Notaries – A prime target for hackers
In the world of notaries, cyberattacks have become frequent and notary offices are a prime target for hackers.
In recent years, working methods have changed, and the COVID-19 pandemic has accelerated these changes. Workplaces are becoming increasingly digitalized. But this exponential use of digital is leading to a quantum in cybercrime.
In the notary’s world, cyberattacks have become frequent and notary’s offices are a prime target for hackers.
In addition, the regulatory framework of notarial offices is changing. For example, since 2015, the state has required that all sums over €3,000 collected by notaries will be sent by bank transfer, thus requiring an exchange of bank details by email.
Whether it is to defraud clients or notary firms themselves, cybercriminals use several different techniques to always get richer at the expense of others.
Attacks targeting notaries
Ransomware or data thieves
Ransomware attacks involve the installation of malicious software on a computer. This software will encrypt the data present, and the hackers will demand payment of a ransom to decrypt the data.
Data may not necessarily be encrypted, but rather recovered and resold on Dark Web sites.
Today, there are solutions for constantly monitoring the Web, the Deep Web and the Dark Web, with the aim of gathering information about a company and alert impacted teams in real time, this is called Cyber Threat Intelligence.
Defacement attacks
Defacement cyberattacks directly target sites belonging to notary offices.
This type of attack aims to make the site unusable, with the objective of stealing data or making a ransom demand.
According to the cybermalveillance.gouv.fr site: “Website defacement is the alteration by a hacker of the appearance of a website, which may become uniformly black, white or include messages, images, logos or videos unrelated to the original purpose of the site […] Defacement is the visible sign that a website has been attacked and that the attacker has obtained the rights allowing him to modify its content. During the attack, the site is often no longer usable, which can lead to direct losses in revenue and productivity. In addition, […] the attacker was able to take control of the server, and therefore potentially access sensitive data”.
This king of attack damages the reputation of the targeted company, proving that its information system is clearly unprotected, but it can also jeopardize its data, including that of its customers, whether personal, commercial or financial.
Hackers manage to infiltrate by exploiting an unpatched flaw in a website. This is why it is essential to arm yourself with a vulnerability scanner to detect the slightest flaw present within your computer system.
Correspondence attacks
Here, cybercriminals don’t seek to infiltrate the notary’s website, they seek to retrieve information directly from online accounts, such as e-mail or file transfer sites.
E-mail accounts, for example, represent a real goldmine for hackers, as they often contain a wealth of confidential, personal and even financial information. This can include, for example, proof of residence, bank details, addresses, identity documents, and property titles.
Jean-Luc Girot, president of Magic Notary announces : “with this kind of informations, cybercriminals can, for example, usurp a person’s identity, open a bank account in their name and obtain consumer credit”.
Email hijacking and RIB fraud
In recent years, one fraud has become very popular with notaries and their clients: the RIB change fraud.
There are still two ways to proceed :
- The first: Hacking into a client’s mailbox, or a notary ‘s mailbox for example. The hackers then intercept the emails and replace the beneficiary’s bank details with their own bank details.
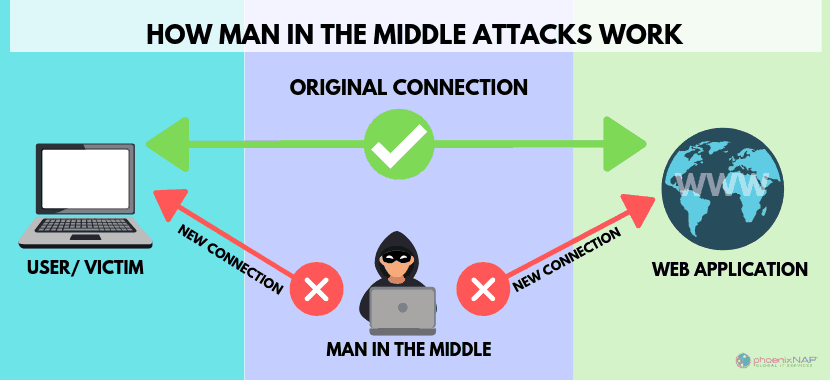
- The second is called “Man in the Middle”. The fraudsters intercept the emails exchanges between the customer and the notary, and are then able to modify the attachments including the bank details. Hackers rely on high-performance bots, which can scan and detect emails looking for RIBs to replace them.
Phishing attacks
Phishing attacks are very present these days. In 2022, this type of attack increased by 61%. This technique is actually quite simple. It simply consists of usurping the identity of a person, company or entity to deceive the email’s recipient.
Once the recipient is confident, he will either open an attachment containing a malicious file, but the mailboxes begin to detect problematic attachments, or click on a fraudulent link and will enter this personal and especially financial information such as the number bank card.
