Accountants & Chartered Accountants – Valuable prey for Cybercriminals
Discover how cybercriminals are taking advantage of digitalization to attack accounting professions.
With the advent of digitalization, the profession of accountant and chartered accountant has undergone significant change and transformation.
The COVID-19 period has accentuated this change through telecommuting and the use of cloud-based tools.
This exponential increase in the use of digital technology in the accounting world has led to a de facto increase in risks and cyber-attacks.
Accounting data is particularly attractive to cybercriminals, as it can be used to commit financial fraud, such as identity theft, money laundering or terrorist financing.
In this blog article, we will see how cybercriminals are taking advantage of digitalization to attack accounting professions.
Accounting professions : between change and handling confidential data
Digital technology is revolutionizing the accounting profession. New technologies make it possible to automate numerous tasks, increase efficiency and offer new services.
The main developments in the accounting profession
Task automation
Online accounting software can automate many tasks, such as :
- Registration of invoices.
- Preparation of tax and social declarations.
- Payroll management.
This enables accountants to be more productive and concentrate on higher value-added tasks.
Dematerialization of documents
Document dematerialization enables accountants to work remotely and share information more easily with their customers. This means greater flexibility and lower costs.
Data analysis
Accounting data can be used to analyze a company’s performance. In this way, accountants can help their clients make better strategic decisions.
Use of confidential data
Accountants have access to confidential data, including company financial information, customer personal data and strategic information. This data is protected by professional secrecy, which is a legal obligation.
The use of confidential data by accountants is governed by several rules:
- The accountant is bound by professional secrecy. He may not divulge this information to anyone, unless required by law or authorized by the client.
- The accountant must use this information solely for the purposes of his work. He may not use it for personal purposes or to gain an advantage.
- The accountant must take security measures to protect this information. It must use data protection software and secure storage systems.
The hacker’s goal: data theft
Theft of accounting data is a frequent occurrence, and can have serious consequences for companies and their customers.
Cybercriminals use a variety of methods to steal accounting data. They may use malware, phishing attacks or brute force attacks. They can also exploit vulnerabilities in corporate IT systems.
In 2022, consulting firm PwC estimated that 43% of companies had suffered a data breach in the previous year. Of these breaches, 20% involved accounting data.
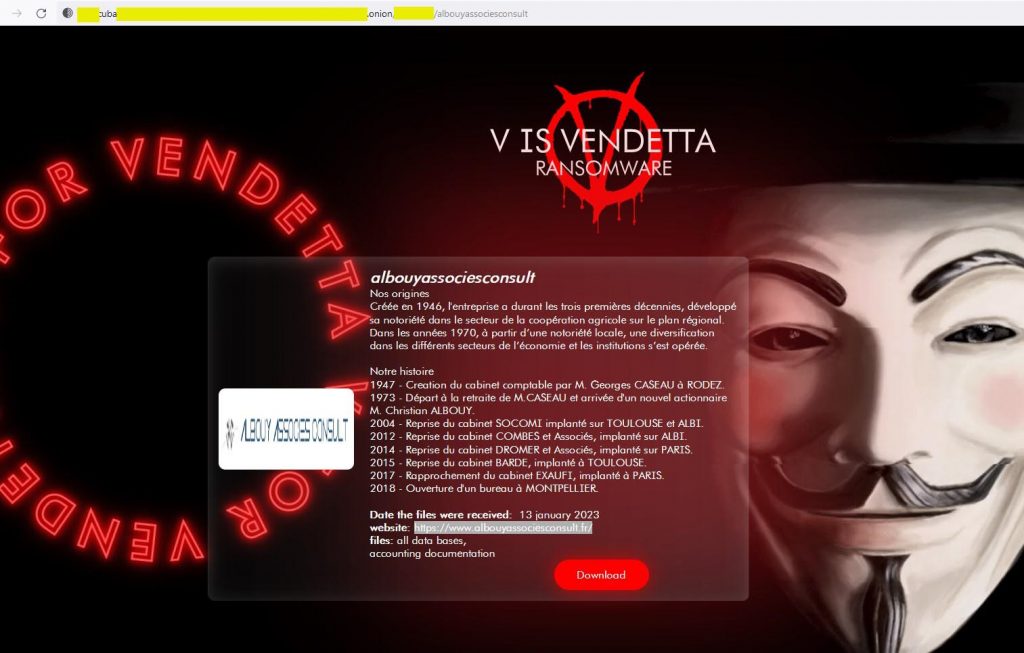
A recent example of data theft from an accounting firm
On December 29, 2022, the Center for Documentation and Studies on Risks (CDER) announced that it had suffered a data breach.
Cybercriminals gained access to a CDER server and stole sensitive data, including:
- The names, addresses, telephone numbers and email addresses of more than 100,000 people.
- CDER employee login information.
- Financial data, such as bank account numbers and credit card information.
CDER stated that the stolen data did not include any sensitive medical or personal information. However, those affected have been advised to take precautionary measures, such as monitoring their bank accounts and updating their passwords.
Those affected by the CDER data breach have been asked to take the following actions :
- Monitor their bank accounts and credit cards for possible fraudulent activities.
- Update their passwords for all their online accounts.
- Be vigilant against fraudulent emails and phone calls.
The consequences of data theft
Accounting firms store sensitive data, such as bank account numbers, credit card information, and client identification details.
Consequences for the firm
In the event of data theft, an accounting firm may suffer:
- Financial penalties: In France, breaches of data protection laws can result in fines of up to 4% of the company’s worldwide annual sales. In some cases, company executives can also be sentenced to prison terms.
