Our 10 cybersecurity recommendations
Cyber attacks cost French organizations two billion euros in 2022. Ransom payments accounted for 40% of this amount.
Cybersecurity has therefore become an essential part of corporate life.
In this blog post, we are going to give you 10 recommendations in the field of cybersecurity.
Cyber attacks cost French organizations two billion euros in 2022. Ransom payments accounted for 40% of this amount.
Cybersecurity has therefore become an essential part of corporate life.
In this blog post, we are going to give you 10 recommendations in the field of cybersecurity.
Strengthen authentication
Let’s start with the obvious, let’s talk about authentication and passwords.
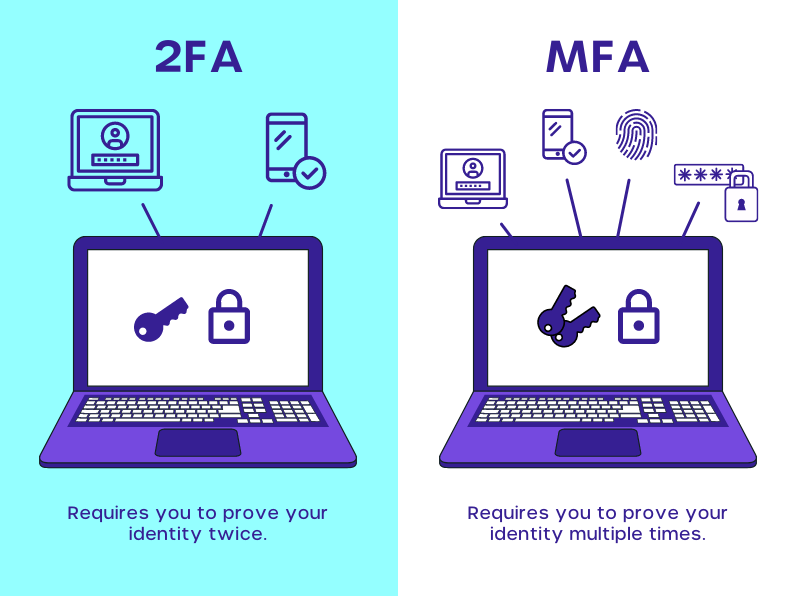
Implementing strong double authentication makes it possible to limit information leaks by hacking a password.
The two authentication factors are :
- A password, unlock pattern or signature
- A material medium (smart card, USB token, magnetic card, RFID) or at least another code received by another channel.
Additionally, passwords must be unique, involving many different characters including uppercase, lowercase, special characters, and numbers. They must not echo any real word surrounding the collaborator.
For example, an employee named Mr. Doe, born July 10, 1990 and working for Example in France, should not have a word like “doe10071990” or “example-doe”. A good password would be random, like “Hr7k$ppU9? “.
Do not mix personal and professional
It is important to separate personal and professional uses.
An employee should never use their personal tools such as their mobile phone or computer to work.
Protection of personal tools is not the same as protection of professional tools.
What’s more, with the rise of telecommuting, we strongly recommend providing employees with a laptop that’s only for work and not for personal use.
Update software
Companies use a lot of software to work, such as management, desktop publishing, accounting, planning and communication software.
Occasionally, however, such software is subject to cyber-attack, or publishers detect security vulnerabilities.
Software publishers are quick to offer updates to their solutions to correct these breaches.
Updating third-party software makes it possible to avoid exploiting the security vulnerabilities detected in these solutions as much as possible.
Beware of emails
According to the website of the French Ministry of the Economy: « Phishing consists in obtaining from the recipient of an email, which appears legitimate, that he transmits his bank details or his login credentials to financial services, in order to steal money from him. […] This type of practice can also be used in targeted phishing attacks aimed at obtaining from an employee their access credentials to the professional networks to which they have access. To reinforce its credibility, the fraudulent email will not hesitate to use logos and graphic charters of the most well-known administrations or companies. »
According to a French government report, 60% of information system breaches come from phishing techniques.