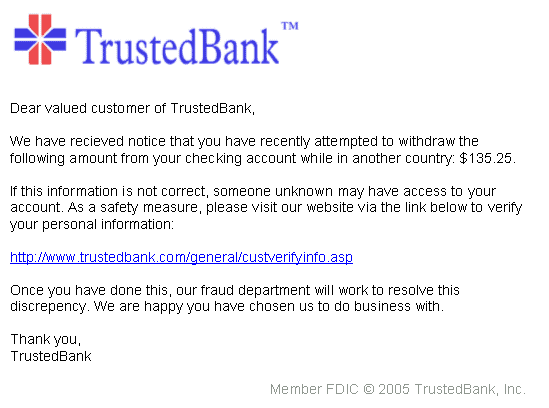
This kind of attack can also affect members of a company. Indeed, notaries can receive, for example, an email from the “government” or a bank and asks the employee to enter confidential data.
This is why it is essential to raise awareness among employees via a personalized phishing campaign.
What should notary firms do?
Whether it is for prevention, or after the damage has been done, good cybersecurity practices and reflexes are essential.
Prevention
Better safe than sorry, right?
With this in mind, we are going to draw up a list of good practices for you to avoid the risk of cyberattack as much as possible :
- Have security flaw detection software like a vulnerability scanner.
- Regularly update all the software you use, whether it is messaging, file sharing software, search browsers or software dedicated to notaries such as Fiducial or GenApi.
- Use Cyber Threat Intelligence software. This kind of solutions will allow you to be alerted in case of your data’s detection on the Dark Web.
- Reinforce your passwords and never put the same one for the different uses you have.
- Make yourself and your employees aware of the risks of cyberattacks and best practices. For this, you can go through approved training organizations in IT Security such as Ziwit.
- Choose your software carefully. They must be renowned for their protection and for the data’s security that they offer.
- Train your associates and colleagues on best practices for exchanging emails. Always check the recipients of your emails and avoid transmitting confidential information as much as possible. If necessary, program a personalized Phishing campaign with an expert company in computer security.
- Back up your data frequently on external, highly secure servers.
- Separate personal and professional uses. Do not forward your work e-mail messages to e-mail services used for personal purposes. Do not host professional data on your personal equipment (USB key, telephone, etc.). Avoid connecting personal removable media to company computers.
- Ask professionals to perform a Pentest, or intrusion test, of your information system to test it. Pentest is a computer security assessment method that simulates a computer attack to identify vulnerabilities and weak points in a computer system, web application or network.

Reaction
If you’ve suffered a cyberattack, don’t panic. We will take you through the steps you need to take to react as it should. To begin with, we strongly advise you to go through professionals and to call on an Incident Response Team which is an emergency unit in case of cyberattack.
Then, here is a list of measures that we advise you to take :
- If it is an affected machine, disconnect it from the Internet and from all possible networks, but ABOVE ALL, do not turn it off !
- Gather as much evidence as possible so that you can file a complaint.
- Retain hard drives or make a full copy of data before it’s too late.
- Identify anything that has been destroyed or copied.
- Of course contact your server hosting company to take the appropriate measures.
- Once the threat has been averted and the machine is secured, correct the flaw. For this, we advise you to go through professionals.
What are the consequences for notary firms?
The consequences of cyberattacks are numerous, it can be financial, reputational or even legal.
As far as the financial consequences are concerned, the average cost of a cyberattack for an SME is between €20,000 and €50,000. For large companies, the figure is several hundred thousand euros.
In reputational terms this can be a real disaster. A company that has suffered a cyberattack, and even more so with a proven data leak, will be seen as vulnerable, lacking sufficient IT security and data protection for its customers.
Since 2016, companies have been obliged to comply with the guidelines of the General Data Protection Regulation (GDPR). Companies are required to adequately protect the informations provided by customers. Data leaks and non-compliance with this European law expose the company to heavy penalties of up to 20 million euros or 4% of annual turnover. Also, be aware that the courts will not be in your favor if you expose your customer’s data to cybercriminals.

What to conclude ?
Attacks affecting companies processing confidential and banking data have become increasingly frequent in recent years, leading to the creation, in the United States, of a service called the IC3 or Internet Crime Complaint Center which aims to deal cybercrime complaints.
Notary companies have now become a major target for hackers because they hold a lot of confidential and financial information such as bank details. This data is often exchanged simply by email and can be easily intercepted and diverted.
It is therefore becoming mandatory today for notary firms to have optimal IT security by having solutions to detect security breaches but also data leaks.
In addition, we recommend performing Pentest type audits on the whole computer system. These simulate attacks in real conditions and use advanced techniques to test the resistance of the system.