- Loss of confidence: Clients may lose confidence in an accounting firm that has been the victim of data theft. This can lead to a loss of clients and revenue.
- Repair and recovery costs: An accounting firm may have to invest in additional security measures to protect its data. It may also face repair and recovery costs in the event of financial fraud.
- Data recovery costs: In many cases, when data is stolen, cybercriminals demand a ransom from the company and threaten to disclose it if it does not pay within the requested deadline.
Consequences for customers
In the event of data theft, clients of an accounting firm can suffer from:
- An invasion of privacy: Sensitive customer data, such as bank account numbers and credit card details, can be used by cybercriminals to commit financial fraud.
- The risk of financial fraud: Cybercriminals can use stolen data to open new bank accounts, make online purchases or even withdraw money from customers’ bank accounts.
Consequences for employees
In the event of data theft, employees of an accounting firm may suffer:
- An invasion of privacy: Sensitive employee data, such as their social security numbers and health information, can be used by cybercriminals to commit fraud or blackmail.
- The risk of losing your job: In the event of financial fraud, employees can be fired or prosecuted.
Types of cyberattacks to steal accounting data
Phishing attacks
Phishing is a cybercrime technique that involves sending fraudulent emails or SMS messages that appear to come from a legitimate source, such as a bank or company.
These emails or SMS messages usually contain a link or attachment which, when clicked or opened, installs malware on the victim’s device.
This malware can then be used to steal data, such as passwords, credit card information, or credentials.
This type of technique is increasingly used, so much that in 2022, phishing attacks increased by 61% compared to the previous period.
Malware
Malware is a computer program designed to harm computer systems.
They can be used to :
- Steal data.
- Damage files.
- Take control of a computer.
Malware can be installed on a device in a variety of ways, such as via email, download, or infection via a security hole.
Email detour and RIB fraud
In recent years, one fraud has become very popular with accounting firms and their clients: RIB alter fraud.
There are two ways to proceed:
- Hacking into a customer’s or accountant’s mailbox, for example. Cybercriminals will then intercept the emails and replace the beneficiary’s RIB with their own bank details.
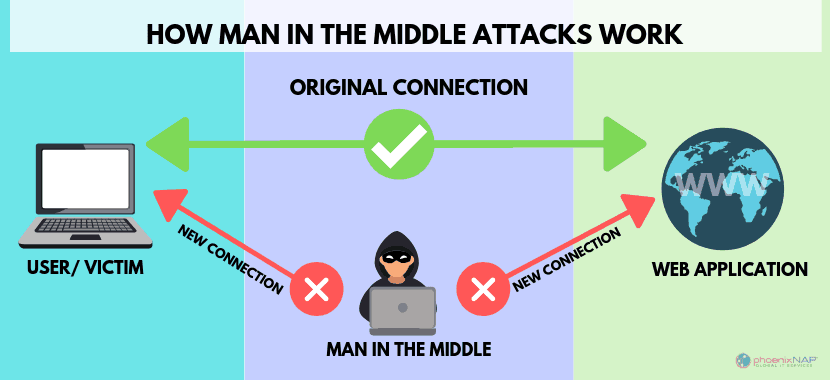
- The second is called “Man in the Middle”. Fraudsters will intercept email exchanges between the customer and the accountant, enabling them to modify the attachments, including the RIB. The hackers rely on high-performance bots, which can scan and detect emails looking for RIBs and replace them.
The Brute Force attack
Brute Force attacks are repeated attempts to guess a password.
They can be used to access password-protected computer accounts.
Cybercriminals can use automated tools and bots to carry out Brute Force attacks.
Protect yourself from data theft and cyberattacks
Whether it’s for prevention, or after the damage has been done, good cybersecurity practices and reflexes are essential.
Prevention
Here is a list of good practices and measures to take to avoid the risk of cyberattack as much as possible:
- Use vulnerability detection software such as a vulnerability scanner.
- Regularly update all the software you use, whether it is email, file sharing software, search browsers or accounting software.
- Use Cyber Threat Intelligence software or solution. These solutions will alert you if your data is detected on the Dark Web.
- Reinforce your passwords and never use the same one for all your different uses.
- Choose your software carefully. They must be renowned for their data protection and security.
- Train your associates and colleagues in Phishing techniques with a personalized Phishing campaign.
- In the same vein, always check the recipients of your emails and avoid transmitting confidential information as much as possible.
- Make backups of your data very often on external and very secure servers.
- Separate personal and professional uses.
- Do not host professional data on your personal equipment (USB key, telephone, etc.). Avoid connecting personal removable media to company computers.
- Carry out a Pentest of your information system with PASSI certified professionals to test it.
Reaction
If you have suffered a cyberattack, don’t panic. We’ll take you through the steps you need to take to respond appropriately.
To start with, we strongly advise you to call on the services of a professional Incident Response Team, which is an emergency unit in the event of a cyberattack.
Next, here is a list of measures we advise you to take:
- If a machine is affected, disconnect it from the Internet and all possible networks, but above all, do not switch it off!
- Gather as much evidence as possible so that you can later lodge a complaint.
- Keep the hard disks or make a complete copy of the data before it’s too late.
- Identify anything that has been destroyed or copied. If your data is confidential, you must inform the CNIL. Failure to do so may result in a fine.
- Contact your server host to take the appropriate measures.
- Once the threat has been eliminated and the machine has been secured, correct the flaw. For this, we advise you to call in the professionals.