This kind of technique can be very effective for someone who is not paying attention or is not used to cyber malicious acts.
It is therefore necessary to carry out personalized Phishing campaigns. Carrying out a fictitious personalized phishing campaign to raise employee awareness of computer security is a very effective training strategy.

Back up
We advise you to make regular backups on offline devices.
Cold storage solutions make it possible to protect backups from an infection of information systems and to preserve critical data.
This kind of backup makes it possible, in the event of a data leak and a ransom demand, to avoid paying hackers.
This also allows, if an information system becomes unavailable, not to lose the data.
Oversee IT security
It is essential to set up a cybersecurity supervision system. An integrity checker, such as HTTPCS Integrity, makes it possible to detect a change within the code of the site and therefore to detect a possible compromise.
IT security managers should develop event logs. Thus, if one of the various entry points suffers a compromise via an incident, it is much easier to react and thus save time in understanding the incident.
Examples include VPN entry points, virtual desktops and domain controllers.
Protect yourself with cybersecurity software
We have already advised you to use an integrity checker to detect changes and possible compromises.
Obviously, you need to protect your devices with firewalls and anti-viruses, but if you have websites or web applications, you need to protect them with other software.
Today, it’s essential to protect your site with a vulnerability scanner, such as HTTPCS Security. These tools can detect security flaws before they are exploited by cybercriminals.
We also recommend Cyber Threat Intelligence software. This type of software can detect data leaks.
HTTPCS CyberVigilance constantly monitors web, deep web and dark web networks to collect information (documents, data leaks, sensitive information, security breaches, etc.) that concerns your company, and alerts affected teams in real time.
Train employees
Employee training and awareness-raising is an essential element of corporate IT security.
Awareness-raising classes make all employees aware of the challenges, threats and risks of IT security. They also provide all the protection methods that make the difference in the event of a cyber attack.
Ziwit’s Qualiopi-certified cyber-experts provide training tailored to your company’s needs. Find out more about Ziwit training courses.
Audit its Information System
Cybersecurity audits enable you to monitor your organization’s security, correct any vulnerabilities that may have been discovered, carry out manual Pentests and continually improve the IT security of your information system.
We strongly recommend that you carry out an annual intrusion test of your information system with a PASSI-certified organization, such as Ziwit.

Pentesting by the Ziwit team enables us to identify vulnerabilities in a computer system in the same way as hackers.
Once the penetration test has been carried out, certification is issued attesting to the integrity, security and reliability of your IT system.
Have a crisis plan in case of a cyberattack
Finally, we recommend establishing an emergency plan in the event of a proven cyberattack.
This kind of plan helps guide employees on what to do, and how to react.
A crisis plan details a number of elements such as :
- How to guide employees on what to do, and how to react.
- What to do with the infected system, its isolation, repair, etc.
- What are the causes of the incident ?
- Has data been lost ? If so, are they present in the backup made recently ?
- Has data been stolen ? If so, is the data confidential and personal? In this case, you must inform the CNIL quickly.
- Was there a ransom demand ? If yes, take into account that the French government does not recommend paying the ransom, because you have no guarantee to find your data.
All these details need to be detailed in an emergency plan so as to be ready in the event of a possible incident, and to warn employees.
Bonus : Outsource your Security Operations Center
The Security Operation Center (SOC), designates within an IT cell, the team in charge of ensuring the protection and sustainability of all the elements that make up your information system (IS).
The aim of the SOC is to detect, analyze and remedy cybersecurity problems and incidents, using technical and technological solutions as well as a range of methodologies and know-how.
When you call on the SOC by ZIWIT, you’re guaranteed the support of specialized, complementary teams, available 24/7.
Our experts are equipped with the most powerful tools on the market to ensure your cybersecurity.
SOC by ZIWIT enables you to optimize your cybersecurity management by structuring it around proven technical and operational processes.
