code injection requiring access to the administration console to be fully exploited.
Fortra said it had “temporarily implemented a service outage in response”. The company warned that if an admin console is exposed, “it is strongly recommended that you partner with our customer support team to implement appropriate access controls to limit trusted sources“.
Rapid7 advises GoAnywhere MFT customers to review all administrators and watch for suspicious names.
FileZen

FileZen from Soliton, a Japanese company, allows you to upload and download files on the web browser. This is a type of appliance that can be easily installed.
FileZen suffered data theft following the discovery of two flaws in its system.
A nearby source with the investigation in Japan said hackers appear to have found a combination of two FileZen security flaws, which they began exploiting earlier in January 2021.
Threat actors used CVE 2020-5639 and 2021-20655, two vulnerabilities that were patched in December 2020 and February 2021, respectively, to infiltrate FileZen’s systems.
The first vulnerability allowed hackers to download malicious files onto the device, while the second allowed them to execute operating system commands with elevated privileges.
Highly sensitive data was stolen with the main target being the Japanese Prime Minister’s Office.
Like Accellion, a vulnerability scanner would have allowed Soliton to detect flaws before hackers exploited them.
MOVEit

MOVEit is one of the market leaders in file transfer software.
This software, developed by Ipswitch and owned by Progress Software, suffered a major cyber-attack in early June 2023, targeting data and then demanding ransom.
The group of hackers named Cl0p launched an extensive campaign of cyberattacks by exploiting the CVE-2023-34262 vulnerability, which was unknown at the time.
The company behind MOVEit has strongly recommended that all customers disable internet access for their MOVEit Transfer system.
More than 3,000 organizations use this file transfer system. The companies using this software are numerous and very reputable. We find, among others, the BBC group, airlines companies such as British Airways or Aer Lingus, the province of Nova Scotia in Canada, many large American banks, or the American Department of Homeland Security.
Extreme Networks, a world leader in LAN access infrastructure solutions for professionals, was also affected. They state: “We have recently learned that our instance of the Progress Software MOVEit Transfer tool has been affected by a malicious act. We took immediate action by enforcing our security protocols and circumscribing the affected areas. Our investigation is ongoing and if any customer information is found to have been affected, we will communicate directly with those customers and disclose all relevant information.”
The BBC revealed what kind of information were stolen :
- Identification numbers
- Dates of birth
- Personal mailing addresses
- Email addresses
- Social security numbers
Progress Software acted quickly, and offered a fix within 24 hours, which the company urgently recommends installing. The official cybersecurity agency CISA recommends that American organizations apply these updates.

File transfer software and tools are full of personal and confidential information.
For hackers and ransomware seekers, these programs can represent a veritable goldmine. In recent years, many of these programs have been targeted by malicious individuals.
That’s why it’s essential that this software is optimally protected and secured by cyber-defense solutions such as vulnerability scanners or Cyber Threat Intelligence tools.
